Our researchers recently picked up on a spike in SPAM activity directed at sites powered by WordPress, which, naturally, led them to take a closer look.
Turns out the attack was launched by a botnet and implemented in the form of comment SPAM – meaningless, generic text generated from a template and posted in the comment sections of blogs, news articles etc; linking to pay-per-click commercial or suspicious sites looking to scam you or phish for your passwords.
Sifting through the comments we began to see a pattern – the linked sites offered betting services on 2018 FIFA World Cup matches.
How did they do it?
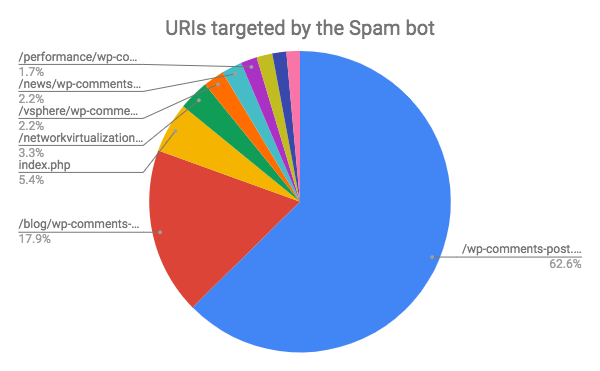
The SPAMbots mainly targeted WordPress sites using the “Spray and Pray” technique – attempting to post a comment to the same URI across different sites, regardless of whether the site is vulnerable or if it even has a comment section.
The payload used by the SPAMbot is a simple list of parameters whose values vary between each request. The following payload, for example:
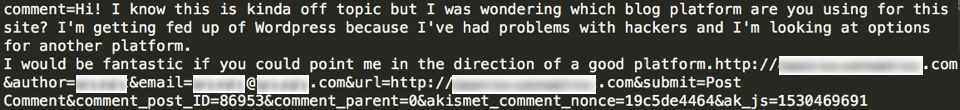
Under the right circumstances, the text above can be resolved to produce the following comment:
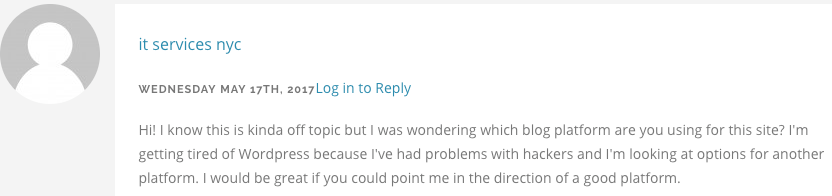
Of course, this comment didn’t appear on any Imperva protected website, we blocked them all; we found it in an online search.
The comments used by the botnet have been around for more than half a decade, tracing back to 2013 when a gist was published with the comment SPAM template. Searching any part of the non-varying text in the template yields tens of thousands of results, showing how widespread it is.
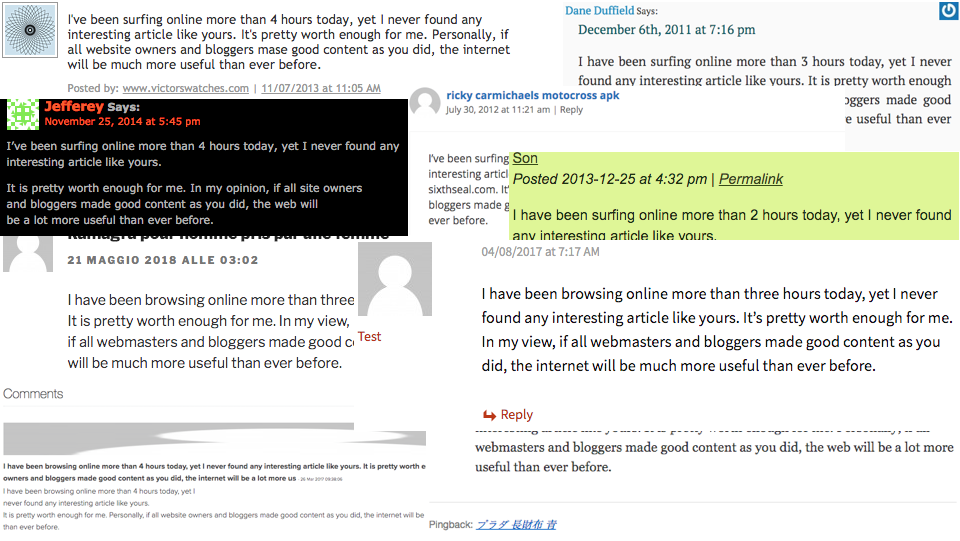
Our analysis found that the top 10 links advertised by the botnet lead to World Cup betting sites. Interestingly, eight of the top advertised sites contained links to the same betting site, hinting that they might be connected in a way.
We found that the botnet advertised over 1000 unique URLs, most of them appear multiple times. In many cases, the botnet used different techniques such as URL redirection and URL-shortening services to mask the true destination of the advertised link.
SPAMbot activity
We tracked down the botnet consisting of more than 1200 unique IPs, with up to 700 daily unique IPs, and monitored their behavior:
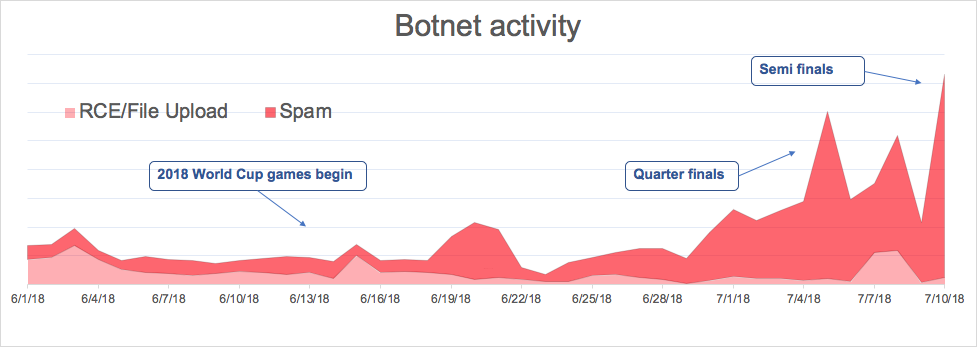
In the weeks before the World Cup, the botnet has emphasized other, non-SPAM attacks, including unsuccessful attempts to invoke Remote Code Execution (RCE) via PHP and to abuse Unrestricted File Upload to WordPress sites.
Once the matches began, the botnets rapidly decreased their violent behavior and increased their comment SPAM activity, peaking at the quarter-finals and semi-finals, possibly indicating that the botnet owner shifted his activity towards, what might be, a more valuable channel at the moment – World Cup betting sites.
A possible explanation is that the botnet is for hire. The malicious activity we’ve seen at first was either paid for or simply the botnet’s attempt to grow itself. Then, it was hired by these betting sites to advertise them and increase their SEO.
Stop SPAM and carry on
Although comment SPAM has been with us for more than a decade — and doesn’t seem like it’s going away anytime soon — there are numerous solutions ranging from dedicated plugins that block comments that look SPAMmy, to WAF services.
Imperva utilizes multiple SPAM protection tools, including:
- Identification of SPAMming IPs
- Classification of SPAM tools and botnets
- Detection of URLs advertised in comment SPAM
Defending against cyber threats requires an in-depth understanding of the cybersecurity landscape coupled with experience dealing with known threats and the dexterity to identify and defend against new ones. So, find a solution that fits your needs and protects your website; make sure not to miss the next World Cup match, and try not to bet on it through a suspicious site you sourced from a blog post comment…
Try Imperva for Free
Protect your business for 30 days on Imperva.

















