TL;DR
Imperva Threat Research discovered and reported a security flaw in the CoCalc Cloud environment. The flaw enabled potential attackers to completely take over a target’s account with only a single click from the victim. This flaw was due primarily to the lack of separation between the user environment and the space where untrusted user files could be executed.
In this blog post, we will see this attack in detail, show what led to this issue, and explain how to prevent it from happening in your applications.
The CoCalc team took action and fixed the bug after the report.
Security in Cloud Platforms
Cloud platforms help manage documents, resources, and even executable files. They sometimes allow you to share or make them public with your contacts. Due to their versatility, cloud platforms often present a larger attack surface than typical applications.
Securing all potential entry points in their architecture can represent a challenge, and companies like Google sometimes opt for BugBounty competitions that engage the community to enhance the security of these complex applications.
RMarkdown files
RMarkdown is a file format that merges the Markdown language (used for creating simple, readable documents with text formatting) with R, a programming language known for statistical computing and data visualization. This combination allows for creating dynamic documents where live code can be executed and its results, such as graphs or analysis outputs, can be displayed directly alongside explanatory text. The powerful capabilities of this file type extend to HyperText Markup Language (HTML).
CoCalc enables users to generate those file types, publish them, and share them. This is the functionality we’ll exploit here.
Explanation of the Flaw
Below is a flow chart explaining the vulnerability:
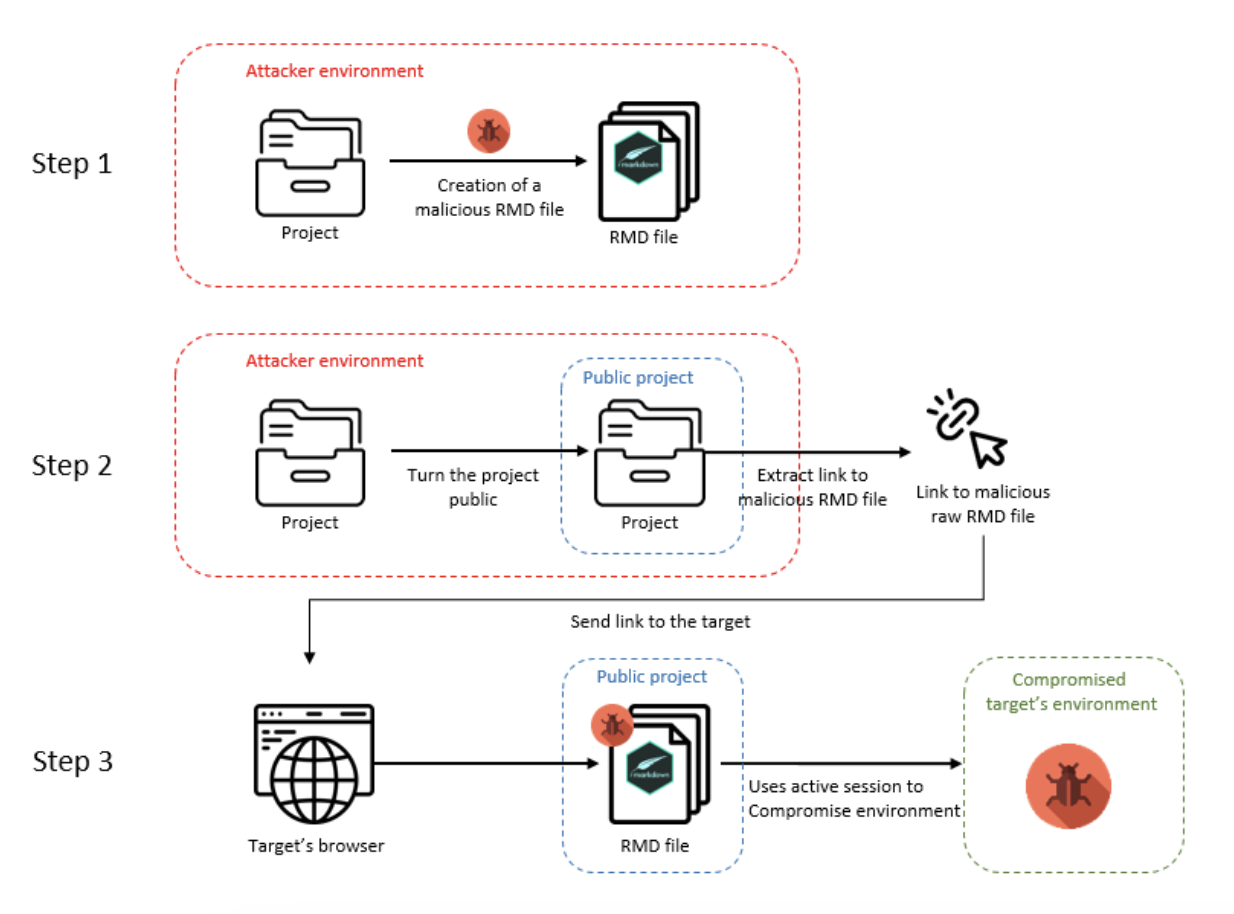
As shown above, the attacker can compromise the target’s environment in several steps:
- Step 1
- The attacker creates a project
- The attacker crafts a malicious RMarkdown file in a dedicated project
- Step 2 :
- The attacker turns their project public
- Then, they extract the raw URL of the malicious RMarkdown file
- Step 3 :
- The attacker sends the link to an unsuspecting target in order to take over their environment
- The target clicks on the link using his usual browser
- The malicious RMarkdown file gains access to the target’s active session
Finally, the malicious file controls the user’s environment via internal APIs.
This security vulnerability arose from the combination of several factors:
- The capability to create a document that could execute JavaScript;
- The absence of a clear separation between the user’s management environment for the cloud and the environment where untrusted user files are rendered; and,
- Any user can forcibly share an untrusted raw file with any other user.
This created a pathway for a potential stored Cross-Site Scripting (XSS) attack. Consequently, a single click by the victim could compromise their cloud environment.
Exploitation
An attacker can exploit this vulnerability by network requests sent to the backend server–for example, via the JavaScript fetch function. In our case, those requests will automatically include the victim’s session cookies, which will be fulfilled.
As a demonstration, we created a video showing how an attacker could insert a malicious file inside a target project using the internal /<project_id>/raw/.smc/upload endpoint.
Conclusion
In web application security, preventing XSS is still a major concern. A robust method to defend against this attack is implementing a Content Security Policy (CSP). CSP acts as a gatekeeper by establishing rules for allowable content, thereby preempting the execution of harmful scripts.
In addition, segregating executable and interpreted files into a separate domain presents an extra layer of protection. This technique effectively isolates any risky scripts, ensuring they don’t compromise the security of the primary web application, thanks to the Same Origin Policy.
Imperva CSP enables monitoring of your third-party dependencies, and can identify data exfiltration due to a stored XSS attack. Imperva WAF also provides robust protection against a wide range of XSS attacks.
Try Imperva for Free
Protect your business for 30 days on Imperva.