The new European Union (EU)-wide General Data Protection Regulation (GDPR) was signed into law in late April 2016, and the compliance deadline came into effect on May 25, 2018. The Regulation is expansive and covers a variety of subject areas, provisions, and actions in the form of documented Articles, with the more specific data security rules and requirements being contained within four Articles (32-35) of the regulation, and unpacked in this blog.
A key question for many organizations remains – what processes and technologies are required to help ensure compliance with these data security Articles, and how can they be leveraged to ease the burden of achieving and maintaining compliance?
In the first blog of this series, we focused on how Imperva Data Security and specifically the Imperva SecureSphere solution can be easily and effectively configured to support data discovery and classification in accordance with GDPR, and specifically with Article 35 (Data Protection & Impact Assessment). We outlined how the solution can now leverage out-of-the-box GDPR scanning and classification capabilities to make the completion of this critical process quick and easy.
In the second blog, we switched gears and took a look at Article 32 (Security of Processing), and how the Imperva Camouflage data masking solution can be leveraged to support data minimization and compliance efforts by delivering pseudonymized data via pre-configured GDPR discovery and de-identification capabilities. Now, in the third and final blog in this series, we will focus on how Imperva SecureSphere can support advanced adherence to the broad requirements of Article 32 (and overall long-term GDPR and data security compliance) with the various monitoring and auditing tools afforded by the solution.
(Also, check out the whitepaper from the Ovum research team, “A Buydown for Risk: Why Data Security is a Must,” where you can learn how to deploy a data security strategy that better protects your most vital asset than core or edge security will.)
Leveraging Imperva SecureSphere to Support Compliance with Article 32
While there is flexibility and some grey area with respect to complying with Article 32, it is clear that doing so will require both organizational process change and various data security technologies. Organizational strategies are similar to those specified for Article 25 compliance, and, while not an exhaustive list, the following technical strategies and technologies will likely form part of your compliance plan:
- Data discovery and classification
- Data loss prevention processes and technologies
- Data masking technologies
- User rights and privileged user database access and activities
- Secure audit trail archiving
- Sensitive data access auditing
Imperva SecureSphere supports the majority of the required process and technology changes as it identifies and classifies sensitive data, monitors data access and identifies suspicious events; providing detailed real-time results of the what/where/when related to incident findings, and leverages advanced machine learning to prioritize truly worrisome incidents. On-demand reporting ensures you can provide information within the required GDPR reporting deadlines.
In the first blog we looked at how to effectively configure SecureSphere to support the data discovery and classification requirements leveraging new out-of-the-box profile for GDPR. Now, we will dive deeper and outline how SecureSphere can also be leveraged to support access and activity monitoring, and ongoing audit and vulnerability monitoring activities- which are both critical to the ongoing and long-term compliance success efforts required of all organizations impacted by GDPR.
To that end, let’s summarize the step-by-step configurations within SecureSphere that will allow you to quickly and easily leverage the solution to monitor access to personal data, monitor data transfers, and raise alerts in the event of personal data access- all of which are critical in terms of offering further support of Article 32 compliance, and long-term data security within your organization.
Once you’ve leveraged SecureSphere to identify the location of all databases within the organization, and also the classification of all personal data within them, you can now easily set up “policies” within the solution to (I) monitor access to personal data, (II) monitor transfers of personal data to locations outside of the EU, and (III) raise alerts as a result of access to personal data.
Let first look at how to set up the applicable policies.
Monitoring access to personal data
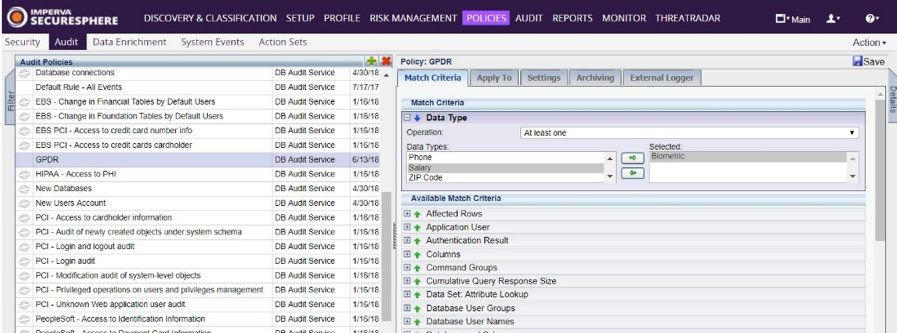
In order to audit access to personal data, you must create a DB audit policy and apply it to the relevant databases. To do so, simply follow these steps within SecureSphere:
- In the Main workspace, select Policies > Audit.
- In the Audit Policies pane, Click the New button.
- From the ddrop-downlist, select DB Service. The Create New Database Policy dialog box appears.
- Type a Name, say, GDPR, and click Create.
- Select the new policy.
- Under the Match Criteria tab, click the green arrow by Data Type and expand it.
![]()
- Select all the data types that contain personal data.
- Under the Apply to tab, select the databases that you want to monitor.
- Click Save.
Monitoring data transfers
While the focus of this blog is on Article 32, there is much overlap in terms of the Articles that SecureSphere supports, and the monitoring of data transfers is one example. Article 44 of the GDPR prohibits the transfer of personal data beyond EU/EEA, unless the recipient country can prove it provides adequate data protection. SecureSphere supports both Articles in this regard, and can be easily configured to support adherence. Let’s review how this can be achieved.
In order to audit access to personal data and activity associated with potential transfers and other activities, you create a DB audit policy and apply it to the relevant databases. To do so, first create a global object that has a list of EU IP addresses. Then, create a DB audit policy that will generate a match when an IP address in the monitored traffic is not in the list defined by the global object.
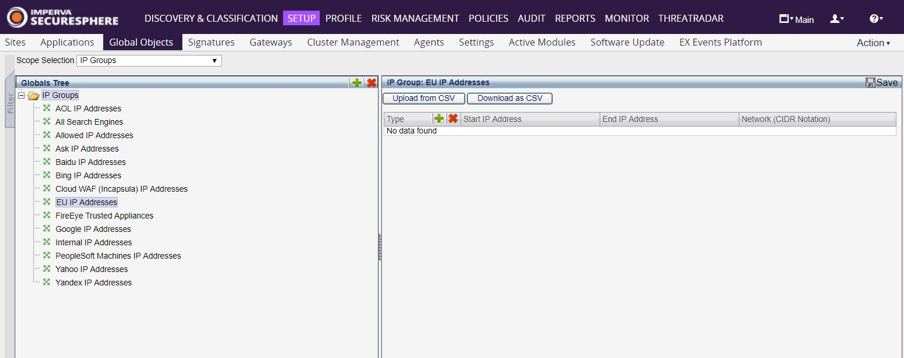
So, to create a global object with EU IP addresses, simply follow the following steps:
- In the Main workspace, select Setup > Global Objects.
- From the Scope Selection drop down list, select IP Groups.
- Click the New The Create IP Group dialog box appears.
- Type a Name, say EU IP Addresses, and click Create.
![]()
- In the Global Tree, select the new IP Group.
- In the details pane, click Upload from CSV. The CSV Upload dialog box appears.
- Click Browse, navigate to the file containing the EU IP addresses, select it and click Upload.
- Click Save.
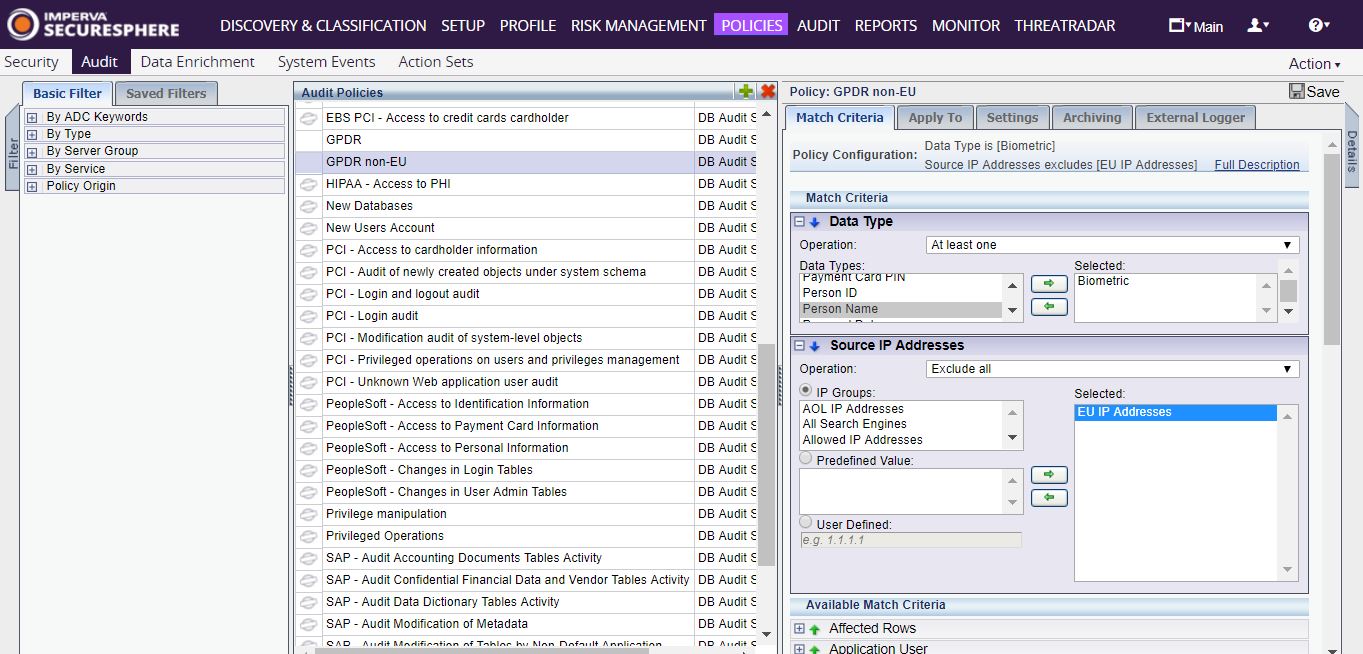
Now, to create a DB audit policy that monitors the transfer of personal data to non-EU locations:
- In the Main workspace, select Policies > Audit.
- In the Audit Policies pane, click the New Button
- From the drop down list, select DB Service. The Create New Database Policy dialog box appears.
- Type a Name, say, GDPR non-EU, and click Create.
![]()
- Select the policy.
- Under Match Criteria, click the green up-arrow by Source IP Addresses. Expand it.
- Under the Operation drop down list, select Exclude.
- Under IP Groups, select the global object you created, in this case, EU IP Addresses, and click the green right arrow.
- Under the Match Criteria tab, click the green arrow by Data Type and expand it.
- Select all the data types that contain personal data.
- Under the Apply to tab, select the databases which you want to monitor.
- Click Save.
You can then easily view the results of your audits by running and viewing a report from the main workspace. This applies to both GDPR audits:
- the audit for access to personal data
- the audit for transfer of personal data to non-EU locations
Raising alerts when sensitive data is accessed
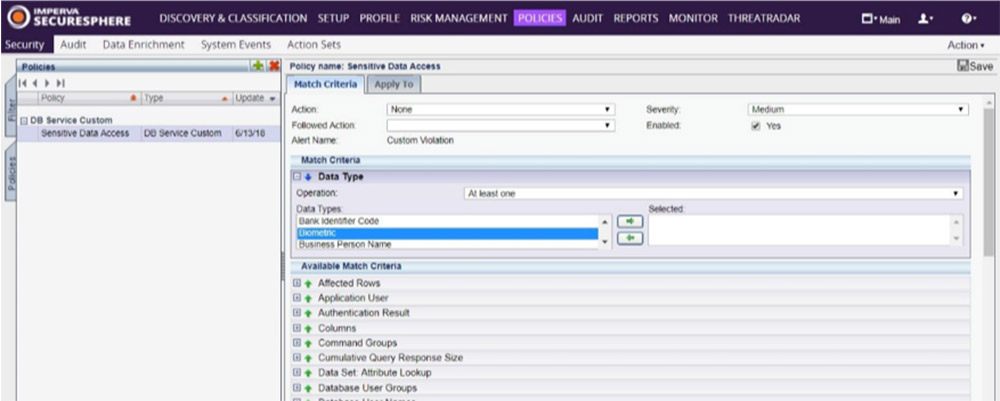
To raise an alert when sensitive data is accessed, you need to create a DB service custom security policy in the main workspace as follows:
- In the Main workspace, select Policies > Security.
- In the Policies pane, click the New button.
- From the drop down list, select DB Service. The Create New Policy dialog box appears.
![GDPR34]()
- Type a Name, and from the Type drop-down list, select DB Service Custom. Click Create. The new policy is now created.
- Select the new policy.
- Under the Match Criteria tab, click the green arrow by Data Type and expand it.
- Select all the data types that contain personal data.
- Under the Apply to tab, select the databases that you want to monitor.
- Click Save.
So, SecureSphere enables you to find out when sensitive data is accessed by setting security policies that will raise alerts when they detect that sensitive data is accessed. Further, SecureSphere’s profiling technology learns over time the legitimate behaviors of application and database traffic, creates a profile based on this behavior- and then raises an alert when this profile is breached.
Ongoing GDPR Compliance and Investigative Support
Now that you’ve set the appropriate monitoring and alert provisions within SecureSphere, you can next look at the longer term vulnerability and assessment capabilities of the solution and how these support ongoing compliance and breach prevention/notification.
Imperva SecureSphere’s ADC (Application Defense Center) has a preconfigured GDPR assessment scan that can (and should) be run regularly to help uncover any vulnerabilities, risks, and potentially serious compliance issues. This is a tag-based scan that is associated with the assessment policies that are relevant for GDPR, i.e., CIS, DISA, and known vulnerabilities. The ADC simply tags these policies with the tag GDPR.
To run the GDPR assessment scan, simply follow these simple steps:
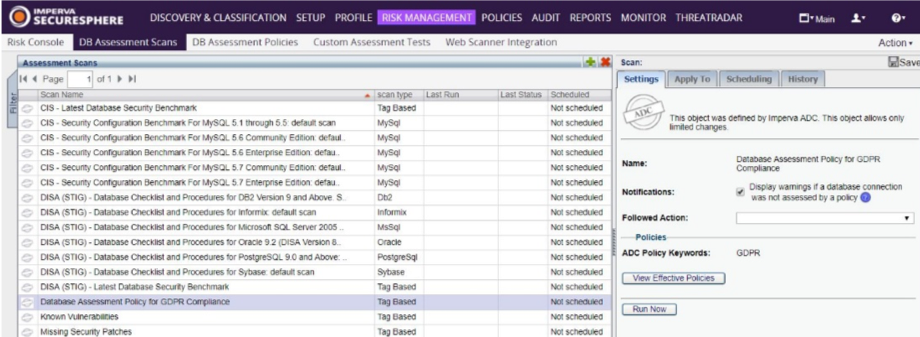
- In the Main workspace, select Risk Management > DB Assessment Scans.
![]()
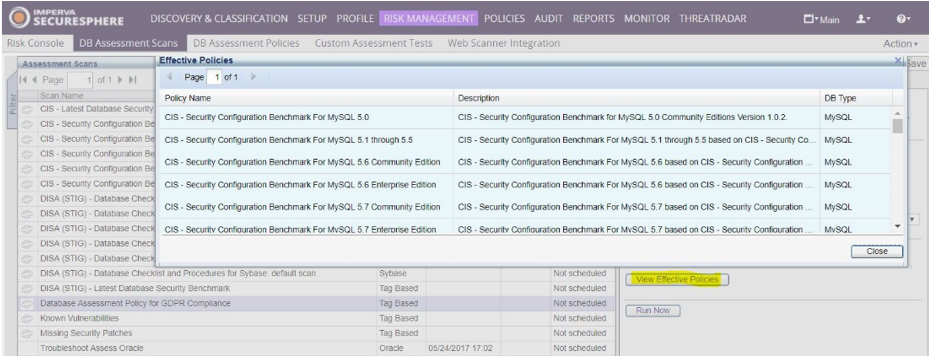
- Under Assessment Scans, select Database Assessment Policy for GDPR Compliance. You can view the effective policies used by this tag-based scan by clicking on the View Effective Policies button under the Settings tab
![]()
- Click the Apply to tab. Select the databases you wish to scan.
- Click the Scheduling Select your scheduling choices. You should schedule regular scans since tables may be added frequently.
- Click Save.
By running SecureSphere’s database assessment scans, you can reduce your exposure to security threats by discovering security vulnerabilities over the long-term. You can then take appropriate steps to fix these vulnerabilities and thereby support ongoing compliance efforts, while at the same time providing valuable insights to help prevent data breach events (and resulting reporting requirements).
A Complex Challenge- Supported with a Comprehensive Solution
GDPR Article 32 clearly mandates that those handling data introduce appropriate technical and organizational measures to secure the data, and we’ve highlighted in this three part blog series how Imperva Data Security conducts a variety of critical data security processes required to support ongoing compliance. It starts with discovery and classification of personal data, and the potential for de-identifying data copies using data masking technology. Further, as outlined in this technical blog, Imperva SecureSphere also identifies security holes in your databases and assesses vulnerability; tracks and manages vulnerabilities and prioritizes remediation efforts; audits sensitive data by monitoring who is accessing what data in real time; and prevents data theft from external attacks and insider threats by monitoring data access activity.
In addition, SecureSphere can control the use and transport of data with ongoing data discovery and classification, and policies that inspect database traffic and alert to potential violations- like those outlined within the data transfer provisions within the GDPR. Clearly, there are a variety of significant data security process requirements within GDPR that require comprehensive and robust technology solutions to help speed compliance efforts and reduce the organizational burden, particularly for those organizations that have yet to fully comply with GDPR.
Contact us to learn more about Imperva’s GDPR compliance capabilities and explore our data security solutions in detail.
More on the GDPR:
- GDPR Series, Part 1: Does the GDPR Apply to You?
- GDPR Series, Part 2: What Rules Require Data Protection Technology?
- GDPR Series, Part 3: Preparing Your Organization for the GDPR
- GDPR Series, Part 4: The Penalties for Non-Compliance
Try Imperva for Free
Protect your business for 30 days on Imperva.