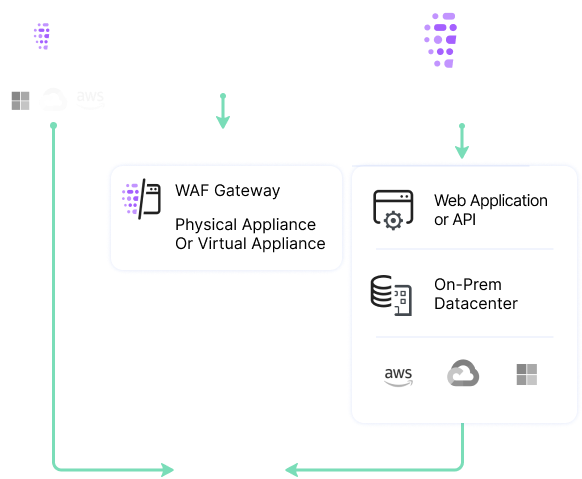
Reduce false positives with Imperva Web Application Firewall
Protect without WAF false positives
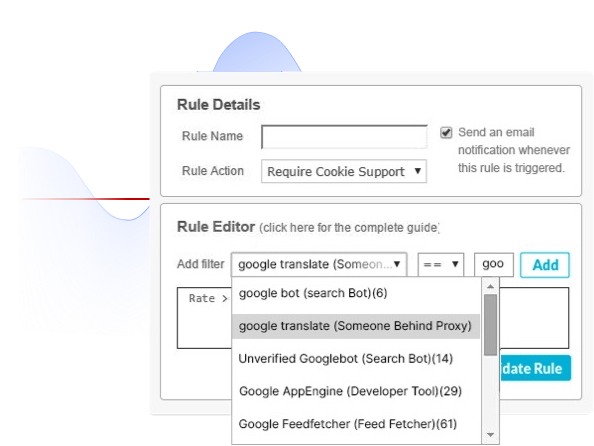
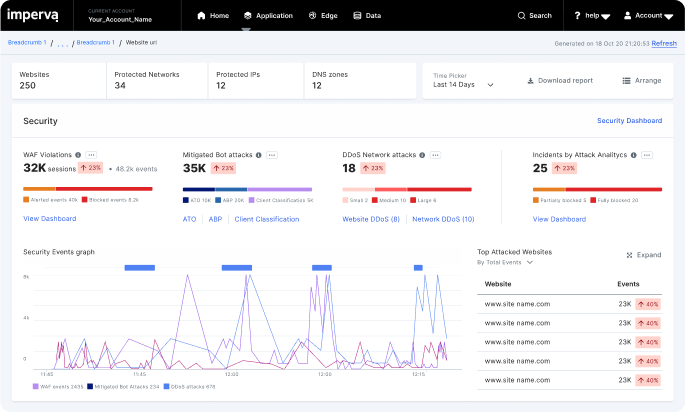
False positives forces a choice between blocking legitimate traffic or staying in monitor mode forever. Imperva Research Labs ensures precision for customers, giving them confidence to block as the threat landscape evolves.
90+%
of our customers deploy in blocking mode
WAF security automations
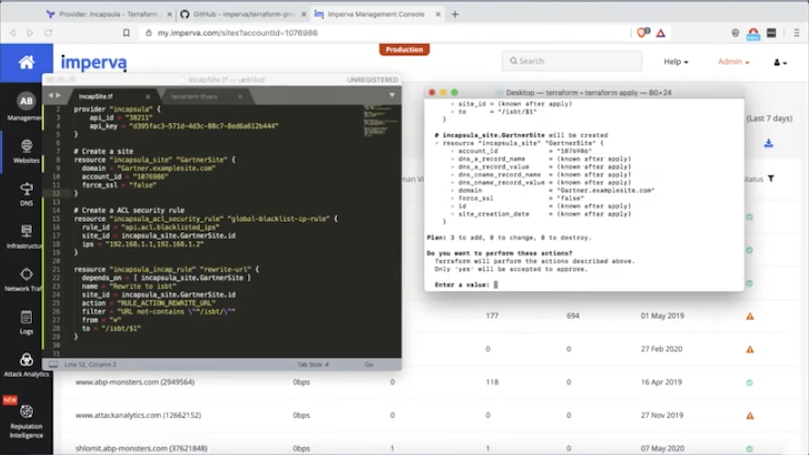
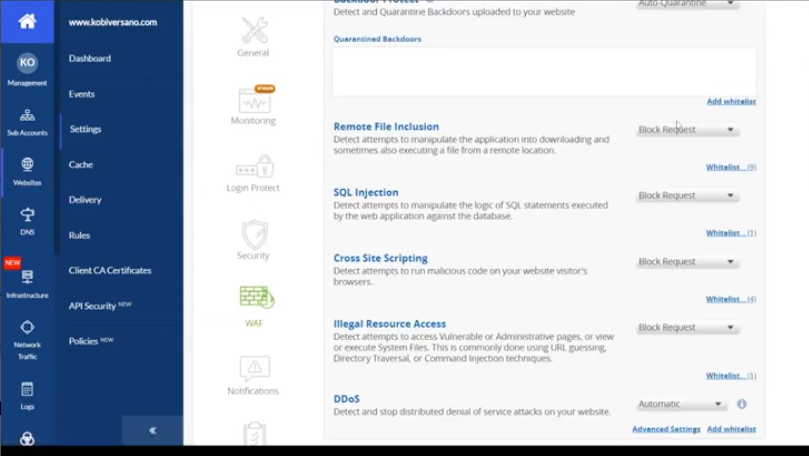
Automatic policy creation and fast rule propagation empower your security teams to use third-party code without risk while working at the pace of DevOps.
70+%
of a web app is risky third-party code