What is UEBA
User and Event Behavioral Analytics (UEBA) is a category of security solutions defined by Gartner in 2015. UEBA uses machine learning and deep learning to model the behavior of users and devices on corporate networks. It identifies abnormal behavior, determines if it has security implications, and alerts security teams.
UEBA improves on older security tools, which would identify security incidents using statistical analysis and predefined correlation rules. These methods were effective for known threats, but did not work well for unknown attacks and insider threats (which appear to be similar to regular user activity). UEBA can detect suspicious behavior with no predefined patterns or rules.
What is the Difference Between UEBA and UBA
Before the emergence of the current UEBA category, Gartner defined User Behavior Analytics (UBA) as a cybersecurity tool that analyzes user behavior on networks and on other computer systems. UBA applies advanced analytics to detect anomalies.
Later, Gartner updated its definition and created the new category User Entity and Behavior Analytics (UEBA) includes behavioral analysis of entities other than users, such as routers, servers, and endpoints. UEBA solutions are more powerful, as they can detect complex attacks across multiple users, IT devices and IP addresses.
Essentially, UEBA extends UBA by observing patterns and anomalies for other entities, such as network devices and servers, and not just individual users.
A major driver for the move from UBA to UEBA was the explosion of Internet of Things (IoT) devices, which generate huge amounts of sensor data. UEBA can analyze this data, looking at IoT devices individually or in peer groups, and identify suspicious behavior that may suggest malicious intent.
UEBA can also be used to monitor large numbers of cloud assets, which are provisioned dynamically and are used remotely, making them difficult to analyze with traditional security tools. UEBA can look at cloud-based assets and discover if, as a group, they are acting normally or abnormally.
How UEBA Works & Best Practices
A UEBA system collects data about user and entity activities from system logs. It applies advanced analytical methods to analyze the data, and establishes a baseline of user behavior patterns. UEBA continuously monitors entity behavior and compares it to baseline behavior for the same entity or similar entities, to detect abnormal behavior.
Baselining is key to a UEBA system, as it makes it possible to detect potential threats. The UEBA system compares the established baseline with current user behavior, calculates a risk score and determines if deviations are acceptable. If the risk score exceeds a certain threshold, the system alerts security analysts in real-time.
Three Pillars of UEBA
Gartner’s definition includes three primary attributes of UEBA systems:
- Use cases—UEBA solutions report the behavior of entities and users in a network. It detects, monitoring and alerting of anomalies. UEBA solutions need to be relevant for multiple use cases, unlike systems that perform specialized analysis such as trusted host monitoring, fraud detection, etc.
- Data sources—UEBA solutions can ingest data from a general data repository. Such repositories include data warehouse, data lake or Security Information and Event Management (SIEM). UEBA tools don’t place software agents directly in the IT environment to collect the data.
- Analytics—UEBA solutions isolate anomalies using analytic methods, including machine learning, statistical models, rules and threat signatures.
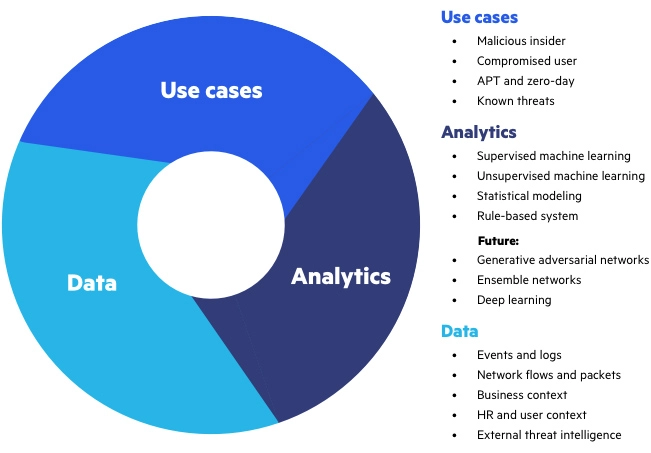
Three pillars of UEBA
UEBA Best Practices
Follow these best practices to successfully implement a UEBA solution:
- Consider both internal and external threats when creating new policies and rules.
- Ensure only relevant team members receive UEBA alerts.
- Do not consider non-privileged user accounts as harmless. Attackers commonly gain control of standard accounts and escalate privileges to penetrate sensitive systems. UEBA systems can help detect unauthorized privilege escalation.
- Do not treat UEBA processes and tools as a substitute for basic monitoring systems such as Intrusion Detection Systems (IDS). They should complement the traditional monitoring infrastructure.
UEBA & Big Data Security Analytics
Big data analytics lets businesses extract value from large volumes of unstructured, semi-structured or structured data. Within this field, big data security analytics focuses on applying advanced analytical techniques to security data, in order to detect threats more effectively and save time for security teams.
The following capabilities distinguish big data security analytics from traditional security tools:
- Scalability—analyzing and correlating current and historical security events across multiple organizational systems.
- Reporting and visualization—helping users understand complex data, slice and dice and easily create visualizations to extract insights.
- Big data storage—effectively storing massive quantities of data, processing and analyzing it using massively scalable systems like Hadoop or ElasticSearch.
- Context—framing data in relation to users, devices, and events. Data without this context is far less useful and can result in false positives.
- Broad functionality—using security data to detect a large variety of threats, and storing historical data to enable detection and investigation of future threats.
SIEM and UEBA
SIEM systems are a big data security analytics infrastructure deployed by many security organizations. SIEMs collect and aggregate data from security tools and IT systems, analyze it, and provide real-time alerts for security teams.
Traditionally, SIEMs did not include behavioral analytics technology—they discovered threats via user-defined correlation rules. UEBA solutions were developed to address this gap, and have proven to be very effective at detecting complex or unknown attack patterns.
In recent years, analysts and vendors realized advanced analytics can make SIEMs more effective at detecting and analyzing threats. As a result, many next-generation SIEM systems offer built-in UEBA solutions.
Imperva Data Protection Solutions
Imperva’s industry-leading data security solution provides user behavior analytics which establishes baselines of data access behavior and alerts on abnormal activity.
Our comprehensive approach relies on multiple layers of data protection, including:
- Database firewall—blocks SQL injection and other threats, while evaluating for known vulnerabilities.
- User rights management—monitors data access and activities of privileged users to identify excessive, inappropriate, and unused privileges.
- Data masking and encryption—obfuscates sensitive data so it would be useless to the bad actor, even if somehow extracted.
- Data loss prevention (DLP)—inspects data in motion, at rest on servers, in cloud storage, or on endpoint devices.
- Data discovery and classification—reveals the location, volume, and context of data on-premises and in the cloud.
- Database activity monitoring—monitors relational databases, data warehouses, big data and mainframes to generate real-time alerts on policy violations.
- Alert prioritization—Imperva uses AI and machine learning technology to look across the stream of security events and prioritize the ones that matter most.
Imperva protects data wherever it lives—on-premises, in the cloud and in hybrid environments, providing full visibility into how the data is being accessed, used, and moved.




