Imperva is setting TLS 1.2 as Incapsula’s default minimum TLS version to provide your users a more secured first hop. Learn what steps Imperva is taking, how this affects your site and users, how to remain PCI-compliant, and how to opt-out if needed.
TL;DR
PCI-DSS v3.2 compliance requires disabling the use of TLS 1.0 as of July 1, 2018.
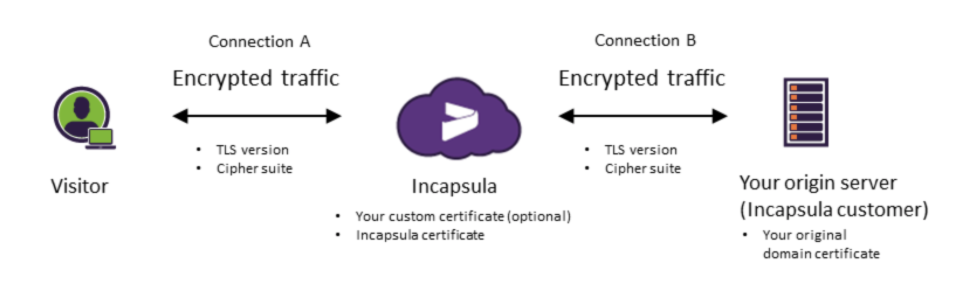
To comply with this requirement, and due to the known vulnerabilities in TLS 1.1, we are defining TLS 1.2 as the default minimum TLS version for connectivity between visitors and the Incapsula service (“Connection A”). Otherwise, leaving the responsibility of disabling the “dangerous” protocol version in the hands of the customer (which would be required to take action to remain compliant) leaves a hole in our security from the compliance perspective. The hop between the Incapsula service and the origin server is the compliance responsibility of the customer. The changes will take place on April 29, 2018, leaving a sufficient buffer for us and our customers to take action if needed. This change also applies to the Incapsula management console and the Incapsula API.
Enterprise and Business accounts that need to keep supporting TLS 1.0 and 1.1 may opt-out and continue to support all TLS versions. Pro accounts must upgrade to Business (or Enterprise) in order to opt-out. The 2018-03-11 release included the opt-out UI & API functionality.
Vulnerabilities in TLS 1.0 and 1.1
TLS 1.0 and 1.1 implementations are susceptible, in some cases, to vulnerabilities such as POODLE (CVE-2014-3566) which can potentially lead to exposure of personal data such as email addresses, passwords, and credit card numbers – the very things the TLS was designed to protect. Attackers with access to client or server environments can manipulate clients to use insecure SSL 3 connections. They then use SSL 3 weaknesses to extract sensitive data from the stream.
While the Incapsula WAF does protect your sites against POODLE and other application attacks, the PCI requirement does calls for the end of use of TLS 1.0. Although it is not yet required, PCI also recommends to stop using version 1.1, leaving us with the existing 1.2 and version 1.3 which is just around the corner.
We see that most of our customers’ visitor traffic consists of TLS 1.2 (>94%), and due to the known and potential weaknesses in 1.0 and 1.1, we recommend to stop using TLS 1.0 and 1.1. Additionally, over 80 percent of our customers have less than 5 percent of traffic from those earlier TLS versions; justifying that it’s time to retire TLS 1.0 and 1.1.
Client to Incapsula TLS Distribution (30 days)
| Version | Traffic Distribution |
| TLS 1.2 | More than 94% |
| TLS 1.1 | Less than 0.2% |
| TLS 1.0 | Just a tad over 5% |
| SSLv3 | Less than 0.0001% |
Customers First.
A few months ago, we set out on a mission to align with the new PCI TLS requirement while avoiding a negative impact on our customers’ traffic at all costs. This was and still is a cross-team effort involving all teams – product management, product development, support, technical account management, managed services, sales and more. We needed to plan a smooth transition process and provide the relevant tools and information to both our customers and our customer-facing teams.
To ensure a smooth transition we have provided an option to opt-out of the TLS enforcement per site. Opting-out is only possible on the new network, so if you’re not on it yet, we will move your site to a new IP on our new network platform. Additionally, we’ve automated most of these processes that will be required as part of the enforcement; such as DNS updates and certification re-validation. We’ve summarized the actions that we’ve taken:
- Proactively reaching out
We started contacting our customers in January 2018 to give them a heads-up. Customers that choose to opt-out will be contacted by our team to plan the transition to the new platform if needed. The notifications are being sent to both the account admin and the account notification list.
- Providing TLS visibility
Our support team is available 24/7 to provide any support you may need, including TLS version distribution statistics on your clients’ connections to Incapsula. This visibility can help you make an informed decision whether to opt-out and support all TLS versions or not.
- Opt-out checkbox (there’s also an API, don’t worry)
If you decide to opt-out, you can check the “Support All TLS Versions” checkbox in the management console (Account Settings and Site Settings). Selecting the checkbox in the site settings will either automatically move your site to a new IP or notify you if assistance from our Support team is required. This setting is also available by API. If you haven’t already done so, at this time we recommend that you prepare your customers/users, client applications, or any other tools to support TLS 1.2 only. Our Support team will contact you to coordinate the change to the new platform if needed. Should you wish to set TLS 1.1 as the default minimum, which is still PCI-compliant, first opt-out and then let our Support team know, and they will configure it for you.
- Moving your account to the new platform
After checking the opt-out checkbox, and if you’re currently not on the new platform, we will create another instance of your account on the new service platform. You can tell you’re on the new platform if you can see the Network Traffic Dashboard. The new instance will allow you to opt-out of the TLS default setting. Additionally, your new instance on the new platform will give you access to the Network Traffic Dashboard to explore your traffic metrics and DDoS attacks in real-time, or analyze up to 90 days back. Your current instance will remain live until you update your A record. - Automatic re-validation of your TLS certificates
If you opt-out, in most cases, your TLS certificates will be re-validated automatically without requiring any action on your side. If needed, we will proactively identify the certificates that require re-validation and we will reach out to you. The re-validation typically requires that you add the relevant authorization string in a DNS TXT record to be viewed by the CA. You will receive instructions on how to complete the revalidation.
Timeline for Migrating to TLS 1.2
January 24, 2018
We began distributing notifications to our customers.
Read the 2018-03-11 Release notes
March 11, 2018
An option to opt-out (per site) has been provided in the management console and API.
From the management console: Account level and Site level
Using the API: Account level and Site level
April 29, 2018 (Update: this date has been extended to May 27, 2018)
TLS 1.2 will be set as the default minimum TLS version for the connectivity between clients and the Incapsula service for all customers who have not already opted-out.
Incapsula will have an emergency process in place for customers who are impacted by this “default” change. The emergency process will allow you to revert back and re-enable support for TLS 1.0 and TLS 1.1 temporarily while we work with you to complete the opt-out steps. This solution will only be available until the PCI deadline.
July 1, 2018
PCI Deadline
All customers wishing to opt-out of TLS 1.2 enforcement must have completed the opt-out steps outlined below or will be impacted by the change.
Imperva is committed to the successful migration of all customers without disruption. Working together, we are confident that the process can be completed without any downtime.
Try Imperva for Free
Protect your business for 30 days on Imperva.