Just two months ago we published an analysis of a critical remote code execution (RCE) security vulnerability in Apache Struts. Now Apache Struts has published a new version fixing yet another critical RCE vulnerability (September 5, 2017). CVE-2017-9805 is a vulnerability in Apache Struts related to using the Struts REST plugin with XStream handler to handle XML payloads. If exploited it allows a remote unauthenticated attacker to run malicious code on the application server to either take over the machine or launch further attacks from it.
Imperva Customers Are Protected
In addition to our zero-day protection rules that spotted this attack, we’ve also published new dedicated security rules to provide maximum protection to Imperva SecureSphere and Incapsula WAF customers against this vulnerability. As of the publication date of this post, our systems have successfully blocked thousands of attacks from all over the world (see “In the Wild” section below).
Multiple Apache Struts Vulnerabilities in 2017
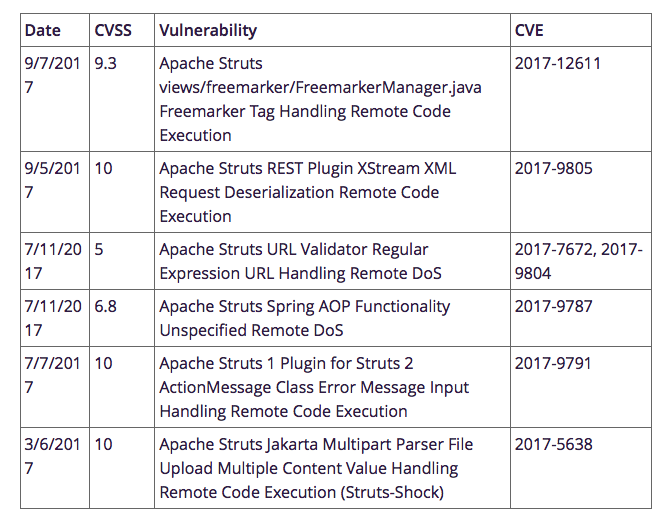
As mentioned above, this isn’t the first time such a critical vulnerability has been found in Apache Struts. In fact, we’ve seen an increasing amount of them in the Struts platform as several other RCE vulnerabilities have already been discovered since the beginning of 2017. The CVEs are summarized below.
About the CVE-2017-9805 Vulnerability
Apache Struts contains a flaw in the REST Plugin XStream that is triggered as the program insecurely deserializes user-supplied input in XML requests. More specifically, the problem occurs in XStreamHandler’s toObject () method, which does not impose any restrictions on the incoming value when using XStream deserialization into an object, resulting in arbitrary code execution vulnerabilities. More information about the vulnerability can be found here.
In the Wild
To date, our systems have successfully blocked thousands of attacks from all over the world with China, as usual in Apache Struts vulnerabilities, identified as the most prominent source of attacks (see Figure 1).
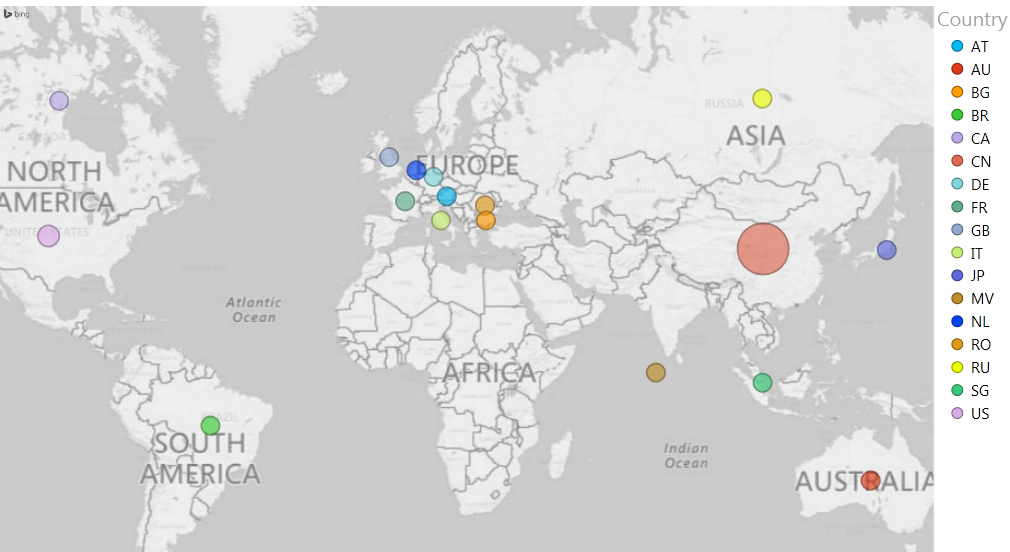
Figure 1: Geo-distribution of CVE-2017-9805 attacks
It is interesting to note that a single Chinese IP is responsible for more than 40% of the attack attempts that we registered. According to Shodan, this IP is registered to a large Chinese e-commerce company and runs an open SSH server which may indicate that this is a compromised machine. This machine tried to attack dozens of sites with different automated tools impersonating legitimate browsers such as cURL, wget, and Python-requests indicating the persistency of the attacker(s). Unlike past vulnerabilities, most of the attempted attacks (~80%) refer to exploitation attempts and only 20% refer to reconnaissance attempts to track vulnerable servers (see Figure 2). Exploitation attempts involved running operating systems such as shell, wget, or cURL in order to download malicious payload and take over the server to mount further attacks, usually DDoS, as part of a larger botnet.
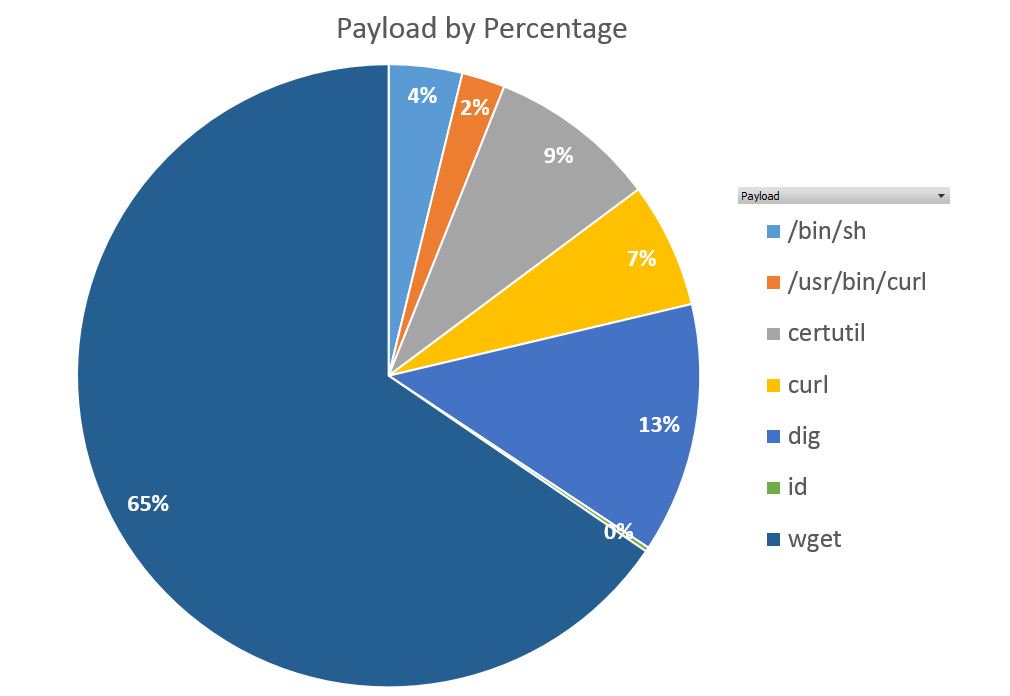 Figure 2: Percentage of payload types of CVE-2017-9805 attack attempts
Figure 2: Percentage of payload types of CVE-2017-9805 attack attempts
Stay Protected with Virtual Patching
Based on the official advisory, this vulnerability affects applications using Struts 2.5 (Struts 2.5.12). There is no known workaround, meaning that an update is required for those who use these versions. It is also mentioned that backward compatibility is not ensured and that some REST actions stop working.
An immediate security measure organizations can use to protect against these types of vulnerabilities is virtual patching. Instead of leaving a web application exposed to attack while attempting to modify the code after discovering a vulnerability, virtual patching actively protects web apps from attacks, reducing the window of exposure and decreasing the cost of emergency fix cycles until you’re able to patch them.
Learn more about virtual patching and protecting web applications from vulnerabilities using Imperva Incapsula WAF or Imperva SecureSphere WAF.
Try Imperva for Free
Protect your business for 30 days on Imperva.