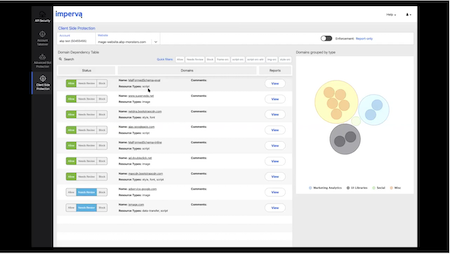
Client-side Protection
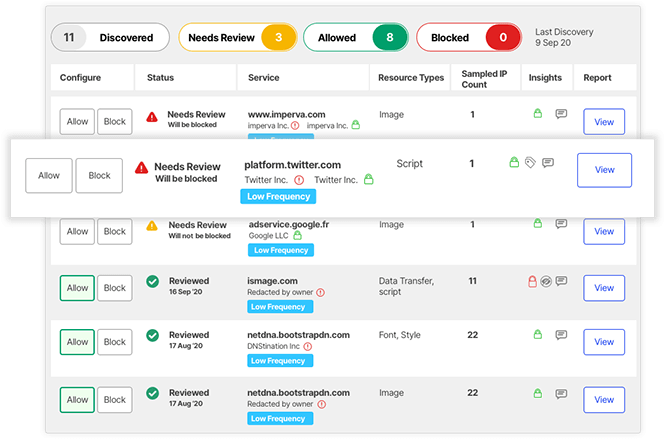
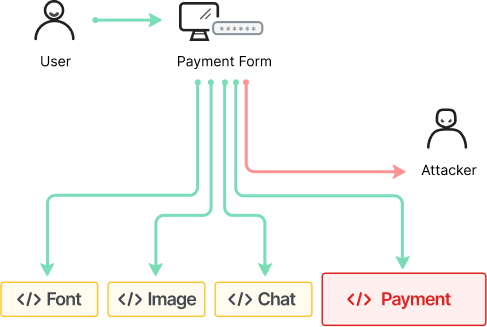
Client-side attacks increase as web applications shift to client-side logic and incorporate more third-party code and resources. These attacks can directly steal sensitive customer data, resulting in breaches and noncompliance with data privacy regulations. PCI DSS 4.0 has added new client-side security requirements addressing this growing threat. Imperva provides comprehensive visibility, actionable insights, and intuitive controls, enabling your security team to inventory client-side resources and JavaScript effortlessly and quickly authorize or block them. Client-Side Protection allows your organization to streamline regulatory compliance, including requirements 6.4.3 and 11.6.1 in PCI DSS 4.0.