The Open Web Application Security Project (OWASP) is a non-profit organization that helps security experts protect web applications from cyber attacks. OWASP counts 32,000 volunteers worldwide who perform security assessments and conduct research on cybersecurity threats about which the larger cybersecurity community needs to be aware.
The OWASP Top 10 prioritizes the most important security risks affecting web applications in a single document and is widely regarded as the security risks document of record. Of course, there are far more than ten security risks. The goal of the OWASP Top 10 is simply to identify the risks to which security professionals need to pay specific attention so they can develop plans to mitigate them. OWASP periodically evaluates cyber-attack risks based on four criteria: ease of exploitability, prevalence, detectability, and business impact. Using their evaluation of these factors, they identify the most serious top 10 attack risks. Click here for a full description of the OWASP Top 10 updated in 2017.
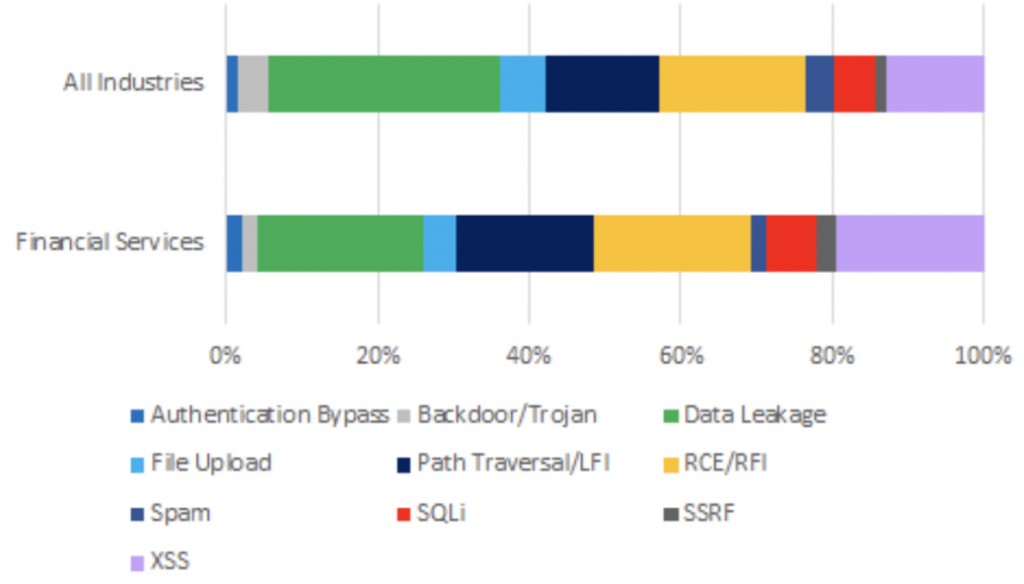
The top three OWASP attack risks by volume that have impacted the financial services sector since the beginning of 2021 are data leakage, RCE/RFI, and cross-site scripting (XSS).
Data leakage falls under the OWASP category A3:2017-Sensitive Data Exposure. The OWASP organization summarizes the risk like this, “Many web applications and APIs do not properly protect sensitive data, such as financial and healthcare information and PII. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.”
OWASP categorizes RCE/RFI as A1:2017-Injection. According to OWASP, “injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.”
Cross-site scripting (XSS) has its own discrete risk category, A7:2017-Cross-Site Scripting XSS. OWASP explains, “XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.”
At-a-glance: Major OWASP risks to the financial services sector
| Attack Name | OWASP Category | Percentage of Attacks | Principal risk to the financial services sector |
| Data Leakage | A3:2017-Sensitive Data Exposure | 21.9% | Data leakage enables attackers to steal or modify weakly protected yet high-value sensitive financial data, enabling them to commit credit card fraud, identity theft, or other crimes. |
| RCE/RFI | A1:2017-Injection | 20.5% | For financial services especially, when remote attackers run malicious code on servers to exfiltrate data, the data is often sensitive personal data. Once exfiltrated using this method, attackers use it to commit credit card fraud, identity theft, etc. |
| Cross-site scripting (XSS) | A7:2017-Cross-Site Scripting XSS | 19.4% | Cybercriminals inject client-side scripts into web pages viewed by other users. Because the malicious script is on the client-side, it is not attached to the targeted website but to unsuspecting website users. This presents a significant risk to the financial services industry because cybercriminals can use this method to extract valuable information (e.g., session cookies) that can be used to take over customers’ accounts on financial services sites. |
How OWASP risks to financial services compare to other industries
The volume of incidents by attack type in financial services largely mirrored other industries with the only significant difference being that XSS incidents in financial services were higher by almost 8% possibly a result of an increase in the number of people switching to online banking since 2020. Research shows the pandemic forced large-scale uptake in online banking. According to an analysis by Fidelity National Information Services, in April 2020 there was a 200% jump in new mobile banking registrations. That jump accompanied a 50% drop in branch bank traffic in the same month, according to U.S. banking data firm Novantas. Data leakage accounted for the highest number of incidents in financial services at 22%. Again this is possibly due to the high number of people using online banking to manage their finances and also due to the high value of the data held by financial institutions making it more of a target for cybercriminals.
How you can mitigate your risk
As a security professional in the financial services sector, how do you address these risks?
To mitigate the exposure and leaking of sensitive personal data, you should consider:
- Identify sensitive data and apply appropriate security controls.
- Don’t store sensitive data unless absolutely needed. Discard sensitive data, use tokenization or truncation.
- Encrypt all sensitive data at rest using strong encryption algorithms, protocols and keys.
- Encrypt data in transit using secure protocols like TLS and HTTP HSTS.
- Disable caching for sensitive data.
- Store passwords using strong, salted hashing functions like Argon2, scrypt and bcrypt.
For mitigating code injection attacks, Imperva recommends:
- Use a safe API which avoids the use of the interpreter entirely
- Use positive or “whitelist” server-side input validation
- Escape special characters
- Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
A web application firewall (WAF) is the most commonly used solution for protection from XSS and web application attacks. WAFs counter attack vectors with signature based filtering to identify and block malicious requests.
Learn more about how Imperva protects financial services data and all paths to it.
Try Imperva for Free
Protect your business for 30 days on Imperva.