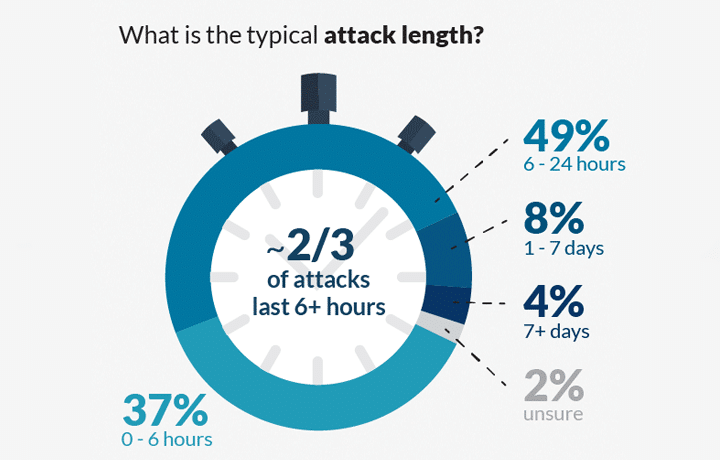
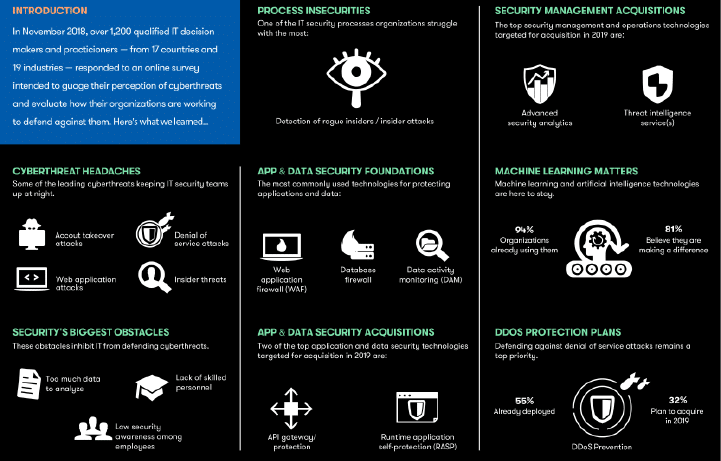
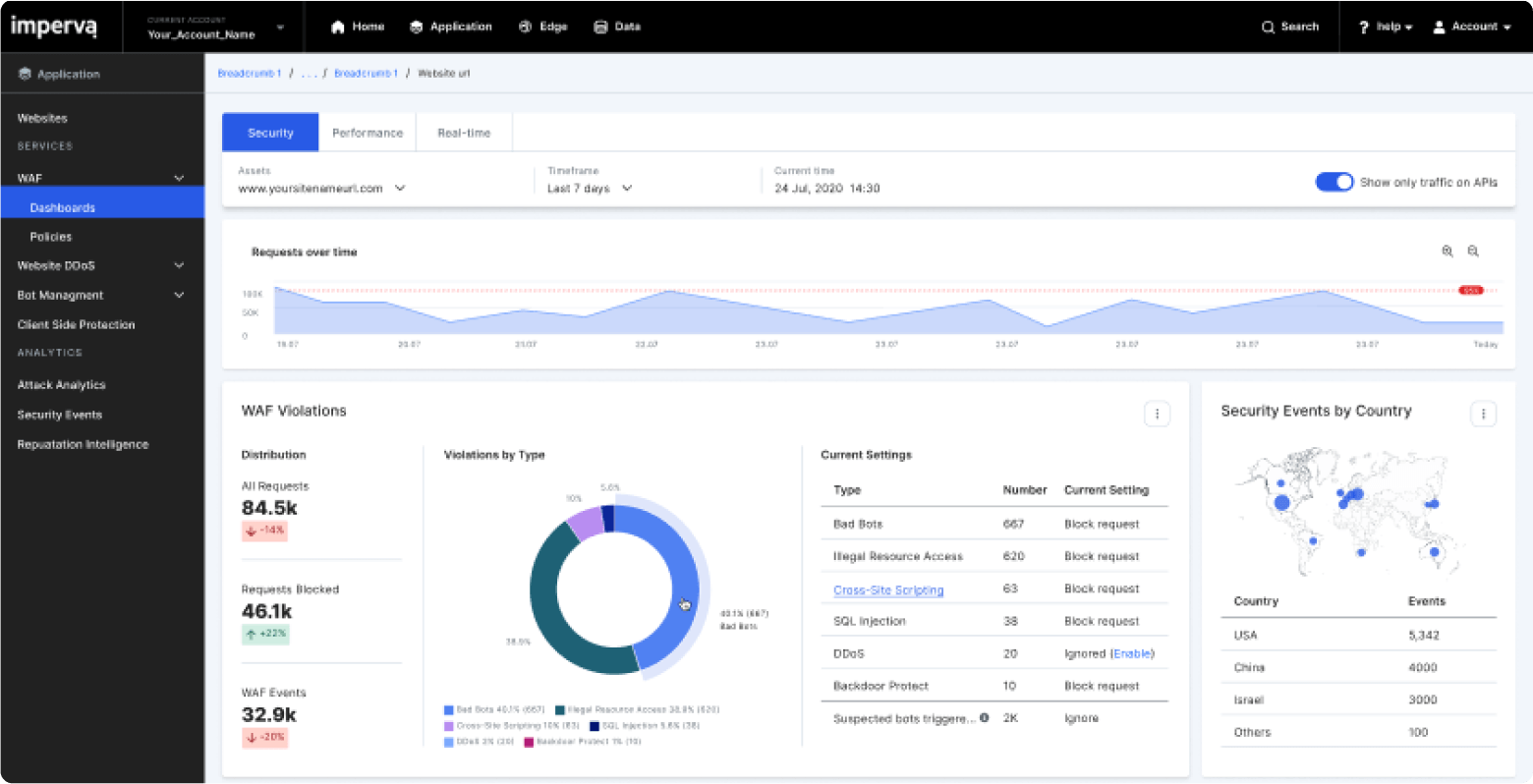
-
Upcoming Webinar
PCI DSS 4.0 – the New Client-Side Security Frontier
1726740000 -
Upcoming Webinar
The True Cost of API Insecurity and Bot Attacks in 2024
1727802000
Home > Resource Library
Imperva Resource Library
Popular Resources
Latest Blogs
The Importance of Bot Management in Your Marketing Strategy
May 17, 2024 5 min read
API Security and The Silent Menace of Unknown APIs
May 8, 2024 3 min read
Five Key Takeaways from the 2024 Imperva Bad Bot Report
Apr 16, 2024 4 min read


See how we can help you secure your web apps and data.
The State of API Security in 2024
Learn about the current API threat landscape and the key security insights for 2024
Download NowProtect Against Business Logic Abuse
Identify key capabilities to prevent attacks targeting your business logic
Download NowThe State of Security Within eCommerce in 2022
Learn how automated threats and API attacks on retailers are increasing
Free ReportPrevoty is now part of the Imperva Runtime Protection
Protection against zero-day attacks
No tuning, highly-accurate out-of-the-box
Effective against OWASP top 10 vulnerabilities
Want to see Imperva in action?
Fill out the form and our experts will be in touch shortly to book your personal demo.
Thank you!
An Imperva security specialist will contact you shortly.
Top 3 US Retailer