Every year, cyber attacks increase. Attackers get smarter, tools get better, and incentives to target sites grow. Over the last year, Imperva Threat Research detected a large increase in attacks targeting Australian sites, more than the global rise over the same timeframe.
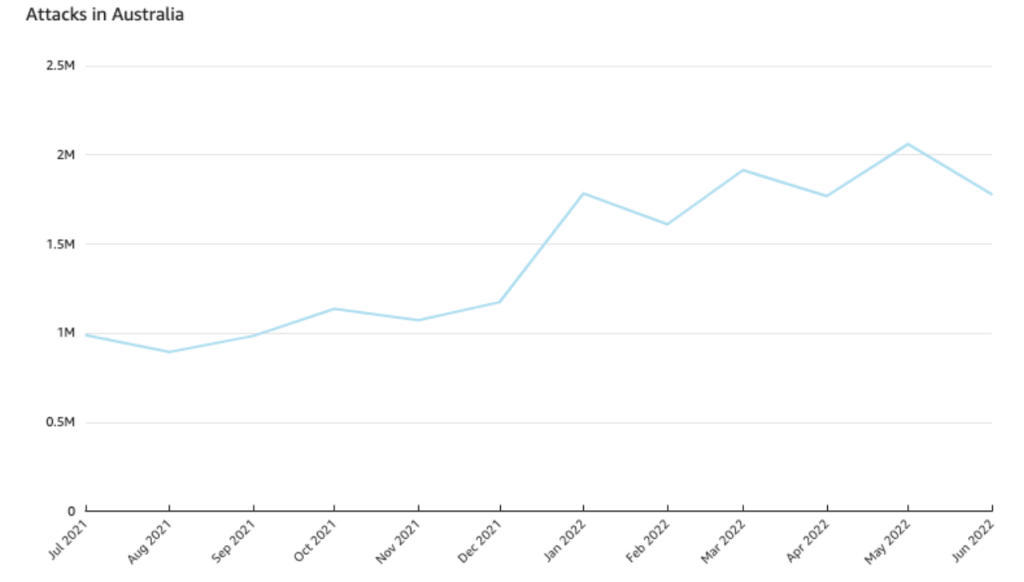
Australian attacks rose sharply between 2021 and 2022.
An Upward Trend
From July 2021 to June 2022, attacks increased by 81%. At the same time, Australia’s traffic only increased by 38%, showing that the rise in attacks is not simply due to increased network traffic. This trend grew over the past year, but increased sharply between December and January.
Attacks, in our classification, cover any security incident– a cluster of security events triggered by any application security solution– that’s caught by our WAAP. From there, we further categorize attacks by severity: critical, major, or minor. Severity is determined by analyzing a number of parameters that describe the attack, such as the number of events and type of attack, attack tool, and by comparing incidents. Incidents with multiple attack types, or those that are extremely focused in terms of target, origin, and tool, have higher severity scores.
In addition to the increase in all attacks from 2021-2022, critical incidents rose sharply as well. Attacks scored as critical rose almost 230% between August 2021 and May 2022. This is almost twice the rate that these attacks rose globally during the same period.
Industry Peaks
Financial, retail, and business services had the most attacks in one year, with financial and retail sites also having the largest jump in attacks. Incidents targeting financial sites, specifically, rose almost 200% in 2022. Financial cybercrime is a lucrative industry, and attackers are after credit cards, account information, banking details, and crypto wallets, among other things. Business Services may be targeted for a variety of reasons, including scraping data for competition, stealing customer databases or other information, or because small businesses may not have the same security controls on their sites as larger companies.

Attack Types
Bad bots tipped the scales, at a 108% jump from H2 2021 to H1 2022, and accounted for 35% of all active sessions during this period. It’s easy for attackers to aim bots at the information they want to steal, so bots are commonly used across the board for attacks in all industries. Bots shot up in the financial industry more than most, though, at an almost 600% increase, showing just how much hackers want financial information. According to Imperva’s 2022 Bad Bot Report, financial sites are heavily targeted by bad bots conducting account takeover attacks, carding, and other forms of financial fraud, which aligns with what we’ve seen in Australia over the past year.

Remote code execution, or RCE, followed at an almost 60% rise across the board. RCE allows attackers to execute malicious code on a targeted device, and can be used to get a wealth of information out of a system. RCE can be modified to fit any target, and can be combined with social engineering attacks, MFA bombing, or malware to gain easier access to the target’s system.
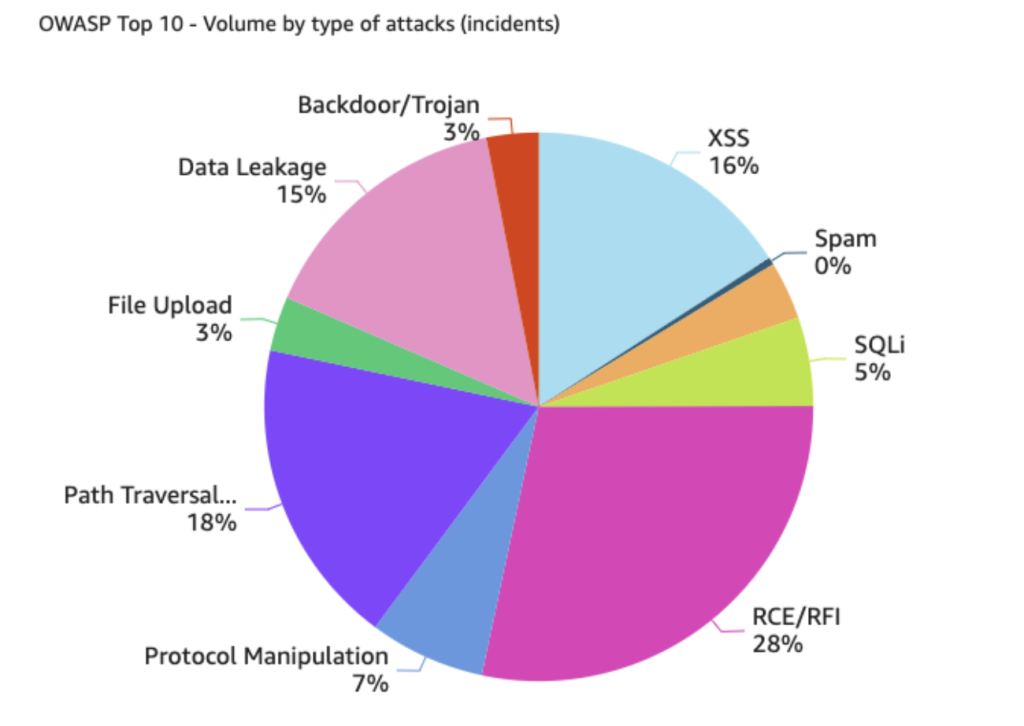
RCE was the largest OWASP threat to Australian sites, at 28% of all OWASP Top 10 attacks. Path traversal and local file inclusion (LFI) followed at 18%, and cross-site scripting (XSS) at 16%. LFI is a technique used to trick a web application into exposing files on a server, and XSS occurs when an attacker injects malicious code into a normal website. All of these techniques can all be used together to conduct a more efficient attack.
Account takeover attacks (ATO) in Australia differed from those globally as well. In Australia, attackers mainly used brute force attacks and credential stuffing, at 70% and 20% of ATO attacks, respectively. Globally, those two categories only accounted for a combined 28% of ATO attacks in the same time period. These attacks targeted less than 40 distinct accounts, mainly in the financial and retail sectors, so these Australian sites were distinctly targeted for financial gain.
Attacking IPs mainly came from the US and Australia, which is to be expected, given that it’s common for hackers to use botnets based in the country they’re targeting, and the US also accounts for a large number of infected devices.
Why Australia?
Attacks are rising globally, so why is Australia targeted more than other countries?
A recently released study of wealth per country ranked Australian adults as the richest in the world. According to the Credit Suisse Research Institute’s (CSRI) Global Wealth Report 2022 Australia is the wealthiest country in the world when it comes to wealth per adult (USD 273,900). This makes cybercriminals see Australia and its citizens as lucrative targets for identity theft, financial fraud, and other financially motivated scams. To commit these crimes at scale and with high success, cybercriminals need data– personal data about Australian citizens that can be used to fuel their campaigns.
Couple this with a surge over the pandemic period of businesses and government entities moving more and more of their applications and data online, it creates the perfect storm. Many have rushed their online implementations and transformation projects. and have taken shortcuts that leave the door open for cybercriminals to exploit. Recently, we’ve seen a large uptick in hackers recycling common off-the-shelf and automated attacks against Australian targets. They’re looking for known weaknesses and vulnerabilities in applications and APIs that allow them to gain access to the vast amounts of data in databases behind them, ultimately with the aim to exfiltrate data at scale that will allow them to build citizen profiles that are used as the basis of their scam activity.
No matter where you live, take steps to protect yourself and your business on the internet.
What you can do:
- Implement zero trust.
- Invest in security products.
- Ensure employees have adequate cybersecurity training.
- Require strong passwords.
- Adopt a cybersecurity policy.
Click here to find out more about Imperva’s application security solutions, and take the first step to protect your business from fraud.
Try Imperva for Free
Protect your business for 30 days on Imperva.













