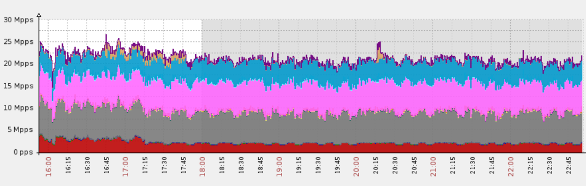
Several days ago one of our clients became the target of a massive DNS DDoS attack, peaking at approximately 25Mpps (Million packets per second).
The attack fit the description of other recently reported DNS floods, like the one that brought down UltraDNS earlier this month. With multiple reports coming from different directions, and with several large scale attacks on our own infrastructure, we are now convinced that what we are seeing here is an evolving new trend — one that can endanger even the most hardened network infrastructures.
Interestingly enough, in this case, the DNS queries contained non-spoofed IP data that allowed us to uncover the attacker’s true points of origin.
When we did, we were surprised to learn that the malicious requests were originating from servers of two other anti-DDoS service providers — one based in Canada, the other in China. All told, these were hitting our network at a rate of 1.5 Billion DNS queries a minute, amounting to over 630 Billion requests during the course of the 7 hour-long DDoS attack.
Following our notification, both anti-DDoS vendors acknowledged the attacks and dropped the responsible parties from their services.
Malicious misuse of security solutions is anything but new. However, this is the first time we encountered ‘rogue’ scrubbing servers used to carry out large-scale DDoS attacks. This fact, combined with the inherent danger of non-amplified DNS floods, is what makes these attacks so devastatingly dangerous.
DNS UDP Flood Is NOT DNS Amplification
When hearing about DNS DDoS, most people will probably think of the now common DNS amplification attacks. However, DNS floods are distinctively different — both in their methods of execution and in the type of grief they aim to deliver.
On one hand, DNS amplification is an asymmetrical DDoS attack in which the attacker sends out a small look-up query with spoofed IP of the target, making it the recipient of much larger DNS responses. With these attacks the offender’s goal is to achieve network saturation by continuously exhausting the target’s bandwidth capacity.
On the other hand, DNS floods are symmetrical DDoS attacks, trying to exhaust server-side assets (e.g., memory or CPU) with a multitude of UDP requests, generated by scripts running on several compromised botnet machines.
| DNS Amplification | DNS Floods | |
| Packets Per Second | Less | More |
| Packet Sizes | Abnormally Large | Regular-Sized |
| Targeted Resources | Network Pipes | CPU/Memory |
For the case in point, the most important difference between the two attacks is in the quality of the offender’s resources.
With DNS amplification, the effectiveness of an attacker’s own resources is increased by anywhere from 300% to 1000%, which means that large attacks could be initiated by relatively small botnets. On the other hand, with DNS floods there is no multiplier to speak of at all. This means that, in order to generate a DNS flood at the rate of 25Mpps, the offender needs access to an equally powerful botnet infrastructure’¦
Guess Who Has Powerful Infrastructures
DDoS protection services, with their proximity to the Internet’s backbone and wide traffic pipes, are specifically designed for high capacity traffic management. This, combined with the fact that many vendors are more concerned with ‘what’s coming in’ as opposed to ‘what’s going out’, makes them a good fit for hackers looking to execute massive non-amplified DDoS attacks.
Besides providing the ‘poetic twist’ of turning the protectors into aggressors, such mega-floods are also extremely dangerous.
Why DNS DDoS is on the Rise?
Effective DDoS mitigation is synonymous with accurate traffic filtering. For that reason DNS amplification attacks are actually easier to deflate as all uninitiated DNS responses are highly suspect and could be filtered on-edge, without any impact on the regular traffic flow.For example, one could categorically drop all unexpected DNS responses to port 53.
However, this isn’t the case for seemingly legitimate DNS flood queries, which cannot be dismissed before they are individually processed at the server level.
With on-edge filtering bypassed, and the path to the server CPU cores laid wide open, DNS floods have the potential to bring down even the most resilient of networks. Thankfully, this potential is usually capped by the capacity of the attacker’s own resources.
Any service providers that offer indiscriminative access to high-powered servers helps the offenders to outgrow these limitations. In this case, the security vendors played right into the hackers’ hands, by equipping them with high-capacity resources, able to generate billions upon billions of unfilterable DDoS requests enough to pose a serious threat to even to the most overprovisioned servers.
Try Imperva for Free
Protect your business for 30 days on Imperva.













