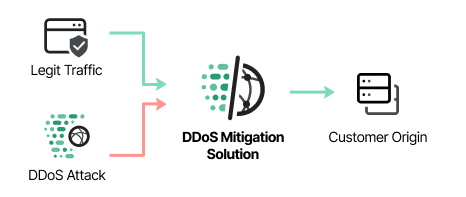Comprehensive DDoS mitigation for Layer 3, 4, and 7 attacks
Ensure business continuity
Every second counts when defending against a DDoS attack. Imperva prevents downtime fast and effective mitigation for all DDoS attacks and a guaranteed 3-second mitigation SLA for Layers 3 and 4 DDoS attacks.
Reduce costs
Every hour of downtime costs organizations tens of thousands of dollars in lost business and recovery costs. Imperva ensures business continuity with no performance impact.
Optimize performance
When under DDoS attack increased bandwidth usage slows performance drives up costs. Imperva gives you peace of mind that attack traffic will be blocked at the edge meaning no need for extra bandwidth.
DDoS mitigation for unmatched performance
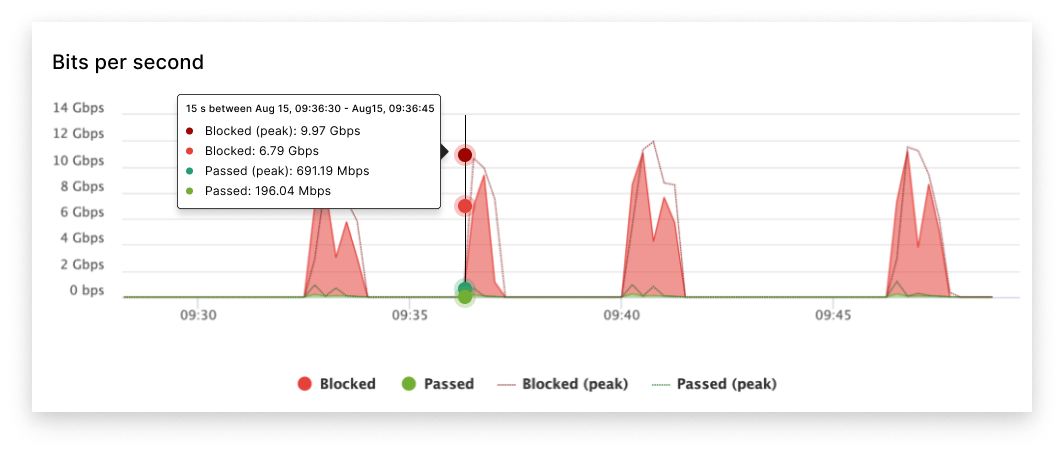


Fast time to mitigation for all DDoS attacks
Imperva provides a consistently fast time to mitigation for all types of DDoS attacks, ensuring your network stays protected with minimal downtime. For added assurance, we offer a guaranteed SLA of 3 seconds or less for DDoS attacks targeting Layers 3 and 4, delivering industry-leading protection against volumetric and protocol-based threats.

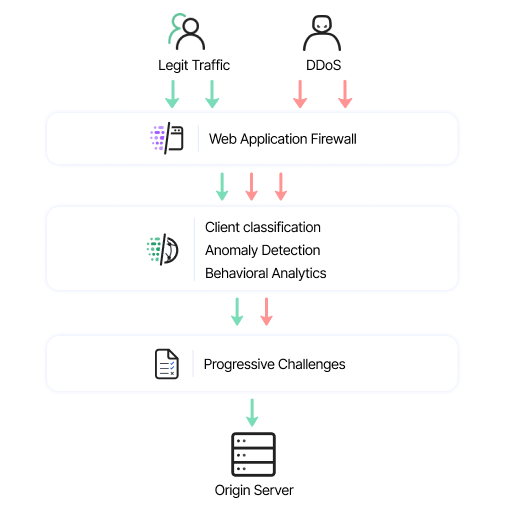
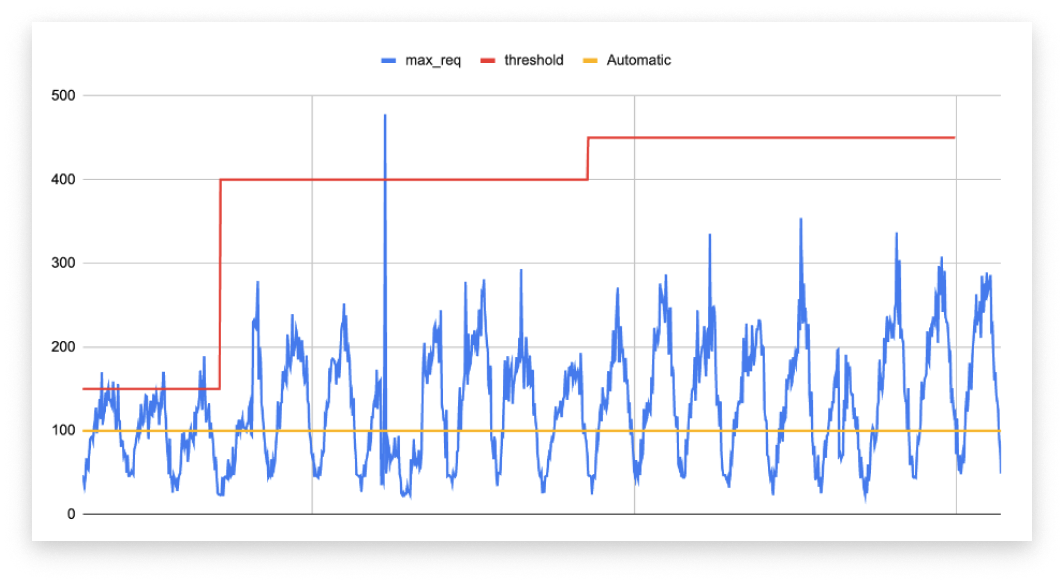
Adaptive protection against Layer 7 DDoS attacks
Imperva provides a consistently fast time to mitigation for all types of DDoS attacks, ensuring your network stays protected with minimal downtime. For added assurance, we offer a guaranteed SLA of 3 seconds or less for DDoS attacks targeting Layers 3 and 4, delivering industry-leading protection against volumetric and protocol-based threats.

Quick onboarding with fully automated DDoS protection
Imperva’s Application Security platform offers seamless self-onboarding and management, allowing users to easily configure and adjust DDoS protection settings through a self-service portal. Once set up, the platform’s fully-automated DDoS protection neutralizes threats without manual intervention, ensuring continuous defense even in on-demand mode. This combination streamlines management and guarantees round-the-clock protection, minimizing risks and maximizing uptime.

Global network for high-speed, low-latency traffic management
Imperva’s extensive global network ensures 95% of the world experiences sub-50 millisecond latency, delivering rapid, reliable performance even during DDoS attacks. Utilizing advanced Anycast routing and real-time capacity management, traffic is dynamically optimized across the most efficient paths, ensuring minimal latency and enhanced network speed. This system provides consistent, responsive service while preventing congestion and maintaining smooth operations during peak demand or attacks, making it ideal for international businesses requiring fast, efficient data transmission.

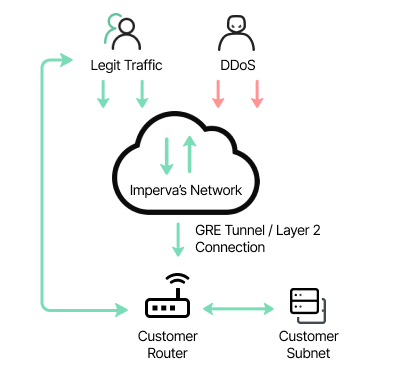
Seamless compatibility with any Internet Service Provider
Imperva’s DDoS Protection is fully ISP-agnostic, meaning it works seamlessly with any Internet Service Provider. This flexibility allows you to implement a unified, robust defense strategy across all ISPs without compatibility concerns, simplifying deployment and enhancing network resilience.
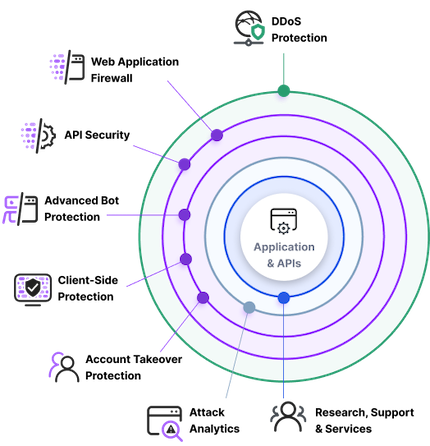
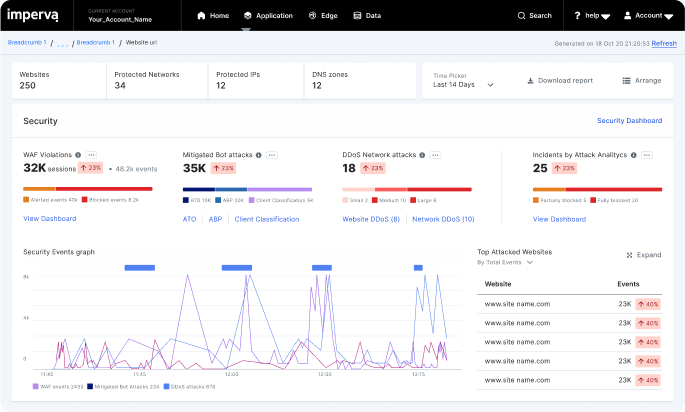
DDoS Protection
DDoS attacks are increasingly sophisticated and often automated, leading to significant financial and reputational damage from even brief downtime. Imperva DDoS Protection provides fast, scalable defense against advanced attacks, ensuring your operations remain available. Whether the threat targets the application layer, network layer, individual IPs, or DNS Servers, Imperva swiftly mitigates disruptions, safeguarding your infrastructure and enabling quick recovery.
Download datasheet