Protect all of your data, regardless of format or source
Structured data
Structured data types are characterized by predefined data models. They are text-based, easy to search, and consist of dates, phone numbers, Social Security numbers, names and transaction histories, etc. These data are generally stored in rows and columns and live in relational databases, data warehouses, etc.
Unstructured data
In the case of unstructured data, there is no defined data model. Data is not always text-based and can be difficult to search. It may include PDF, image, and video files. The data lives in various forms within applications, data warehouses, and data lakes. Examples include emails, messages, and conversation transcripts, to name a few.
Semi-structured data
Semi-structured data is loosely organized in a meta-level structure containing unstructured data in HTML, XML, and JSON formats. These data live in relational databases, tagged-text formats, abstracts, and figures. For example, semi-structured data include server logs, tweets organized by hashtags, and emails sorted by folders.
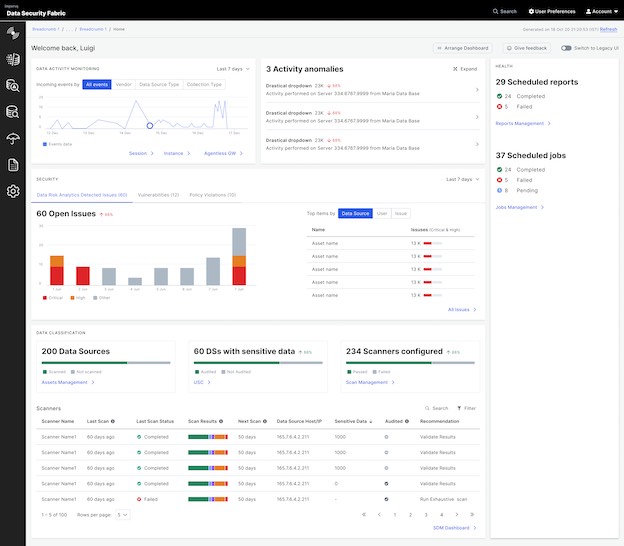
Database security was already complex, even before the challenges introduced by digital transformation and the rapid pandemic-driven movement of workloads to public, private, and hybrid cloud environments. Organizations that have made substantial investments in audit compliance solutions are now feeling pressure to create a data-centric security model that can monitor all data sources, not just those being audited.
As any data security practitioner knows, database proliferation is a very real issue. The cloud affords greater flexibility, but that flexibility can become a double-edged sword due to the ease with which DevOps teams, and even end-users, can quickly create, replicate, and move databases. In the on-premises database world, an organization may have used three to five databases that were the approved standard, and developers would attempt to funnel every application into using those databases. In the cloud world, those three to five databases are going to 10s and 100s of data repositories—and sometimes even more.
Protects all data sources and types
Any data, everywhere: from structured to semi-structured to unstructured
Imperva DSF provides a comprehensive and unified view of enterprise data risks across both structured and unstructured data management systems – meaning your security policies are applied consistently everywhere.
Imperva DSF can standardize data security controls across large and complex data environments, giving you complete visibility and centralized command of what is happening across all your file stores and data assets—on-premises, in the hybrid cloud, and across multiple clouds.


Databases
Imperva DSF offers robust protection for various database platforms, including but not limited to Oracle, Microsoft SQL Server, MySQL, PostgreSQL, IBM DB2, SAP HANA, Teradata, and more.
File servers
Imperva DSF can protect data stored on file servers, including network-attached storage (NAS) devices and shared file systems.
Cloud storage
With the increasing adoption of cloud computing, Imperva DSF extends its protection to various cloud storage services. This includes popular cloud platforms such as Amazon S3, Microsoft Azure Blob Storage, Azure Data Lake, Google Cloud Storage, and others.
Big data platforms
Imperva DSF can safeguard data residing in big data platforms such as Apache Hadoop, Apache Spark, and NoSQL databases like MongoDB, Cassandra, and Couchbase.
SaaS applications
Imperva DSF also offers protection for sensitive data stored within Software-as-a-Service (SaaS) applications. It integrates with popular SaaS platforms such as Salesforce, Office 365, and Google Workspace.
Virtualized environments
Imperva DSF can protect data within virtualized environments, including virtual machines and virtualized storage systems.
Supports multiple database and NoSQL platforms & services
Imperva Data Security Fabric protects all data types with a single system that delivers multiple business capabilities
Imperva Data Security Fabric is the first data-centric solution that enables your organization's security and compliance teams to quickly and easily secure sensitive data no matter where it resides with an integrated, proactive approach to visibility and predictive analytics.
Imperva Data Security Fabric is composed of cutting-edge orchestrated technical capabilities that work in unison to protect your data across your entire organization:
Data Discovery & Classification
Discover ungoverned data, classify all data, and assess vulnerabilities.
Learn moreData Activity Monitoring
Gain complete visibility and ensure compliance with continuous monitoring, auditing and analyzing all data store and data types.
Learn moreData Retention & Archive
Meet any data archiving requirement using the most cost efficient storage technology available.
Learn moreData Risk Management
Detect and report non-compliant, risky, or malicious data access behavior across all of your data repositories enterprise-wide to accelerate remediation.
Learn moreEcosystem Integrations
Enhance the value of your existing technology investments—for both incident context and additional data capabilities.
Learn moreData Encryption & Tokenization
Protect critical data with encryption, key management, and tokenization wherever it resides.
Learn moreStatic Data Masking
Modify sensitive data so it is of no value to unauthorized users while still being usable by your systems.
Learn moreAutomated Workflows & Playbooks
Achieve higher scale and increase DevOps efficiency through the use of automated workflows delivered through trusted repositories.
Learn moreSensitive Data Management
Identify, locate, classify, and secure sensitive data across various data stores located either on-premises or in the cloud.
Learn more