It’s been a busy year thus far in the cybercrime world with the stakes seeming to grow higher every month. Just last month, insider threats were making headlines with a news report that Reality Winner, a contractor for the National Security Association with a top-level security clearance, leaked sensitive documents related to an FBI investigation into Russian hacking to the media.
Threats from insiders, while not as common as breaches from external actors, are still very significant and damaging. According to the 2017 Verizon Data Breach Investigations Report (DBIR), insider threats account for 25 percent of breaches and often take months or years to detect. Insider threats are among the costliest breaches because they often take longer to discover which gives the perpetrators ample time to damage systems and steal valuable data. The longer the attack is active and undetected, the higher the cost to the organization.
Insider threats can be classified into three types:
- Malicious insiders – Trusted insiders that intentionally steal data for their own purposes.
- Careless and negligent insiders – These are people within or directly associated with the organization that due to careless behavior expose sensitive data, despite not having malicious intent.
- Compromised insiders – Typically this is an account takeover scenario, where credentials have been guessed or captured as part of a targeted attack. Although the actor behind the account is not an employee, the use of legitimate credentials presents as if it were an employee.
While malicious and compromised insiders are frightening, it’s worth noting that security professionals often identify employees as the weak link in the cyber security chain since they often don’t follow corporate guidelines regarding safe computer and application use.
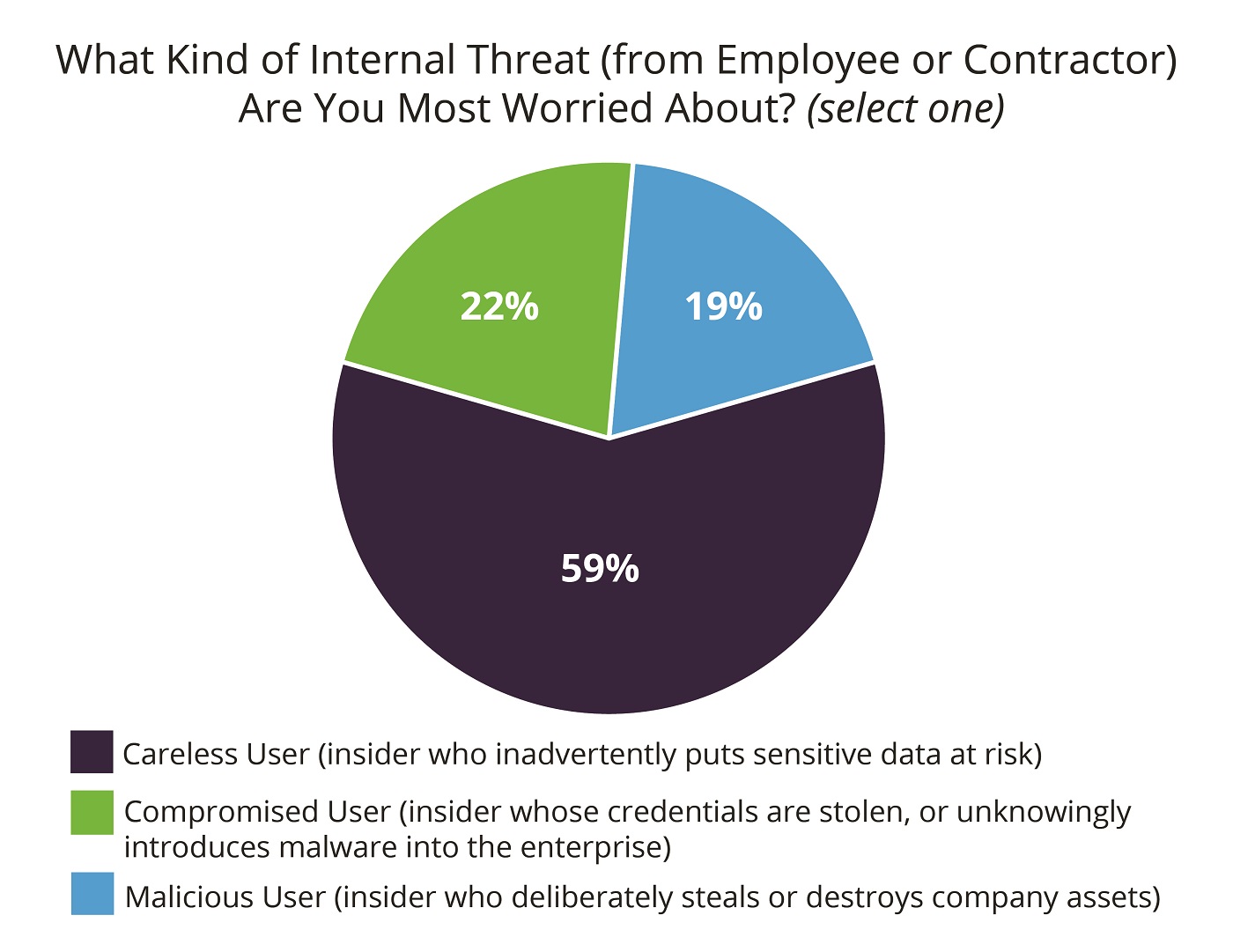
With the lurking danger associated with careless users, it isn’t surprising then that in a survey of 310 IT security professionals at Infosecurity Europe more than half (59 percent) were deeply concerned not primarily about malicious users, but about careless users who unwittingly put their organization’s data at risk.
While there are specific strategies and tools to help manage and investigate insider threats, 14 percent of respondents revealed they don’t have a technology solution in place to detect insider threats.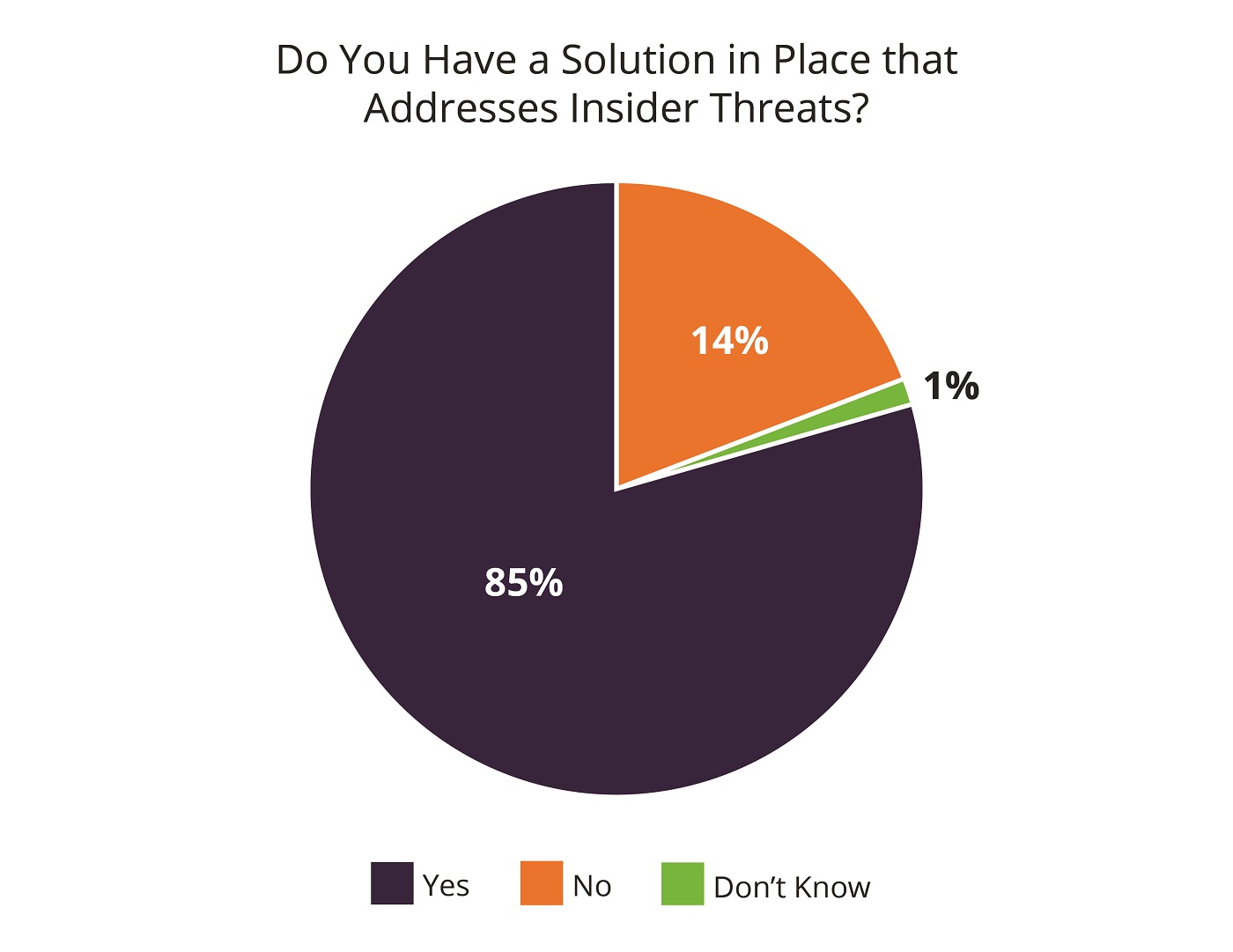
And those that did use tools found them to be labor intensive. For example, fifty-five percent of respondents said that managing too many security alerts was the most time-consuming element of investigating insider threats.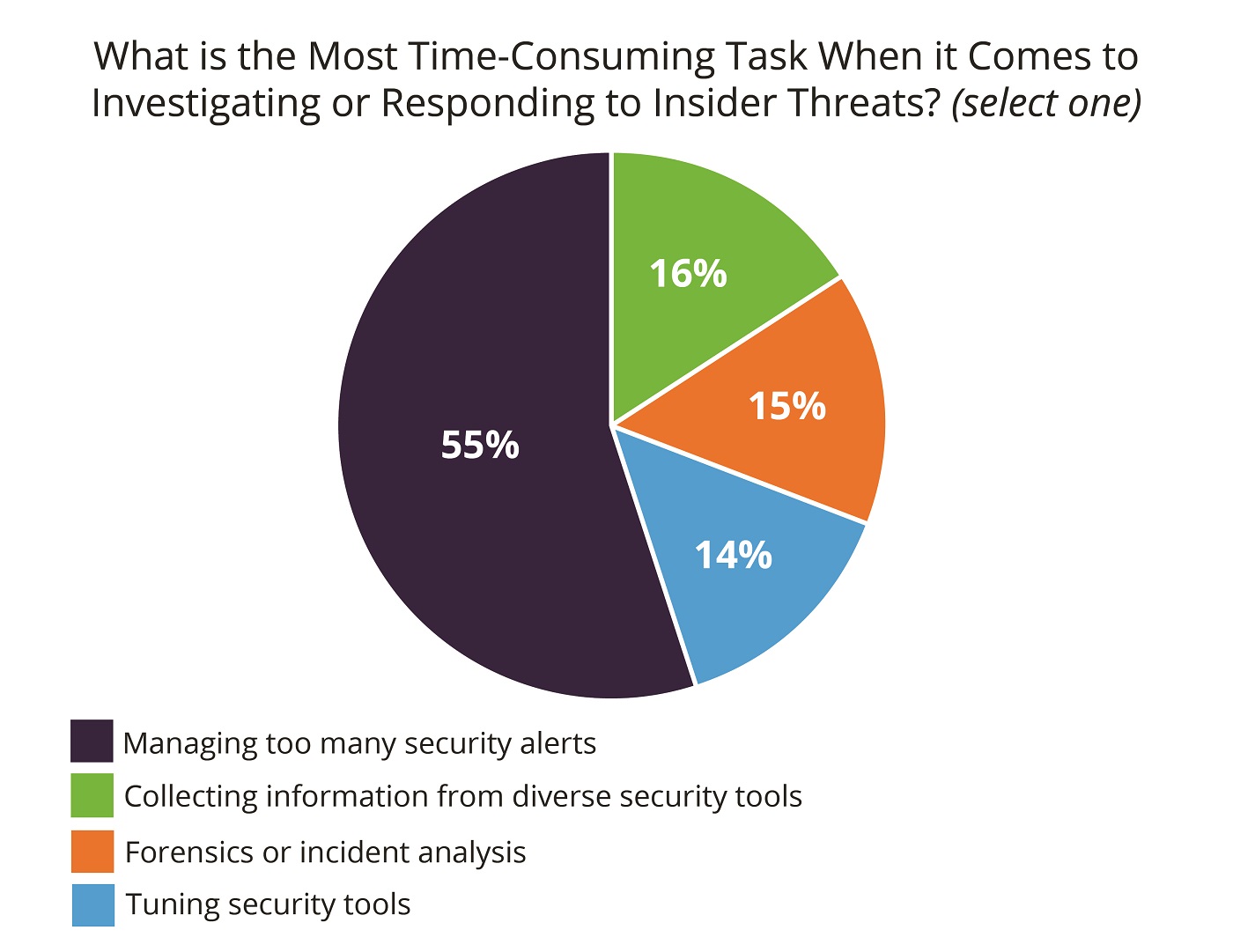
And forty-four percent of security professionals admitted they do not have enough staff resources to analyze data permissions correctly.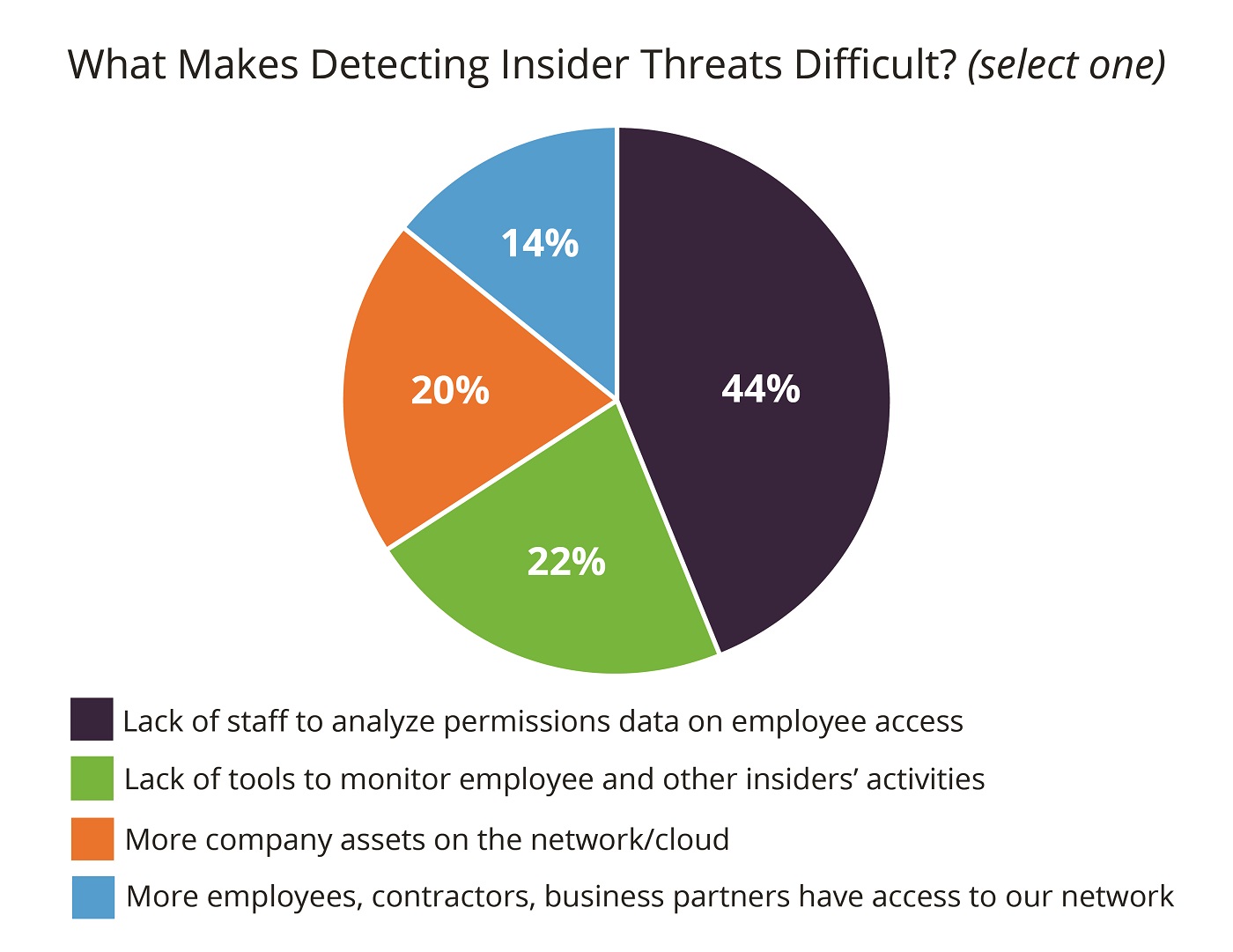
While detecting insider threats can often include labor intensive analysis of alerts and reports, this is just the type of work where machine learning solutions excel. Respondents recognized this as 65 percent estimated that machine learning-based solutions applied to identifying insider threats would free up more than 12 staff hours a week – which equates to more than 600 hours a year.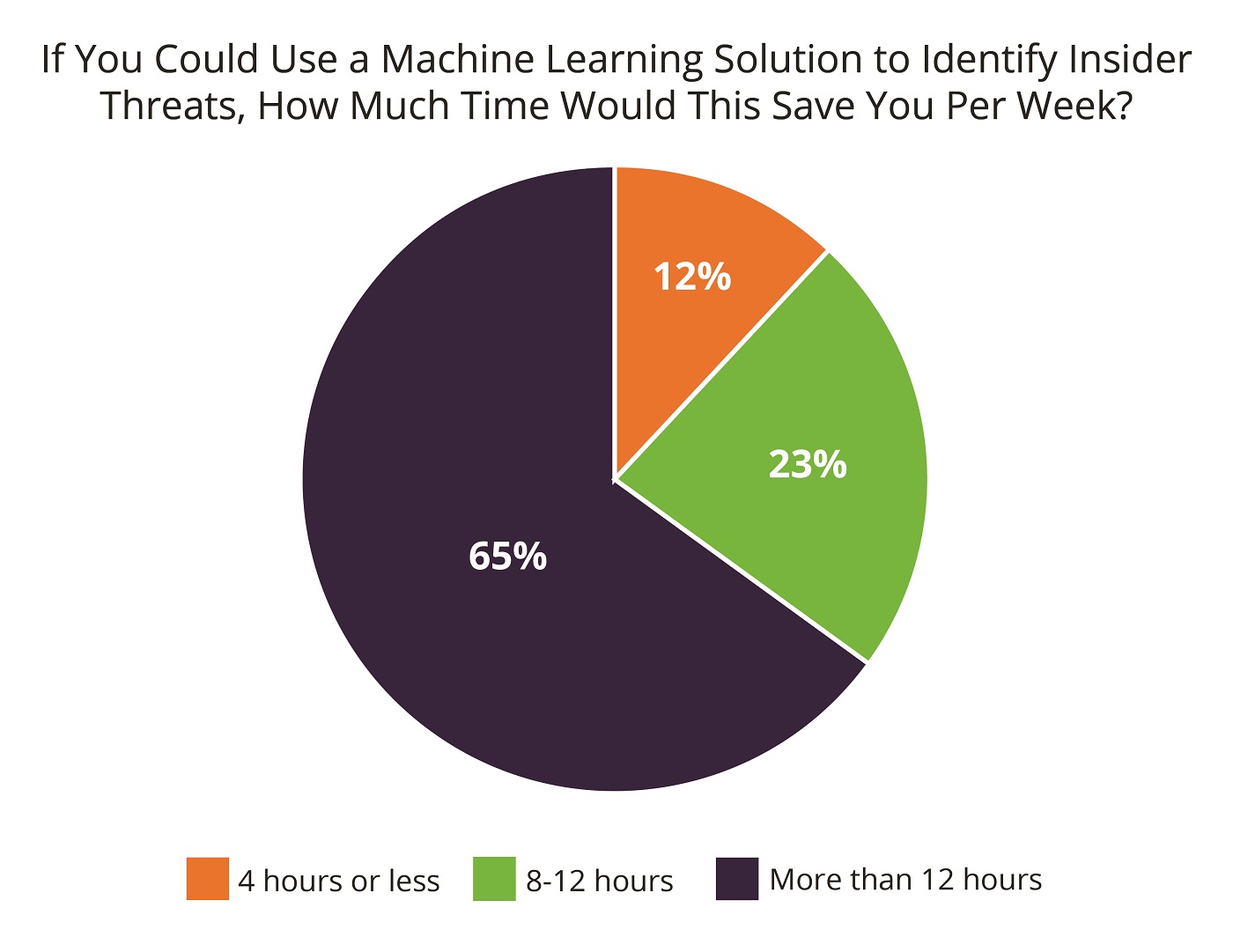 Employees, contractors, business associates or partners pose the biggest risk to enterprise data since they are by definition granted trusted access to sensitive data. To mitigate the risk, corporations should ask themselves where their sensitive data lies, and invest in solutions that directly monitor who accesses it and how.
Employees, contractors, business associates or partners pose the biggest risk to enterprise data since they are by definition granted trusted access to sensitive data. To mitigate the risk, corporations should ask themselves where their sensitive data lies, and invest in solutions that directly monitor who accesses it and how.
Learn more about Imperva breach prevention solutions that help pinpoint critical anomalies that indicate misuse of enterprise data stored in databases, file servers and cloud apps. For an in-depth look at combating insider threats, see the Imperva Whiteboard Wednesday video, “Challenges of Insider Threat Detection.”
View the full survey results on SlideShare.
Try Imperva for Free
Protect your business for 30 days on Imperva.
![Top Insider Threat Concern? Careless Users. [Survey]](/wp-content/themes/impv-blog/dist/imgs/default-thumbnail/data-security.jpg)








