Update: Sept. 29th 2014
In the four days that have passed since the Shellshock vulnerability disclosure, the Incapsula web application firewall has deflected over 217,089 exploit attempts on over 4,115 domains.
During this period the average attack rate has nearly doubled, climbing to over 1,970 attacks per hour. As of this time, the Incapsula system has documented Shellshock attacks originating from over 890 offending IPs worldwide.
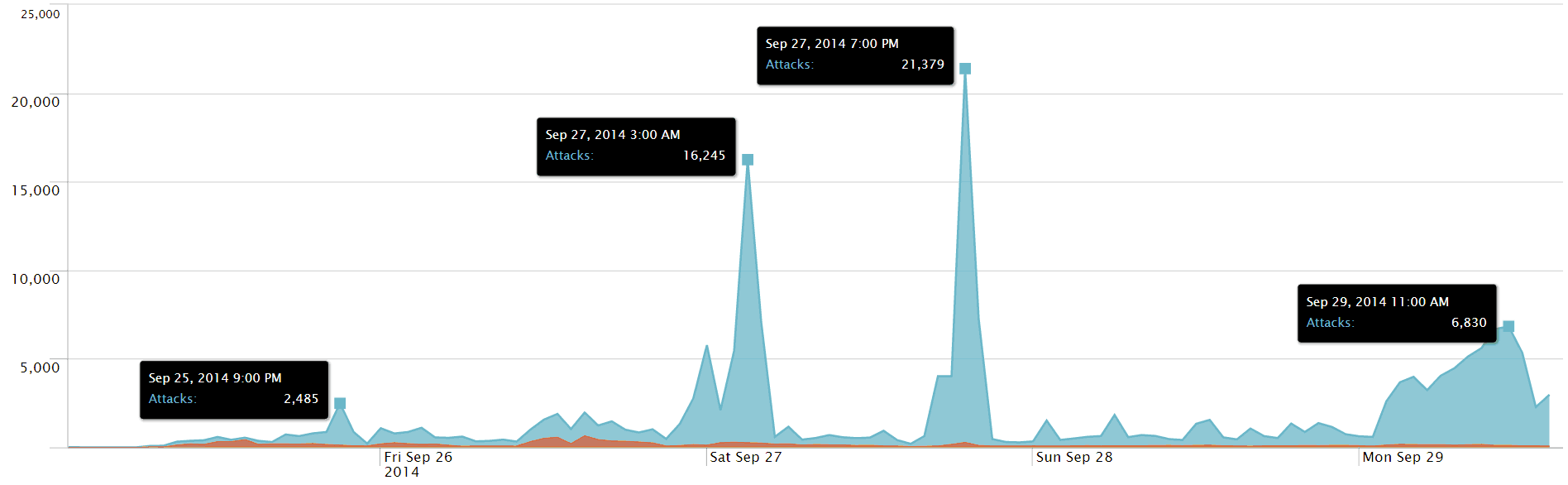
The accompanying graph reflects the increasing attack rates. In the past 24 hours, Incapsula has seen them transitioning from short high-volume bursts into a steady stream of malicious requests.
This is the distribution of attack attempts:
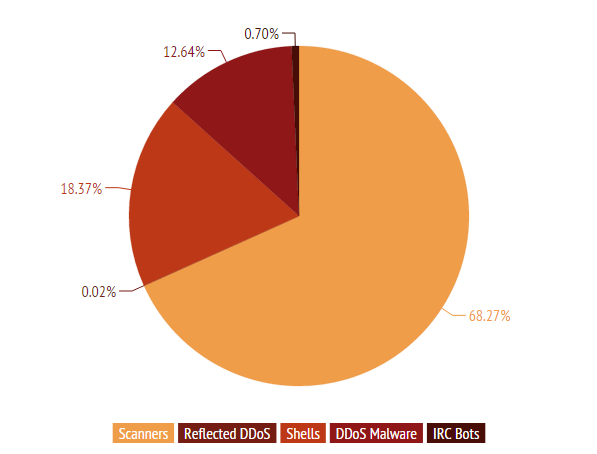
- Scanners (68.27%) – Attempts to verify the existence of the Shellshock vulnerability. Only 6% of these are automated scanner tools that are likely to be used by website operators to identify the issue. The bulk of these (+ 62%) are targeted probing attempts, which — if successful — are likely to lead to an attack.
- Shells (18.37%) – Attempts to establish remote access and use it to hijack the server (e.g., using Python or Perl scripts).
- DDoS Malware (16.64%) – Attempts to inject the server with DDoS malware with the purpose of turning it into a botnet ‘zombies’.
- IRC Shells (0.7%) – Attempts to hijack the server with various IRC bots, to be remotely controlled from IRC chatrooms.
- Reflected DDoS (0.02%) – Attempts to DDoS another website/server by ‘bouncing’ the request from the intermediary server to the actual target. Such tactics are often used by hackers to counter IP blacklisting.
Incapsula now has records of Shellshock attacks originating from almost every country around the globe. The attackers’ most common countries of origin are as follows:
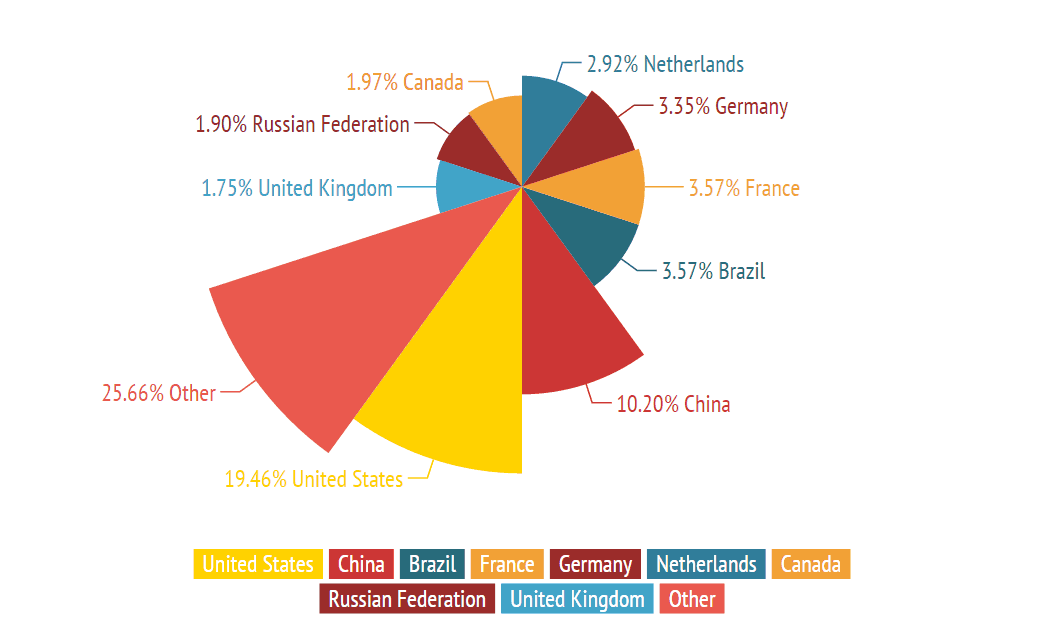
Stay tuned. We will continue to update as things evolve.
Original Post: Sept. 26th 2014
The Internet is currently abuzz with talk about Shellshock, the new ‘mega vulnerability’ discovered in Bash (a.k.a. the Bourne-Again Shell), the most common command-line shell used in Linux/UNIX systems.
Yesterday we released a quick blog post to let our customers know that we have already modified our WAF to protect against this vulnerability.
Now that the dust has settled, we are following up with some of the details we garnered through analyzing attack attempts against Incapsula-protected websites and servers.
Attack Methodology
Shellshock (CVE-2014-6271 and CVE-2014-7169) has been drawing parallels to the Heartbleed vulnerability disclosed in April of this year.
Much of the risk associated with Shellshock is derived from the fact that Bash is widely used by many Linux and UNIX servers. The vulnerability potentially allows unauthenticated attackers to remotely execute code on these machines, which enables data theft, malware injection and server hijacking.
As dangerous as this sounds, Shellshock can be contained.
Remote attackers trying to exploit this vulnerability would have to use other applications or CGI Scripts as a conduit, as Bash is typically not accessible to remote users. Many common applications, such as email and web servers running on Linux and UNIX systems, regularly interact with Bash. With Shellshock, perpetrators could abuse these programs to send remote shell commands to Bash.
A simple example would be that of a common web server, which accepts user-agents.
If user-agents are accepted without proper sanitization, it is possible that a specially crafted user-agent could be processed by a Bash script and executed because of the vulnerability, leading to an unauthorized access to the web server.
An examples of such user-agents, similar to the ones we are now seeing in the wild, are:
() { :; }; echo -e "Content-Type: text/plain\n"; echo qQQQQQq
() { test;};/usr/bin/eject
Measuring the Impact — The Numbers Game
So what have we seen? In the first twelve hours after we started monitoring the attack we collected the following statistics regarding Shellshock exploit attempts against our network.
The graph below shows attack trends during the last 24 hours.
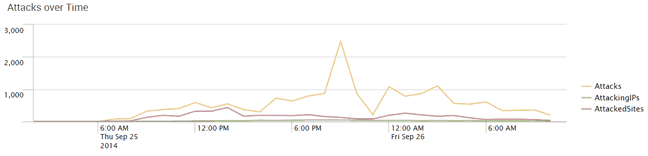
In that period we saw:
- Over 17,400 attacks at an average rate of ~725 / hour.
- Over 1,800 domains attacked.
- Attacks originated from 400 unique IP addresses.
- Over 55% of all attacks originated from China and US.
- Over 57% of the attacks were performed with cURL.
Below is a graph showing attacking IPs distribution by country of origin.

What we are seeing here are hacker using existing botnets to create new ones: running automated scripts from compromised servers to add more hijacked machines to their ‘flock’.
During the last 24 hours we saw several botnet shepherds using repurposed DDoS bots in an attempt to exploit Shellshock vulnerability to gain server access.
In the numbers game the house always wins and so it is safe to assume that some of these attempts will end up being successful. These will provide another boost to an already large and rapidly growing botnet army.
Bunkering our Customers
In order to protect our customers, we’ve updated the Incapsula web application firewall (WAF) security rules to stop all potential Shellshock-related attacks.
The WAF rules we implemented work in multiple stages, scanning all inputs (e.g., request headers, POST body and etc.) to detect and block any attempt to exploit the Shellshock vulnerability.
After blocking thousands of attack attempts and dealing with multiple attack variants we can safely say that Shellshock cannot be exploited on any system protected by the Incapsula WAF.
Having said that, we strongly suggest that all administrators take steps to patch their systems, as soon as security patches are available.
This report was anonymously compiled from a sample of one thousand websites of Incapsula customers, with an average of 50,000 to 100,000 monthly visitors.
Try Imperva for Free
Protect your business for 30 days on Imperva.










