Another remote code execution vulnerability has been revealed in Drupal, the popular open-source Web content management system. One exploit — still working at time of this writing — has been used in dozens of unsuccessful attacks against our customers, with an unknown number of attacks, some likely successful, against other websites.
Published on February 20th, the new vulnerability (known as CVE 2019-6340 and SA-CORE-2019-003) is about fields types that don’t sanitize data from non-form sources when the Drupal 8 core REST module and another web services module such as JSON:API are both enabled. This allows arbitrary PHP remote code execution that could lead to compromise of the web server.
An exploit was published a day after the vulnerability was published, and continues to work even after following the Drupal team’s proposed remediation of disabling all web services modules and banning PUT/PATCH/POST requests to web services resources. Despite the fix, it is still possible to issue a GET request and therefore perform remote code execution as was the case with the other HTTP methods. Fortunately, users of Imperva’s Web Application Firewall (WAF) were protected.
Attack Data
Imperva research teams constantly analyze attack traffic from the wild that passes between clients and websites protected by our services. We’ve found dozens of attack attempts aimed at dozens of websites that belong to our customers using this exploit, including sites in government and the financial services industry.
The attacks originated from several attackers and countries, and all were blocked thanks to generic Imperva policies that had been in place long before the vulnerability was published.
Figure 1 below shows the daily number of CVE 2019-6340 exploits we’ve seen in the last couple of days.
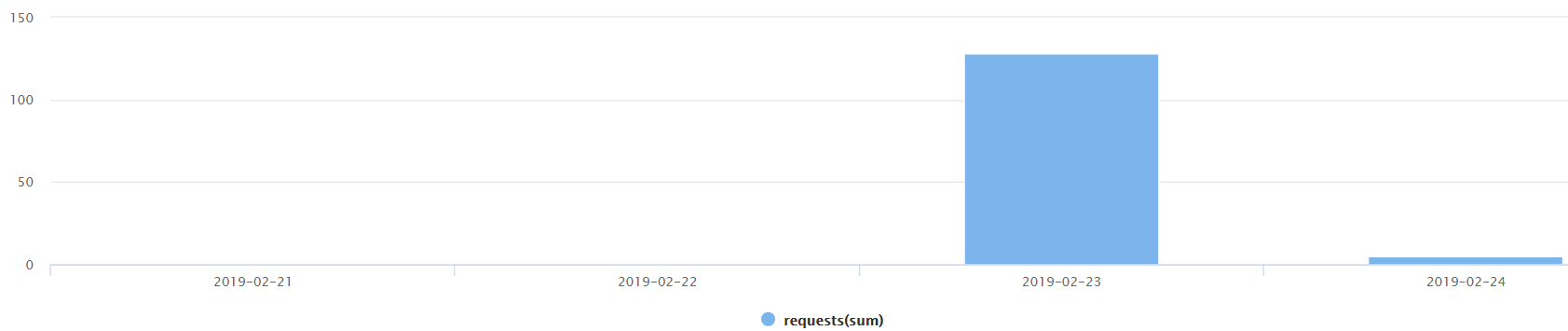
Figure 1: Attacks by date
As always, attacks followed soon after the exploit was published. So being up to date with security updates is a must.
According to Imperva research, 2018 saw a year-over-year increase in Drupal vulnerabilities, with names such as DirtyCOW and Drupalgeddon 1, 2 and 3. These were used in mass attacks that targeted hundreds of thousands of websites.
There were a few interesting payloads in the most recent attacks. One payload tries to inject a Javascript cryptocurrency (Monero and Webchain) miner named CoinIMP into an attacked site’s index.php file so that site visitors will run the mining script when they browse the site’s main page, for the attacker’s financial benefit.
The following is CoinIMP’s client side embedded script. The script uses a 64 character length key generated by the CoinIMP panel to designate the site key of the attacker on CoinIMP.
The attacker’s payload also tries to install a shell uploader to upload arbitrary files on demand.
Here is the upload shell content:
Imperva Customers Protected
Customers of Imperva Web Application Firewall (WAF, formerly Incapsula) were protected from this attack due to our RCE detection rules. So although the attack vector is new, its payload is old and has been dealt with in the past.
We also added new dedicated and generic rules to our WAF (both the services formerly known as Incapsula and SecureSphere) to strengthen our security and provide wider coverage to attacks of this sort.
Try Imperva for Free
Protect your business for 30 days on Imperva.














