If you’ve made a career out of developing or producing content for games, it’s probably old news to you that distributed denial of service (DDoS) attacks are a real and frequent threat in your industry. While the existence of DDoS attacks is familiar, the techniques and impact of those attacks have continued to evolve, and in recent years have undergone an exponential leap in both size and severity.
“The threat of DDoS attacks is so pervasive in online gaming that just about everyone that plays a connected multiplayer game is aware of and fears the tactic,” said GamesBeat reporter Jeff Grubb, “They have hit online services like Sony PlayStation Network and Microsoft Xbox Live as well as games like World of Warcraft and H1Z1. Not only does DDoS prevent players from connecting, but it rings up a significant cost in missed revenues for the targeted companies. And the most frightening part is that they keep happening, and most prevention methods have not reduced the number of attacks.”
We’ve seen attacks on the Imperva Incapsula network recently that support the observation that there is a rising trend in progressively complex attacks. Most recently we wrote about a sophisticated HTTP flood attack on the application layer and a massive 470 Gbps DDoS attack.
VeriSign also reported that it observed 85 percent more attacks in the fourth quarter of 2015 when compared to the previous year. The size of those attacks also increased, with a third involving more than 5 Gbps of data, and an additional third involving more than 10 Gbps. VeriSign saw its single largest attack ever in the form of a 65 Gbps assault on a telecommunications company, involving more than 125 million packets per second of traffic.
We’ve put together some of the most commonly asked questions about DDoS attacks on video gaming companies and presented information on what you can do about it.
Why are video game companies at high risk for DDoS attacks?
Game developers and other industry-related companies remain the most frequent target for DDoS attacks, comprising more than 54 percent of all denial of service attempts.
This is primarily due to two key factors: First, game companies are high visibility targets with a young vocal audience eager to complain publicly about network outages – an important factor when so many attackers are chiefly seeking to make a name for themselves. Secondly, game companies rely on proprietary network infrastructures and protocols that can’t use many of the standard network security methods, especially when it comes to application level attacks and HTTPS protection measures.
How can my company protect itself from DDoS attacks?
Your ultimate protection will come from technological measures deployed to prevent and mitigate DDoS attacks. Our advice is before you begin deploying those measures, you may want to look at your staffing resources to ensure that your company is ready in the event of a DDoS attack.
Does my company need a DDoS response team?
In short: Yes.
A DDoS response team (or general disaster response team) is a vital component if your company is going to respond quickly and decisively to a DDoS attack. More important, the practices and procedures you’ll need to create an effective response team will also improve your prevention measures, and help move your company from a “soft” target into a “hardened” target.
Consider taking these steps while creating your DDoS response team:
- Clearly identify all team members and their responsibilities during an attack.
- Create an escalating response plan that has a chain of actions that are triggered by an attack. A typical chain follows this escalation: monitoring, identification of attack, alerting key personnel, communicating with customers, deploying mitigation measures and initiating recovery.
Recruiting network operations staff that have DDoS experience may take longer, but having a person on staff who can help identify the problem quickly can go a long way in having that ideal response team.
How can I improve in-house security measures?
While effective technological measures will be required to fully secure your network, data and applications, it’s important not to neglect these in-house steps:
- Ensure all personal computers are properly secured with individual firewalls and antivirus software.
- Make sure all personnel follow best practices for creating and maintaining secure passwords, including regularly changing those passwords.
- Ensure all personnel use proper procedures for keeping data private, ideally by creating clear in-house guidelines for who has access to what data and when.
How can technological solutions protect my game company from DDoS attacks?
While your company can take the steps above to keep itself safe, the only way to truly prevent or stop a DDoS attack is to protect your network infrastructure and data itself.
To be effective, a security solution you choose must, at a minimum, be able to:
- Monitor your network traffic continuously.
- Effectively identify suspicious or dangerous traffic.
- Instantly reroute or remove that dangerous traffic.
How do I identify an effective security solution?
Since game companies usually can’t use standard features like a web application firewall (WAF), find out if your DDoS solution meets your unique needs.
There are a variety of individual tools or an all-in-one security platform to choose from. Your solution should satisfy requirements in these key performance indicators:
- Detection: An effective solution must identify dangerous traffic as close to real-time as possible, and before it swells into a full-on attack.
- Time-to-mitigation: The solution’s response to an attack (redirection or removal) must initiate and begin mitigating dangerous traffic as soon as possible—preferably within 1-5 minutes.
- User classification: An effective solution can accurately identify normal users of your services to ensure their experience is unaffected.
- Up-time: The solution must have 100 percent up-time, or as close to it as possible.
- Deployment: The solution is easy to deploy without disrupting your normal functions.
How can my game company protect itself from network layer DDoS attacks?
A network layer assault in which the attackers target your network infrastructure itself is the most common type of DDoS attack. Effective solutions must be able to protect your network assets while maintaining normal operations for authorized users.
Can a VPN help keep my company safe?
A virtual private network (VPN) can protect against DDoS attacks by acting as a proxy server for your entire network infrastructure. The most effective solution presents only the VPN’s IP address to the outside world, while still allowing authorized users to access areas covered by your internal IPs. Attackers digging for your IPs will only find the VPN’s addresses, at which point the mitigation measures deployed through the VPN will spring into action.
Do I need a GRE tunnel?
A generic routing encapsulation (GRE) tunnel is a vital component that ensures your normal users aren’t affected by mitigation measures. A GRE tunnel simplifies your network traffic by establishing a high-speed point-to-point connection between network nodes that bypass normal routing speed bumps.
Typically, monitoring and screening measures are deployed at the start of the tunnel, so only traffic cleared as “safe” is able to enter the tunnel and speed its way toward your systems, where it can also be given a final clearance check before proceeding into your internal network.
Will a VPN impact my users?
If it’s implemented properly, a VPN should not impact your authorized users. Toward this end, your solution provider must have enough data capacity to mitigate the extremely large data volume that can be used in modern DDoS attacks. Your provider must also be able to guarantee screening and scrubbing procedures that are responsive enough to approve your normal users and send them on their way without delay.
How can my company protect against application layer DDoS attacks?
Although application layer attacks are much less common for game companies than network level attacks, they still present a risk.
While network layer protection secures data, application layer protection validates your users using methods like those mentioned below.
How does client classification and whitelisting work?
An effective client classification system can distinguish not only between humans and bots, but between good bots and bad bots. The best solution will do this quickly by interrogating various attributes associated with your network traffic, including HTTP headers (when relevant), variations in cookie support, IP and ASN information and other potentially unique file characteristics.
Using those elements, your solution can build accurate profiles of your authorized users, along with incorporating a “whitelist” based on intelligent profiles describing typical attacker vs. user characteristics. Here’s how we approach client classification for Incapsula.
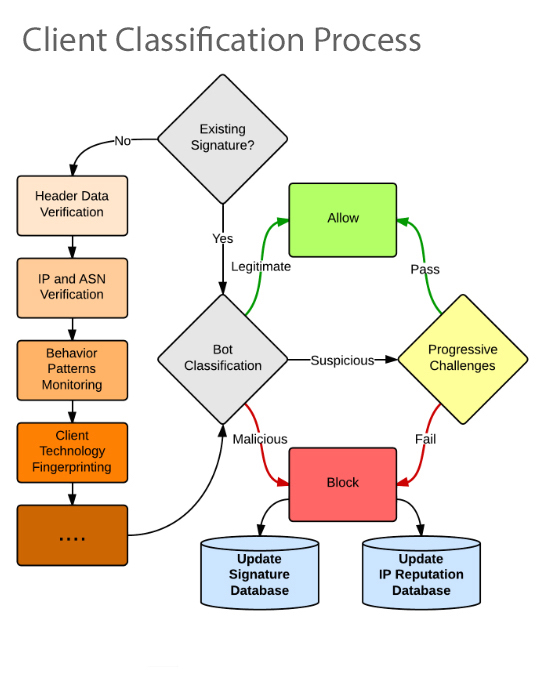
How do progressive challenges work?
A hardened protection system uses a set of progressive challenges designed to “trip up” dangerous traffic, while traffic that fits the authorized profile proceeds unimpeded. Examples of progressive challenges include using JavaScript and cookie challenges to weed out bots imitating web browsers, even including a CAPTCHA system to verify whether a user is a real person or not.
What is behavior detection?
The most sophisticated bots are increasingly immune to progressive challenges, so the next level of challenge uses automated behavior detection routines as a second line of defense. Behavior detection is a complex process, and requires your provider to have a robust database of usage profiles and other indicators that allows the solution to correctly identify suspicious behavior.
How can my company protect against DNS attacks?
A new wave of attacks on DNS servers is becoming increasingly common, despite being nearly unknown just a few years ago. This type of attack is especially troublesome because it can by de facto take your entire network offline without ever attacking the actual network.
DNS servers can be protected with their own VPN-based system. To remain effective, the VPN solution must:
- Not slow down your operations (some solutions can even speed up DNS response times).
- Allow for easy and uninterrupted installation if you maintain your own DNS servers.
- Utilize DNS query reputation to screen traffic.
- Leverage rate-based heuristics to identify the most sophisticated attack methods.
- Include alternative methods like single IP protection if your company is small and doesn’t own its own C-Class subnet.
Adapting to the new DDoS landscape
The goals and motivations of DDoS attackers have remained consistent, but the methods they use are evolving quickly. Attackers are so confident that they often issue warnings to their targets as in the case for Pokémon Go. To protect your users and prevent your systems from becoming an easy target for threat actors, consider engaging the most up-to-date solutions.
To learn more about how your game company can protect itself from DDoS attacks, visit our resource center, or contact us and let us know how we can help.
Try Imperva for Free
Protect your business for 30 days on Imperva.










