Background: DDoS Attack on Major US banks
If you’ve been following the news, you are probably aware of a wave of DDoS attacks that recently hit several major U.S. banks. Izz ad-Din al-Qassam, a hacker group that claimed responsibility for these attacks, declaring them to be a retaliation for an anti-Islam video that mocked the Prophet Muhammad and a part an on-going ‘Operation Ababil’.
So far the attack caused several major disruptions in online and mobile banking services. Izz ad-Din al-Qassam assured that the cyber-attacks will continue, saying that ‘from now on, none of the U.S. banks will be safe from our attacks. ‘
Exposed Backdoor Shell Reveals Botnet Activity
Over the weekend, as the reports of the attack started to roll in, Incapsula security team noticed a suspicious behavior on one of the newly added websites. This client, a small and seemingly harmless general interest UK website, was suddenly a focal point of a rapidly increasing number of security events. The cause? Numerous requests with encoded PHP code payload.
A closer look revealed that these intercepted requests were attempts to operate a backdoor and use the website as a bot – an unwilling foot soldier in a DDoS army.
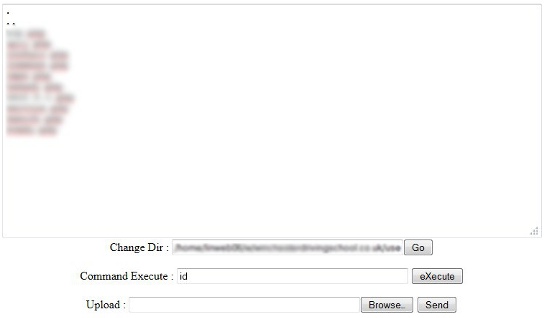
The backdoor was instructed to launch HTTP and UDP flood attacks against several U.S. banks, including PNC, HSBC and Fifth Third Bank.
Since the commands were blocked by our service the attack was mitigated even before it started, so we can’t be absolutely sure about the scope of damage this attack would cause. Still, it is safe to assume that it would be enough to seriously harm an average medium-sized website.
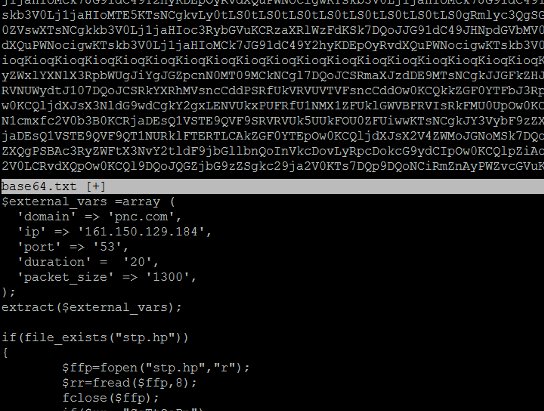
Origins of the Backdoor
The site has just recently joined our service, and it onboarded Incapsula already with the backdoor installed, so at first we couldn’t be sure just how it was hacked. Still, we didn’t stay in the dark for too long. As we examined scanner bot traffic on the site, the answer was pretty obvious. The administrative password was…
You guessed it: admin / admin.
Time Sharing Botnet Zombies
As we continued to monitor the incoming DoS commands we saw that the attacks were precisely timed, limited for periods that varied from 7 minutes to an hour. The Botnet C&C was commanding it to work in ‘shifts’, maximizing its efficiency and ordering it to renew the attack just as the target would start to recover. During some of these ‘shifts’ the backdoor was instructed to change target and attack unrelated commercial and e-commerce sites. This all led us to believe that we were monitoring the activities of a Botnet for hire.
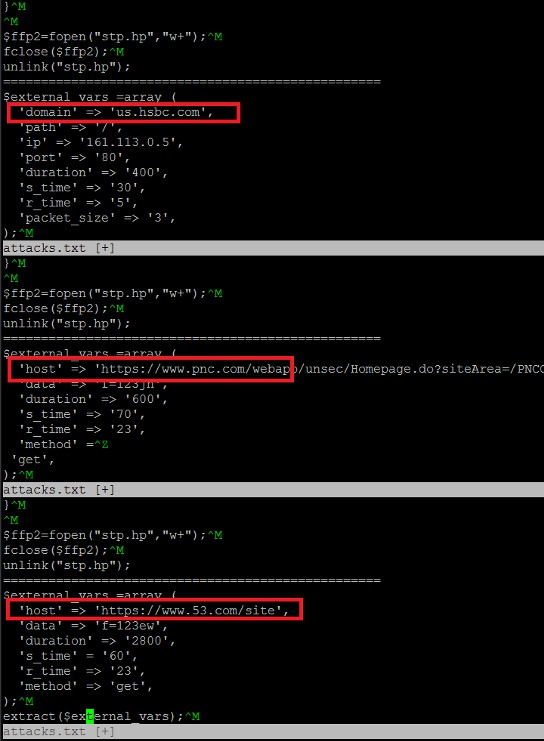
The use of a Web Site as a Botnet zombie for hire did not surprise us. After all, this is just a part of a growing trend we’re seeing in our DDoS prevention work. In an attempt to increase the volume of the attacks, hackers prefer web servers over personal computers. It makes perfect sense. These are generally stronger machines, with access to the high quality hoster’s networks and many of them can be easily accessed through a security loophole in one of the sites.
As we investigated the DoS events we also found some additional interest points:
- The PHP DoS code was designed to multiply itself, so it could take advantage of the full capacity available on the server. Since this is a server on hoster’s backbone, it was potentially capable of producing much more traffic volume than a regular ‘old school’ botnet zombie.
- The backdoor was controlled using an API, which used the server’s PHP environment to inject dynamic attack code. This allows the attacker to adapt very quickly to any changes in the websites security.
Tracing Back the Attacker
After getting all of the information we needed, we decided to follow back the trail of breadcrumbs which led us to a Turkish web design company. The website was used as Botnet C&C for the attack. While we can’t say for sure, but it looks like this website was also compromised and used as an additional buffer between the target and the real attacker.
Afterthoughts
This is just another demonstration of how security in the internet is always determined by the weakest link. Simply neglecting to manage administrative password in a small site in the UK, can be very quickly be exploited by Botnet shepherds operating obscurely out of Turkey to hurl large amounts of traffic at American banks. This is a good example of how we are all just a part of a shared ecosystem where website security should be a shared goal and a shared responsibility.
For more information about DDoS attacks and DDoS mitigation techniques you can visit our DDoS Center or inquire about Incapsula DDoS Protection Services.
Try Imperva for Free
Protect your business for 30 days on Imperva.