As an enterprise security company, our blog doesn’t typically focus on personal account breaches. That being said, if a new or interesting attack pops up we like to share it with our readers.
This is a story about how my Amazon account was broken into, likely as a result of me (stupidly) using similar passwords in different accounts—an annoying but common attack.
What happened next, however, changed it from a run-of-the-mill account breach into a story about perpetrators using registration bots to launch a smokescreen—an attack method I found extremely interesting.
Here is a description of the attack—I hope it’ll serve as a cautionary tale to fellow e-shoppers during this holiday shopping season.
A New Use for Registration Bots
I initially had no idea my Amazon account had been breached. In fact, I only noticed that something was odd when I opened Gmail one night and found hundreds of registration confirmations to numerous services I’d never heard of. What’s more, I was receiving a similar email every few seconds.
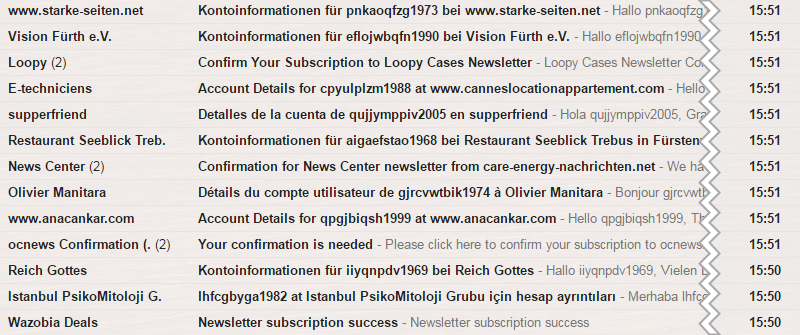
My instincts as a security researcher immediately kicked into gear.
First, I noticed that the registration email usernames followed a clear pattern. Each used a random string of nine or ten letters followed by four numbers. Second, I saw that I was steadily receiving five new emails every minute.
Both were clear signs of automation that used registration bots.
But why would someone suddenly decide to use my email for auto registration? If they were targeting a specific website, wouldn’t it be better to register using a dummy email account?
As part of my investigation, I flagged several messages as spam and let Gmail filter out the rest. After going over the messages, I noticed that many of the IPs associated with the registrations belonged to TOR exit nodes. This confirmed my suspicion that this was a malicious attack, as bot managers can’t be tracked within the TOR network.
When most of the noise had been cleared, I found an Amazon email hidden among the junk. It informed me that my purchase—one I hadn’t made—would be delivered within 24 hours.
After checking the Your Orders section of my Amazon account, I did find this: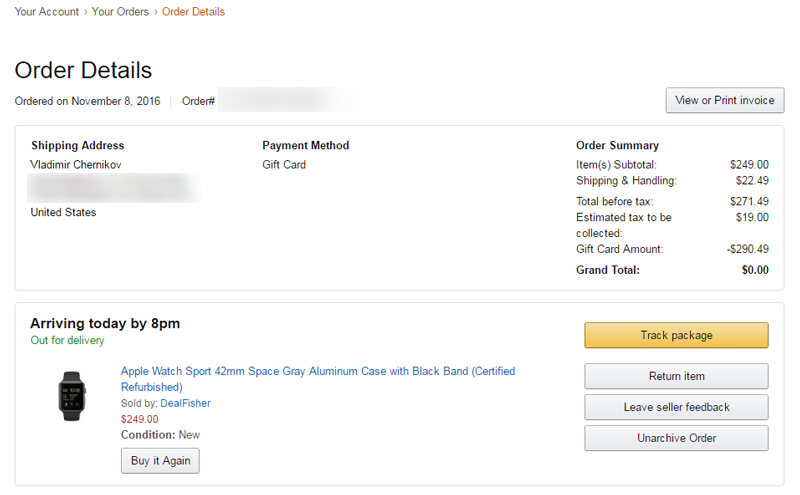
Obviously I have no idea who Vladimir Chernikov is. In fact, in this order only the $300 gift card used to pay for Vladimir’s Apple watch belongs to me.
Thankfully, Amazon customer service was very responsive. After explaining what happened they immediately cancelled the order and refunded my gift card. Still, because the order was placed with 24-hour shipping, it likely would have gone through if I hadn’t quickly cleared out my Inbox and found the shipping confirmation.
So What Happened Exactly
I’m pretty certain my Amazon account was breached some time ago, but the attackers hadn’t been able to do anything because my credit cards weren’t linked to my account. Once I got the gift card, however, they seized the opportunity.
The card wasn’t stolen right away. First registration bots mass subscribed me to thousands of sites, thereby flooding my Inbox with registration confirmations. Afterwards, the attackers used my gift card hoping I wouldn’t see Amazon’s message amid all the junk.
The diagram below illustrates the attack’s progression:
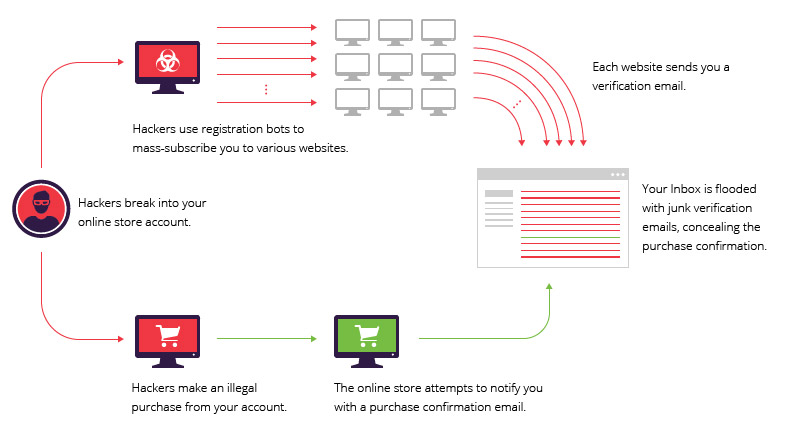
The attack was interesting because registration bots – typically used for brute force attacks – were employed to launch a smokescreen against a single user.
I also noticed that the method the attackers used to launch the smokescreen was very similar to a DDoS reflection attack. Here, the perpetrator initiates a multitude of fake requests in the target’s name, who is then swamped with unsolicited responses.
A Few Tips Going Forward
I hope this story encourages everyone to remain alert about any unusual activity they encounter online. For me, what originally resembled an email spam attack was actually a way to conceal a theft. This just goes to show that with cybercrime, things aren’t often as they appear.
I’d also like to use this opportunity to remind both users and website owners of some of the best practices for preventing attacks similar to the one I experienced.
- Use unique passwords – I don’t reuse passwords. However, I likely created an account some time ago and then used a similar password for my Amazon account. All it took was a database breach at the site for the attacker to obtain my email address and initial password. I can’t stress this enough—don’t reuse passwords and make sure that new ones are totally unique!
- Use two-factor authentication – Providing an extra layer of security, many online services, including Amazon, now offer two-factor authentication (2FA) to protect user accounts. Here an SMS message, containing a single-use account access code, is sent to your cell phone during the login process. Had I activated 2FA for my Amazon account, the attacker wouldn’t have been able to access it.
- Flag junk mail as spam – If you find your inbox flooded with junk mail, flag it as spam instead of deleting it. Doing so improves your spam filter and ensures similar messages are filtered accordingly, although it takes time (I still receive around 100 emails a day). Furthermore, certain email services make it easier to recover mistakenly deleted messages from your Spam folder than from your Trash folder.
- Filter registration bots – This tip is for site owners. Filtering registration bots can help prevent the attack described here, while also blocking any number of phony subscriptions to your service. This can be achieved by implementing Captcha as part of your registration process.
Try Imperva for Free
Protect your business for 30 days on Imperva.

















