As potential threats and entry points into organizations’ databases keep growing, so does the amount of money folks are throwing at detecting and actioning insider threats. In fact, the ballooning amount of money being spent on cybersecurity overall clearly highlights the seriousness with which businesses are tackling the problem in general.
Identifying and containing data breaches
Insider threats are a major concern for CISOs, and rightly so; professionals are concerned because insiders need legitimate access to data to do their work, so in most cases, they’re already embedded within an organization. Perhaps more terrifying is the time it can take to identify and mitigate breaches.
(Also, check out our Ovum whitepaper, “How Modern Database Security Complements Other Tools to Mitigate Risk,” where you’ll learn how to integrate data protection features such as DAM, data discovery, security analytics and data masking with your IAM, DLP and SIEM tools for the strongest protection possible.)
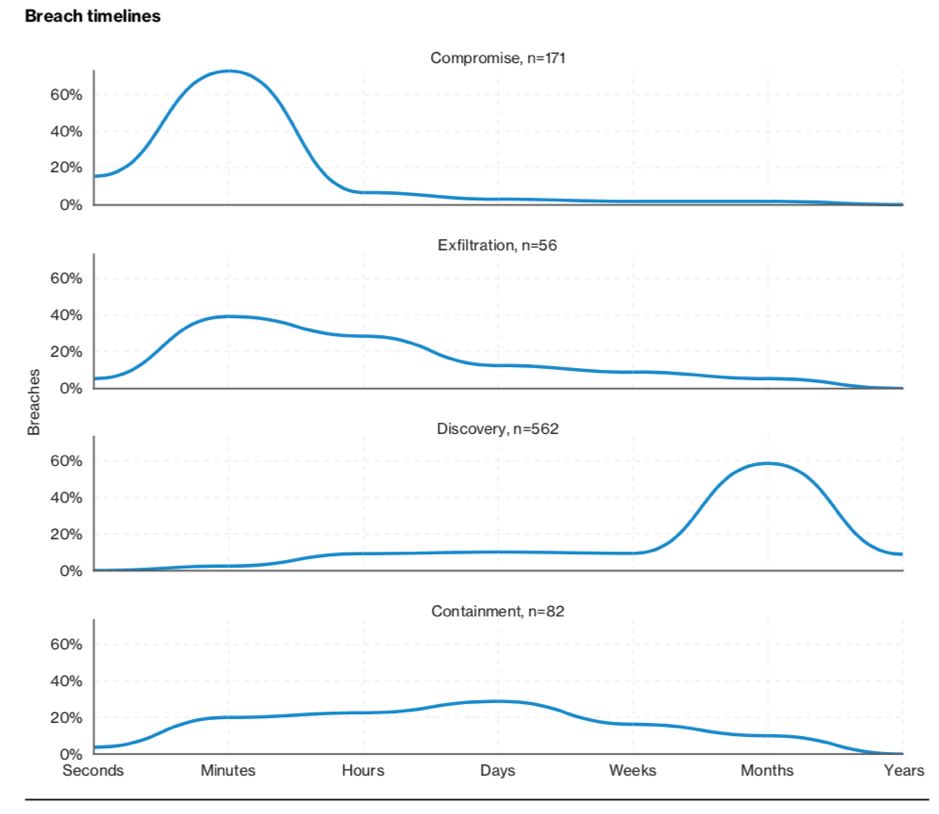
According to Verizon’s 2018 Data Breach Investigations Report (DBIR), almost 60% of data breaches take months to detect, and even then, more than 20% take several days to begin actioning.
What does an insider threat look like?
Well, for one it’s not a Tinker, Tailor, Soldier Spy kind of a situation, not when it comes to day-to-day data security anyway. As a matter of fact, the very reason they’re so hard to detect is that these users all have legitimate credential and data access. They already have access to sensitive database areas, sensitive file shares; and — more importantly, for those regulations that suggest we rely on encryption of data — these employees often have access to the data we encrypt but have the right to decrypt the data, much like most applications.
So, if you were to pull off an insider attack, how would you do it?
In a recent survey of 179 IT professionals, a staggering 43% said they believe they could execute a successful attack on their own organizations. Only a third believe it would be difficult or impossible to carry out a successful insider theft and just 22% say they would have a 50/50 chance.
With the increasingly blurred line between work and home life, and more pressingly, work devices; the ease with which insider threats can carry out attacks continues to grow. Many companies issue employees a networked laptop or smartphone as standard. Now, while this is a necessary business function, it could have potentially devastating consequences where data security is concerned. When asked to put themselves in the shoes of a malicious insider, 23% of security professionals said they would use their company-owned laptop to steal information from their company, while 20% said their personal computer, and 19% said their laptop.
The good news is that our survey also suggests that nearly two-thirds of organizations have a solution which allows them to detect malicious insiders, while 79% percent of organizations would have a way to tell if their employees were accessing something they shouldn’t; this is, however, caveated with another, suggesting 33% of organizations would take weeks or months to discover an employee had gone malicious, while 14% would never know.
Insider threats are hard to detect because people deliberately try to fly under the radar. That’s why you need to monitor who is accessing what data, and how that user is using the data. In the meantime, data access analytics will create a contextual behavior baseline of user data access activity and pinpoint risky or suspicious data access.
Try Imperva for Free
Protect your business for 30 days on Imperva.











