We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018. Organizations that fail to comply could face fines of up to €20M (roughly $22M) or 4 percent of their annual global turnover from the prior year and we’ll soon see just how EU regulators will enforce the GDPR regulations.
One of the more notable provisions of the GDPR is Article 33 or the mandatory 72-hour breach reporting requirement. Article 33 dictates that, in the event of a personal data breach, data controllers notify the appropriate supervisory authority “without undue delay and, where, feasible, not later than 72 hours after having become aware of it.” We recently launched a new infographic that summarizes the various requirements and response mechanisms related to this rule, and we’ll aim to now help you break down the requirements under the rule, and how to effectively prepare.
(Also, check out our Gartner report, “How to Use the Data Security Governance Framework,” where you’ll learn how to use data security strategies to mitigate the risks caused by security threats, data residency and privacy issues such as GDPR.)
72 Hour Countdown
Simply put: Under GDPR requirements, organizations have just 72 hours to gather all related information and report data breaches to the relevant regulator. This is a significant undertaking for any organization and involves the development and provisioning of a comprehensive containment plan. Here’s a simple example:
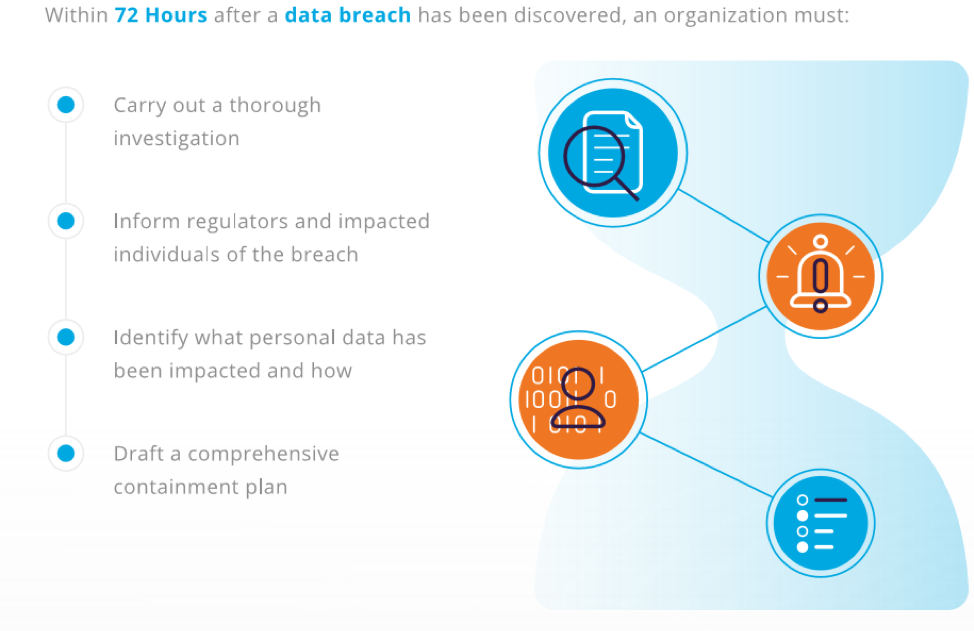
The steps are pretty clear: Carry out an investigation, quickly inform regulators and individuals of a breach, and be specific with respect to what data was impacted and how the issue will be addressed moving forward… all within 72 hours. It’s worth noting that if — for whatever reason — a notification is not made within the 72-hour window, the GDPR requests that the controller provide reasonable justification for the delay; potentially adding additional disruption to regular business operations and exasperating administrative hassle.
GDPR Article 33 also specifies what type of information the notification must include. At a minimum, the data protection authority will expect to see:

Clearly, the information expectations are high, and the timeline is quite short- thereby posing a significant challenge to the organization as it scrambles to meet the requirements while trying to simultaneously address the issues associated with the breach and maintain ongoing operations.
Further, for security teams, in particular, the challenge of identifying data breaches becomes even more pressing, given that many data breaches are not discovered for weeks, months and sometimes years. Even then, once breaches are discovered, understanding the impact and reporting in accordance with the Article parameters – i.e., who’s been affected, what data was breached, how it happened, and how to remediate the situation – within 72 hours may be a daunting task.
So, what can organizations do to navigate the GDPR’s data breach notification requirements and minimize their impact? Put differently, how can they reduce the risk and fallout associated with a data breach and the subsequent 72-hour reporting notification requirements:
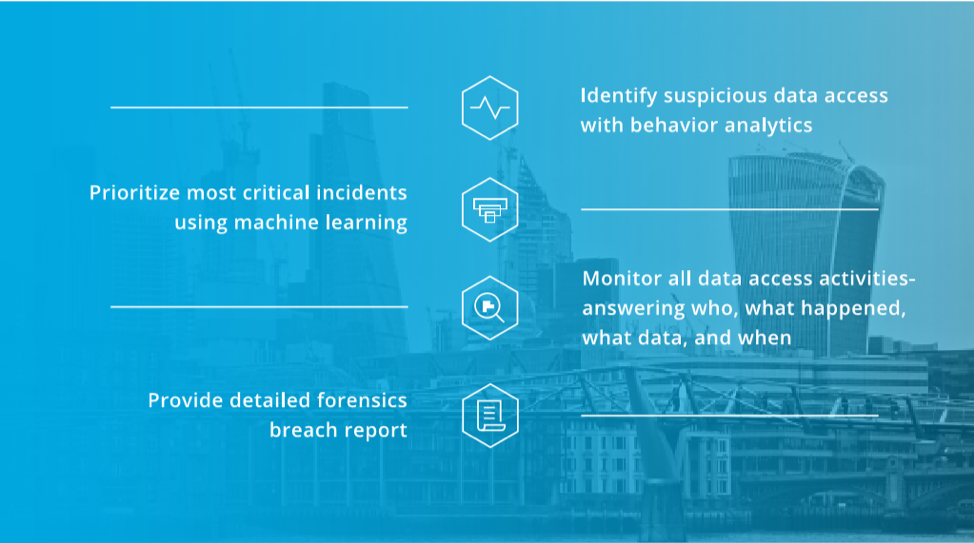
Identify Suspicious Data Access
To ultimately detect and report on a data breach you need to be able to answer the question of whether or not your data has actually been accessed, and if the access is truly suspicious in nature. Therefore, it is important to have a handle on the appropriate approvals, intent, and actions of every user within your organization to ensure internal and approved/intentional users, and unintentional insider threat risks are accounted for. You need to fully understand what users are doing with enterprise data, so you don’t miss the vital context associated with a breach incident.
Detecting suspicious data access can be challenging, as organizations have to give employees access to data to perform their job. The key lies in implementing appropriate policy, process, training, and technologies to help determine what authorized, day-to-day data access looks like, and detect anything that might be abusive.
Prioritize and Categorize True Incidents
Today’s security teams are typically inundated with information and alerts related to activity and incidents associated with data access and use within an organization. With privacy requirements and industry regulations such as GDPR tightening the reigns and requiring transparency and detailed reporting on data breaches; the ability to effectively (and efficiently) sift through volumes of daily alerts to determine which qualify as a ‘true’ incident becomes critical. Furthermore, in many cases, security professionals do not have the context needed to identify and prioritize critical incidents as they’re not database experts and don’t have deep knowledge of what is and isn’t okay.
This is where database monitoring technology, machine learning, data access processes and analytics come into play. Understanding access requirements and processes and leveraging purpose-built technologies to enable the implementation and monitoring thereof help to easily distill billions of data access events into a small number of ‘real’, actionable, high-value events. They improve the fidelity of alerts and allow you to focus on incidents that matter, reducing the time it takes to investigate potential breaches and increasing the effectiveness of security teams. Trying to accomplish this without the aid of technology comes with an increased cost, resource time, and risk.
Monitor & Log Access and Activity
Monitoring is a key piece of the puzzle in terms of adhering to the 72-hour rule; that is, the monitoring and detecting of incidents, and the effective and efficient reporting of those that are material and true under the requirements of GDPR. In order to determine whether data access and activity is good or bad, companies need to continuously monitor data access and capture/record/log those events — which will also serve organizations well with respect to their reporting and proof of best efforts in the event of a data breach and GDPR compliance violations.
The question is: how can you determine if something is good or bad if you don’t even know about it? The key is database monitoring as it provides a critical foundation that gives you the necessary visibility and confidence that your data is secure, and your compliance is in check. It’s not a simple exercise, however, as you need to monitor all users, including applications that access data and privileged users, and all databases… ALL THE TIME.
Sure, this can be a daunting task, but one that can be augmented greatly with effective data security tools like database monitoring and activity reporting technologies. The ability to accurately monitor, detect, and prioritize access and activity is the key to accelerate breach detection without causing business disruption. In the meantime, the solution can automatically collect all the breach details and allow you to provide a detailed report internally and to the regulator under the provisions of the 72-hour requirement.
Provide the Forensic Report
Additionally, GDPR requires that data controllers document not only the facts relating to the breach but also its effects and all related impact information and remedial action taken; and then report all of this activity in writing. As previously outlined, Article 33 requires the reporting of specific information related to the breach, including (among other things):
- The nature of the breach
- The likely impact and consequences of the breach
- The measures taken or proposed to be taken by the data controller to address the breach and mitigate its adverse effects
The information needed to support this requirement comes in the form of a forensic report, conducted either internally, or by third-party expert support. The forensic report is what the investigators provide and helps organizations understand how the attack happened, what vulnerabilities were exploited, what data was compromised, etc. By continuously and effectively monitoring and logging all data access, organizations can better understand the specifics of what was compromised, by whom, and how in a much quicker fashion; thereby shortening investigation time and compliance with the 72-hour requirement.
Technologies to Support Compliance
Supporting GDPR compliance overall, and the requirements under Article 33 requires a variety of process and procedure enhancements, along with a robust and multi-layered data security strategy- one that leverages robust, proven, and GDPR-supportive technologies.
Imperva offers a host of data security solutions that can help with these challenges and support your efforts in better monitoring your data and suspicious activities, helping shorten both identification and investigation times. This is now made even easier with our out of the box GDPR monitoring compliance capabilities and a robust reporting set that provides details on who accessed what data and when. Effectively implementing these tools will get you on the right track as you prepare for the 72-hour GDPR breach notification requirements.
Contact us to learn more about Imperva’s GDPR compliance capabilities and explore our data security solutions in detail.
More on the GDPR:
- GDPR Series, Part 1: Does the GDPR Apply to You?
- GDPR Series, Part 2: What Rules Require Data Protection Technology?
- GDPR Series, Part 3: Preparing Your Organization for the GDPR
- GDPR Series, Part 4: The Penalties for Non-Compliance
Try Imperva for Free
Protect your business for 30 days on Imperva.












