Ever since March 28th, when Drupal published a patch for a RCE named Drupalgeddon 2.0 (SA-CORE-2018-002/CVE-2018-7600), Imperva has been monitoring our cloud looking for hackers’ attempts to exploit the vulnerability, but found nothing. Until today.
It somehow seems fitting that nefarious activity picked up today, Friday the 13th. After a POC exploit was released, our monitoring services showed that hackers are finally starting to catch up! Since the RCE exploit was publicly disclosed two weeks ago, they could have been working on their own exploits, but didn’t.
Lazy Hackers
As usual when exploits become known, we go into hyper-awareness mode looking for security events (and of course, protecting our customers), but no events were identified. Not a single attack. We rang to some of our teammates looking for answers, asking if they deleted events, but no—it’s just simply that no one attempted to exploit this newfound bug and it took them two whole weeks to reverse the patch.
It appeared every one of the black hats was waiting for someone else to do the research and share the exploit. Perhaps most hackers don’t care for the actual work of finding ways to exploit a vulnerability. They just wait until something is public and then use it to attack. Before that, we saw almost no traffic whatsoever!
Attack Data
The chart below is just the beginning of the numbers we’re now seeing in our cloud, and they are continuing to rise (Figure 1).
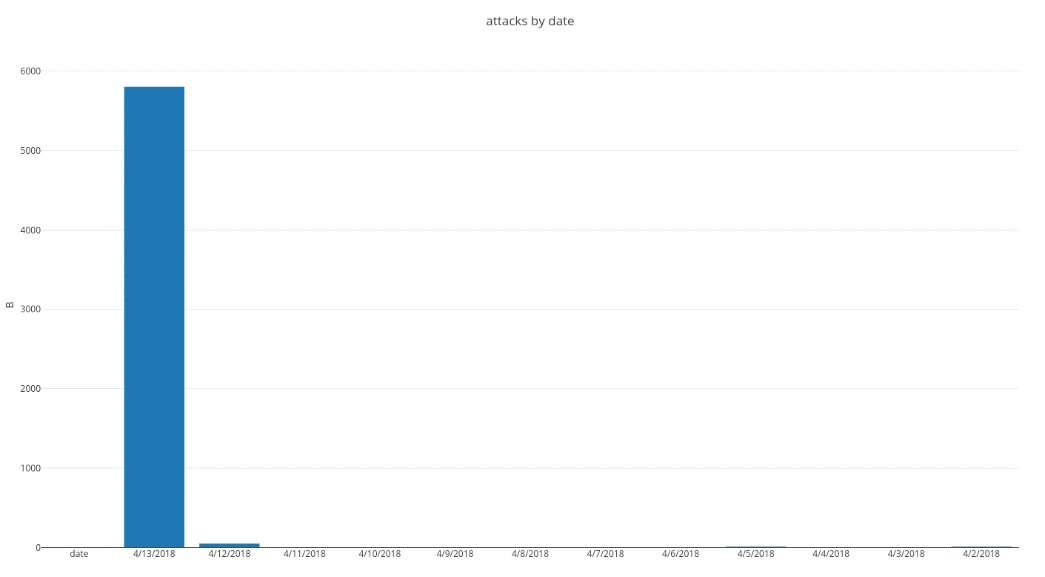
Figure 1: Attacks by date
To this point, we have seen 90% of the attack attempts are scanners, 3% are backdoor infection attempts, and 2% are attempts to run crypto miners on the targets (Figure 2).
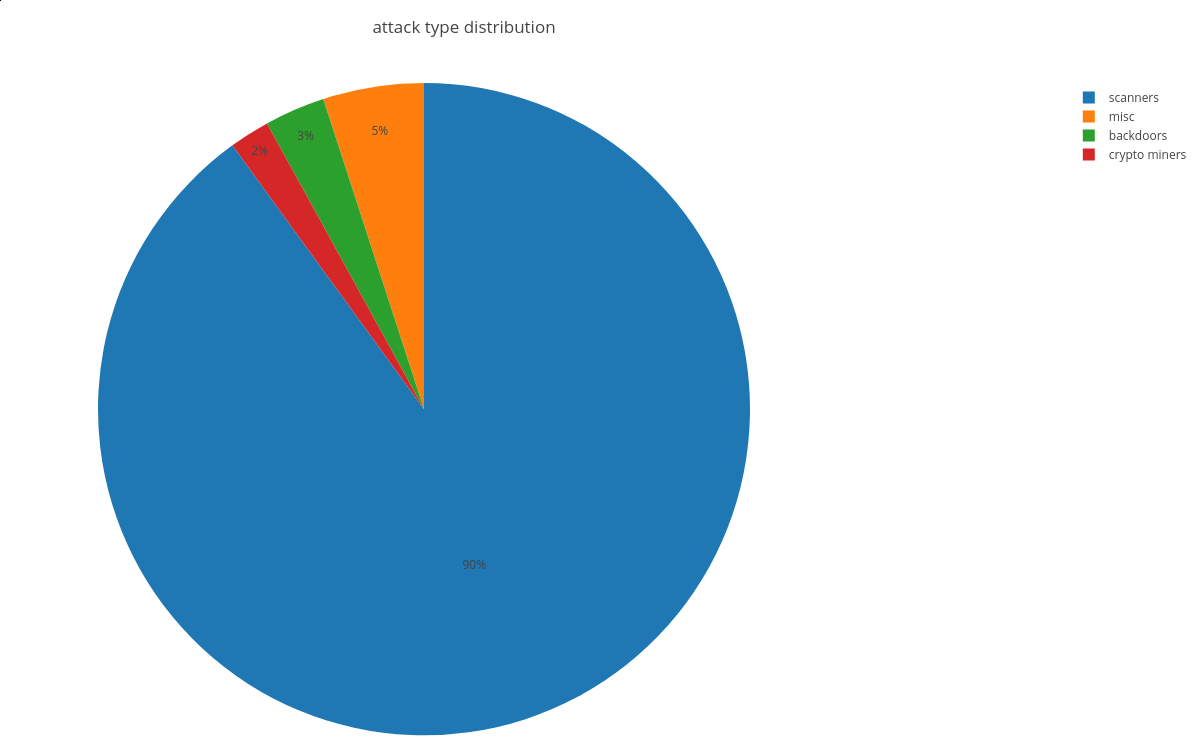
Figure 2: Attacks by distribution type
Also, most of the attacks originated from the US (53%) and China (45%) (Figure 3).
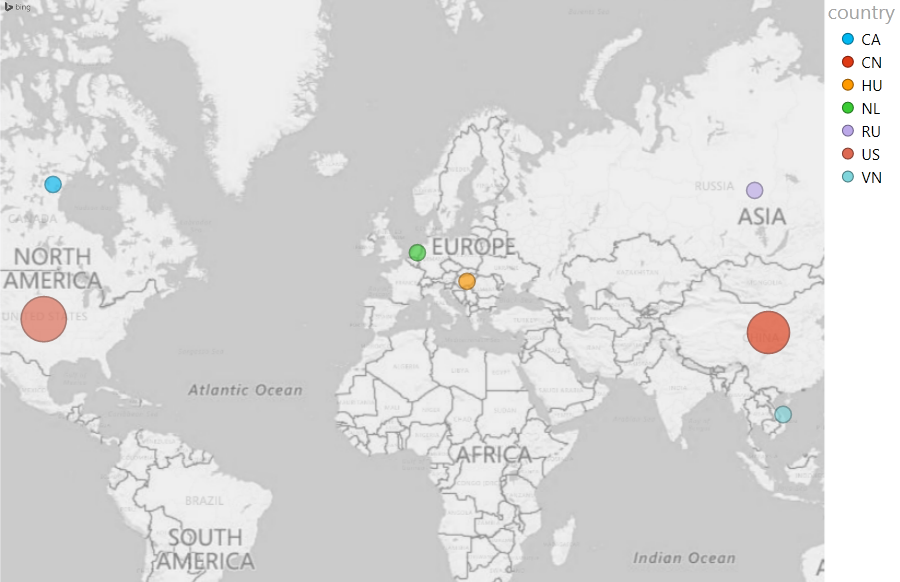
Figure 3: Location source of attacks
Imperva Customers Protected
We applied a virtual patch to Imperva SecureSphere and Incapsula WAF customers within hours of identifying the RCE vulnerability.
In addition to our zero-day protection rules that spotted this attack, we also published a new dedicated security rule to provide maximum protection to Imperva SecureSphere and Incapsula WAF customers against this vulnerability.
Try Imperva for Free
Protect your business for 30 days on Imperva.














