It’s that time of the year when we look back at the tech trends of 2017 to provide us with a hint of things to come. Accordingly, let’s engage in our favorite end-of-year pastime: predictions about the coming year.
Equipped with Imperva’s own research, interactions with our customers, and a wealth of crowdsourcing data analyzed from installations around the world, we’ve looked ahead to the future of cybersecurity and compiled a few significant trends IT security pros can expect to see in 2018.
Here are our top five predictions for 2018 and what you can do to prepare for them:
1. Massive Cloud Data Breach
Companies have moved to cloud data services faster than anticipated even in traditional industries like banking and healthcare where security is a key concern. As shown in Figure 1, take-up of cloud computing will continue to increase, attaining a compound annual growth rate (CAGR) of 19%, from $99B in 2017 to $117B in 2018.
In 2018, in parallel with the take-up of cloud computing, we’ll see massive cloud data breaches—primarily because companies are not yet fully aware of the complexities involved with securing cloud data.
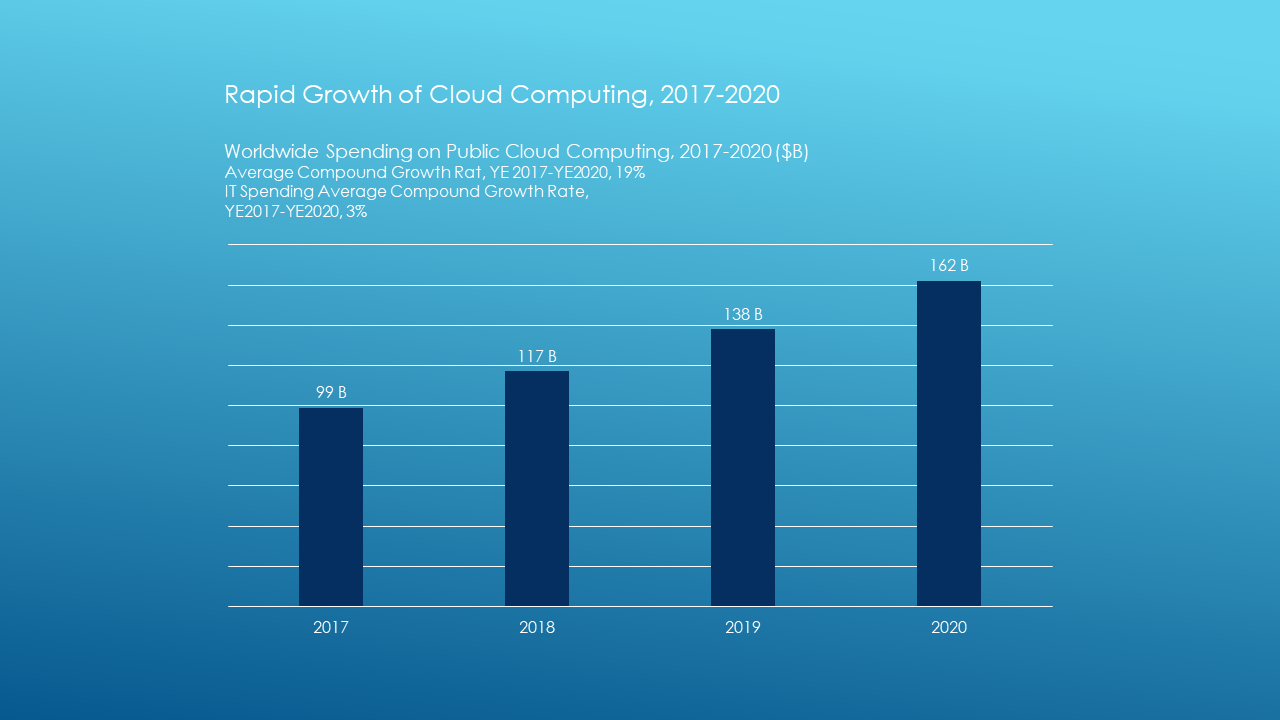
Figure 1: Rapid Growth of Cloud Computing (Source: IDC)
Data Breaches: A Troubling Past, A Worrying Future
It is estimated that in 2017 alone, over 99 billion records were exposed because of data breaches. Of the various circumstances behind the breaches, hacking of IT systems is by far the most prevalent cause, followed by poor security, inside jobs, and lost or stolen hardware and media.
Major breaches at healthcare and financial services companies indicate a growing trend of vulnerabilities and exploits in these two vital business sectors.
Healthcare was one of the hardest hit sectors in 2017, and that trend is expected to worsen in the coming year. Some 31 million records were stolen, accounting for 2% of the total and up a whopping 423% from just 6 million.
The financial services industry is the most popular target for cyber attackers (see Figure 2), and this dubious distinction is likely to continue in the upcoming year. Finance companies suffered 125 data breaches, 14% of the total, up 29% from the previous six months.
Data breaches in various other industries totaled 53, up 13% and accounting for 6% of the total. The number of records involved in these attacks was a staggering 1.34 billion (71% of the total) and significantly up from 14 million.
It is estimated that the average cost of a data breach will be over $150 million by 2020, with the global annual cost forecast to be $2.1 trillion.
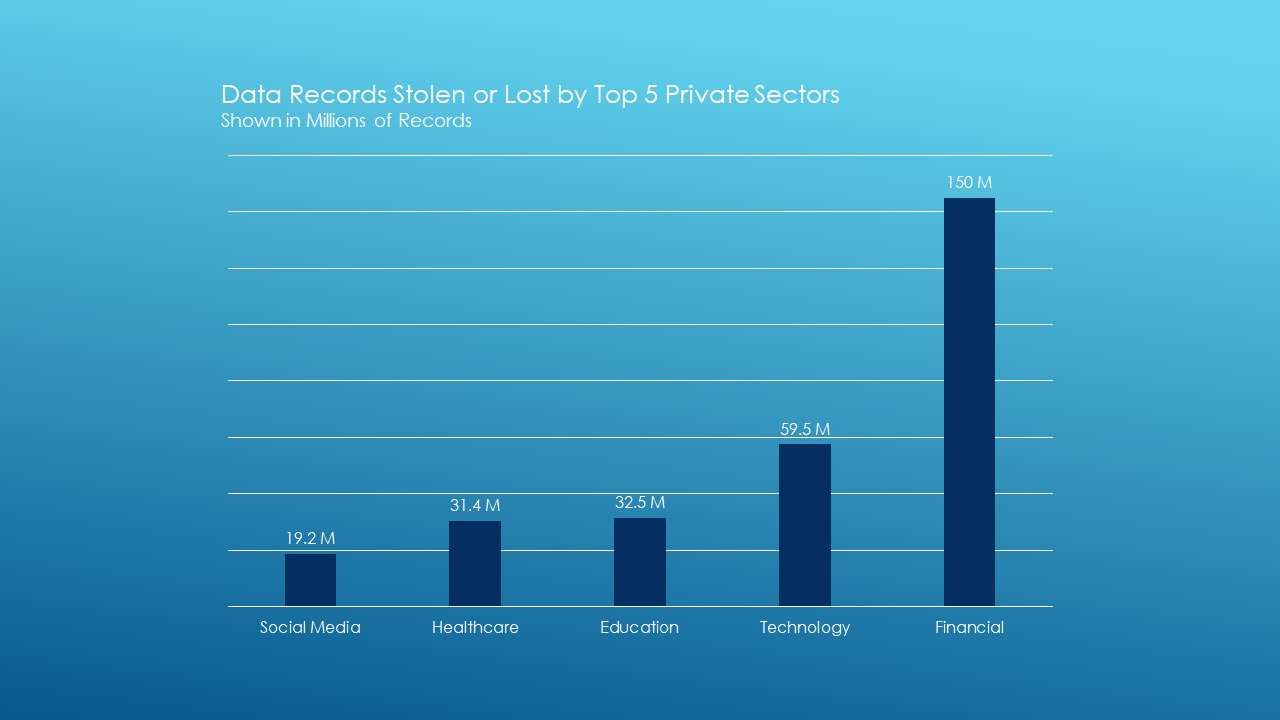
Figure 2: Data Records Stolen or Lost by Sector (Source: IDC)
Critical Cloud-based Security Misconfigurations
Missteps in cloud-based security configurations often lead to data breaches. This is likely to increase as more organizations move some or most of their operations to the cloud.
As organizations and business units migrate to public cloud services, centralized IT departments will find it increasingly difficult to control their company’s IT infrastructure. These enterprises lack the visibility necessary to manage their cloud environments and don’t have the monitoring tools to detect and report on security governance and compliance. Many are not even aware of the specific workloads they’ve migrated to the cloud. And without a doubt, you can’t secure what you can’t see.
For example, an unsecured Amazon Web Services S3 storage bucket has been an ongoing concern for cloud users. The bucket, which can be configured to allow public access, has in the past leaked highly sensitive information. In one instance of a major security breach, a whopping 111 GB worth was exposed, affecting tens of thousands of consumers.
Most significantly, Amazon is aware of the security issue, but is not likely to mitigate it since it is caused by cloud-user misconfigurations.
2. Cryptocurrency Mining
We expect to see a growth of cryptocurrency mining attacks where attackers are utilizing endpoint resources (CPU/GPU) to mine cryptocurrency either by cross-site scripting (XSS) or by malware. It’s increasingly likely that remotely vulnerable/hackable IoT devices will also be used as a mining force to further maximize an attacker’s profits.
Illegal mining operations set up by insiders, which can be difficult to detect, are also on the rise—often carried out by employees with high-level network privileges and the technical skills needed to turn their company’s computing infrastructure into a currency mint.
These attacks will quickly grow in popularity given their lucrative nature. As long as there is a potential windfall involved, such inside jobs are likely to remain high on the list of cybersecurity challenges faced by companies.
Although attacks that attempt to embed crypto-mining malware are currently unsophisticated, we expect to see an increase in the sophistication of attacks as word gets out that this is a lucrative enterprise. We also expect these attacks to target higher-traffic websites, since the potential to profit increases greatly with higher numbers of concurrent site visitors.
3. Malicious Use of AI/Deception of AI Systems
The malicious use of artificial intelligence (AI) will continue to grow quickly. The industry has started to see early traces of attackers leveraging AI to learn normal behavior and mimic that behavior to bypass current user and entity behavior analytics (UEBA) solutions. It’s still very early stage and will continue to mature beyond 2018. However, it will force current UEBA vendors to come up with a 2.0 approach to identifying anomalous behavior.
AI and internet of things (IoT) use cases drive cloud adoption. Artificial intelligence in the cloud promises to be the next great disrupter as computing is evolving from a mobile-first to an artificial intelligence-first model. The proliferation of cloud-based IoT in the marketplace continues to drive cloud demand, as cloud allows for secure storage of massive amounts of structured and unstructured data central to IoT core functions.
Without proper awareness and security measures, AI can be easily fooled by adversarial behavior. In 2018 we will see more:
- Attacks on AI systems (for example, self-driving cars)
- Cyber attackers who adapt their attacks to bypass AI-based cybersecurity systems
4. Cyber Extortion Targets Business Disruption
Cyber extortion will be more disruption focused. Encryption, corruption, and exfiltration will still be the leaders in cyber extortion, but disruption will intensify this year, manifesting in disabled networks, internal network denials of service, and crashing email services.
In the last few years, attackers have adopted a “traditional” ransomware business model—encrypt, corrupt or exfiltrate the data and extort the owner in order to recover the data or prevent it from leaking. Fortunately, techniques such as deception or machine learning have helped to prevent these types of attacks and made it more difficult for attackers to successfully complete a ransomware attack.
From a cost perspective, most of the damage associated with ransomware attacks is not the data loss itself, since many firms have backups, but the downtime. Often in the case of ransomware, attackers will start to leverage a disrupt-and-extort method. DDoS is the classic and most familiar one, but attackers will probably adopt new techniques. Examples include shutting down an internal network (web app to a database, point-of-sale systems, communication between endpoints, etc.), modifying computer configuration to cause software errors, causing software crashes, system restarts, disruption of your corporate email or disruption of any other infrastructure which is mandatory for an organization’s employees and/or customers day-to-day functions. Basically, any event that leaves the company unable to conduct business.
While absolute protection is impossible, you can help lower your chance of business interruption due to a cyber-attack. Start by creating a formal, documented risk management plan that addresses the scope, roles, responsibilities, compliance criteria and methodology for performing cyber risk assessments. This plan should include a characterization of all systems used at the organization based on their functions, the data they store and process, and their importance to the organization.
5. Breach by Insiders
Businesses are relying more on data which means more people within the business have access to it. The result is a corresponding increase in data breaches by insiders either through intentional (stealing) or unintentional (negligent) behavior of employees and partners.
While the most sensational headlines typically involve infiltrating an ironclad security system or an enormous and well-funded team of insurgents, the truth of how hackers are able to penetrate your system is more boring: it’s your employees.
A new IT security report paints a bleak picture of the actual gravity of the situation. Researchers found that IT workers in the government sector overwhelmingly think that employees are actually the biggest threat to cybersecurity. In fact, 100% of respondents said so.
Fortunately, security-focused companies have begun identifying these traditionally difficult to detect breaches using data monitoring, analytics, and expertise. The difference being that in 2018, more companies will invest in technology to identify this behavior where previously they were blind.
In fact, 75% of IT employees in government reported that rather than their organization having dedicated cybersecurity personnel on staff (which is becoming more and more necessary with each passing year), an overworked IT team was left to deal with security and employee compliance. As a result, 57% reported that they didn’t even have enough time to implement stronger security measures while 54% cited too small of a budget.
Here’s another fact for you: insider threats are the cause of the biggest security breaches out there, and they are very costly to remediate. According to a 2017 Insider Threat Report, 53% of companies estimate remediation costs of $100,000 and more, with 12% estimating a cost of more than $1 million. The same report suggests that 74% of companies feel that they are vulnerable to insider threats, with seven percent reporting extreme vulnerability.
These are the steps every company should take to minimize insider threats:
- Background checks
- Watch employee behavior
- Use the principle of least privilege
- Control user access
- Monitor user actions
- Educate employees
Insider threats are one of the top cybersecurity threats and a force to be reckoned with. Every company will face insider-related breaches sooner or later regardless of whether it is caused by a malicious action or an honest mistake. And it’s much better to put the necessary security measures in place now than to spend millions of dollars later.
Join Imperva on January 23rd for a live webinar where we’ll discuss these trends in more detail and review the security measures necessary to mitigate the risks. Register to attend today.
Try Imperva for Free
Protect your business for 30 days on Imperva.












