Today we are releasing our latest Global DDoS Threat Landscape Report, a statistical analysis of 5,765 network and application layer DDoS attacks mitigated by Imperva Incapsula services during Q3 2017.
Before diving into the report’s highlights, it should be mentioned that this quarter was marked by an adjustment to our methodology, which reflects the changes we’ve observed in the threat landscape for the past few quarters.
Specifically, we readjusted the definition of a DDoS attack to compensate for the growing prevalence of short-lived repeat assaults. We also significantly expanded the scope of our analysis, more than doubling the data points in our report.
Read the full report >>
For a more detailed overview of our new methodology and sampling methods, click here.
Report Highlights
Bitcoin was one of the most targeted industries
This quarter, 3.6 percent of network layer DDoS attacks targeted bitcoin exchanges and a related sites on our service. As a result, the relatively small and young industry made the top-10 attacked industry list.
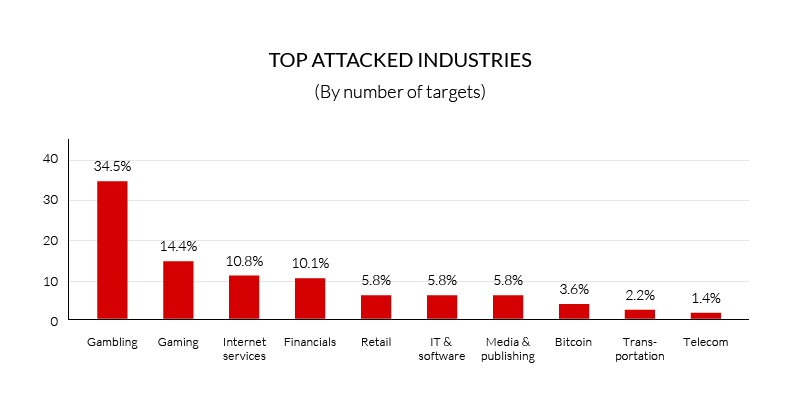
The campaign against bitcoin exchanges exemplifies the way DDoS offenders are drawn to successful online industries, especially new and under-protected ones.
From extortionists that launch ransom DDoS attacks, to more professional offenders working as hired guns for competitors, DDoS attackers are always “following the money”. In this specific case, DDoS attacks could also be attempt to manipulate bitcoin prices, a tactic attackers have been known to use in the past.
Organizations in the cryptocurrency industry and other high-growth digital fields should take notice.
High Packet Rate Attacks Grow More Common
Q3 2017 saw the number of high packet rate, network layer attacks—assaults in which the packet-forwarding rate escalated above 50 Mpps—continue to grow, reaching five percent.
What’s more, 144 attacks went above 100 Mpps, while the highest rated assault of the quarter peaked at 238 Mpps, up from 190 Mpps in Q2 2017. In comparison, in Q1 2017 we mitigated only six DDoS attacks that escalated above the 100 Mpps mark.
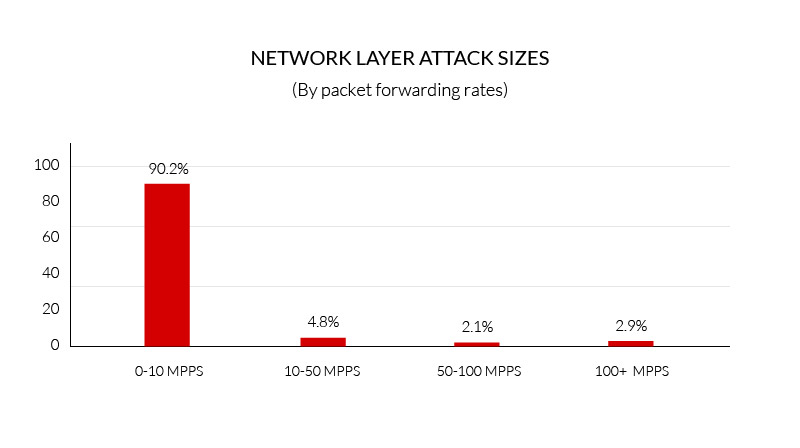
This paints a worrisome picture, as not all mitigation solutions are able to handle attacks at this rate.
Faced with the steep increase in the number of high packet rate attacks, mitigation vendors should upgrade their scrubbing equipment, as we recently did ourselves when we introduced the Behemoth v2 scrubbers, which have a 650 Mpps processing capacity.
Buyers are also not exempted from responsibility, and it’s up to them to inquire about the processing capability of the mitigation solution they’re about to purchase.
Network Layer Attacks Are Extremely Persistent
In Q3 2017, half of network layer targets were attacked at least twice, while nearly a third were hit more than ten times.
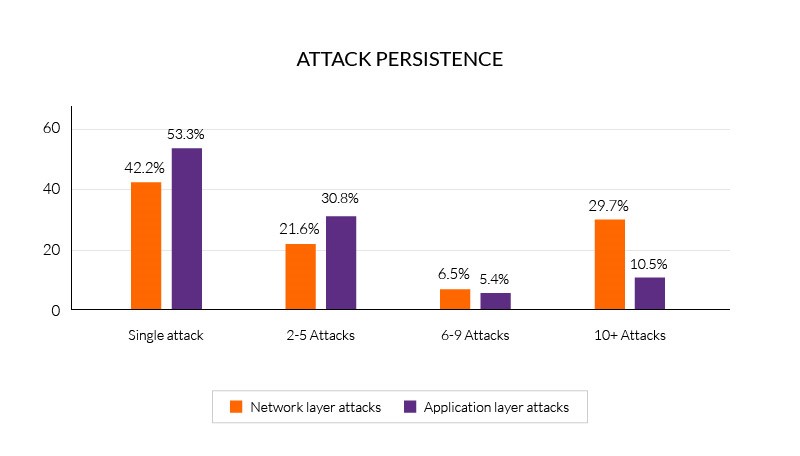
Repeat application layer attacks dropped from 75.8 percent to 46.7 percent quarter over quarter, largely because of how we now measure individual DDoS events. Even with these changes, however, Q3 2017 saw nearly 16 percent of targets exposed to six or more attacks.
These statistics are a reminder of something that most businesses targeted by DDoS attacks already know: if you’re hit once, chances are that you’ll be hit again. Considering how relatively easy and cheap it is to mount multiple attacks, most offenders won’t hesitate to stage repeat assaults, even after several attempts have been blocked by a mitigation provider.
This also highlights the need for a hands-off DDoS protection solution, the kind that doesn’t require an IT department to go into ‘alert mode’ every time an attack hits. Otherwise, the implication of multiple repeat attacks can be dire—not necessarily due to a domain or service going down, but because of work routine disruptions and important inner processes being brought to a halt.
Botnet Activity Out of India and Turkey Continues to Grow
Following an increase in Q2 2017, Indian and Turkish botnet traffic continued to rise this quarter. In India, traffic more than doubled from 1.8 percent in the prior quarter to 4.0 percent in Q3 2017. The uplift was even more dramatic for Turkey, where botnet activity more than tripled from 2.1 percent to 7.2 percent quarter over quarter.
In total, India and Turkey represented more than ten percent of total botnet activity this quarter and were home to more than five percent of all attacking devices. Also appearing on the short list of attacking counties are the more common culprits, including Russia, the US and Vietnam.
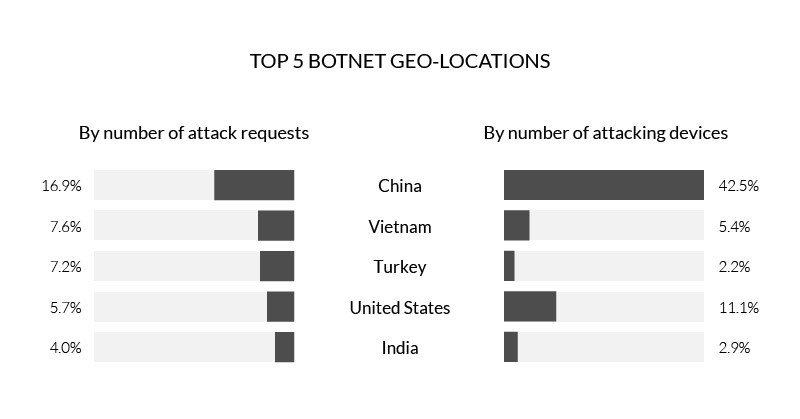
So far, we are unable to attribute the increased activity out of India and Turkey to any particular botnet, type of malware or attacking device. We’ll continue to monitor the situation and, if the trend continues, will allocate further resources to try and identify the reasons behind the uptick in botnet activity in the two countries.
Short-lived Attacks Drive Methodology Changes
Security researchers have different methods for classifying when a DDoS attack has taken place. Some count every attack individually, while others view a string of assaults as a single event. The differences largely come down to defining when an attack has started and when it has stopped.
In previous reports, using a methodology that dates back to 2015, we considered a quiet (attack-free) period of at least ten minutes to mark the end of an assault.
Over the last year, however, we witnessed a growing number of cases (e.g., pulse wave assaults) in which perpetrators launched attack bursts in rapid succession, thereby rendering the old way of measuring individual assaults less reliable. At times, this caused several DDoS bursts occurring only slightly more than 10 minutes apart to be considered as separate attack events.
In response, we updated our methodology’s quiet period from ten minutes to 60 minutes. This allows us to better aggregate successive attacks against the same target, significantly minimizing statistical bias towards repeated short-lived attacks.
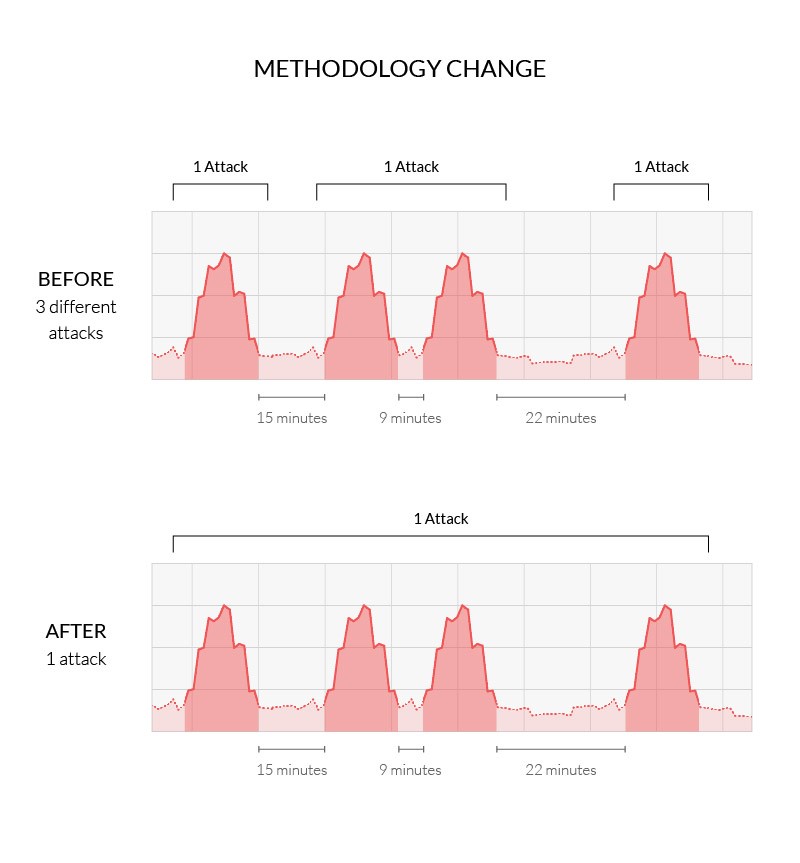
Changing our methodology was also an opportunity to revamp our sampling methods and expand the scope and quality of the information we provide.
The result, following a substantial investment in manpower and resources, is a report that is not only easier to read and navigate but is also more than twice as detailed as its predecessors; now showing 19 data points, compared to nine before.
These new data points include:
- Analysis of network layer attack persistence
- Statistics about network layer attack rates and sizes
- Information about the most attacked industries
- And more
Thank You for Your Support
In the past few years, these quarterly reports, which started out as a modest attempt to share some insights into our work, have become a useful source of information for members of the media and fellow security researchers.
With the new changes to our methodology, we aim to elevate the quality of the information we share and to provide more valuable and accurate information to our readers, customers and industry colleagues.
On behalf of everyone involved in this project, I would like to sincerely thank you for your interest and support.
I also invite you to use the comments section below to share your thoughts about the recent changes we’ve made and how our reports could be further improved.
Try Imperva for Free
Protect your business for 30 days on Imperva.










