In today’s knowledge-driven economy, modern enterprises have a fluid organizational structure in which most employees have access to most data to do their jobs. Working groups are formed organically and are cross-functional by nature. The amount of unstructured data organizations create is growing exponentially. Traditional, black and white file access control can’t keep pace with the ever-changing environment. This creates a security gap in which data contained in files can be lost, stolen or misused by malicious, careless, or compromised users.
Almost any security team will confirm that the traditional static approach to file security, centered on individually granting users access to files based on their department and function, is not effective because it places too much of an administrative burden on enterprise IT teams. Setting up, maintaining and enforcing permissions to grant and deny access has proven to be ineffective when it comes to securing enterprise files.
A new Hacker Intelligence Initiative (HII) report based on research from the Imperva Defense Center reveals three primary reasons why the traditional approach to file security no longer works. We review each of them below, as well as introduce a new way to secure files in today’s dynamic, modern enterprise.
Permissions are granted, but rarely revoked
A key problem is that file permissions are easily granted but are rarely rescinded. With permissions increasing 26% after an employee’s first year and 11% annually afterward, they rapidly accumulate for every user. Yet statistics reveal that users only ever access less than 1% of the resources to which they are granted permission. In other words, the vast majority of resources to which users had access held no interest or only very temporary interest to them.
Theoretically, granting permissions should include resource owners (typically a senior person related to the relevant resource) who define the access policy, coupled with IT teams serving as the enforcer. But the trigger for revoking permissions is not well defined, causing permissions to accumulate.
To better understand the implications, Imperva researched the relationship between employment duration and granted permissions within an organization having more than 1,000 employees. Figure 1 shows the strong correlation between employment date and the number of folders each user is permitted to access. On average, permissions increase by 11% annually, with the biggest jump—26%—occurring after a single year of employment.
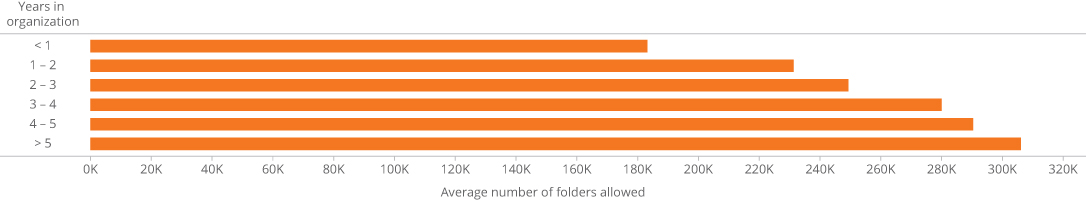
Figure 1: The effect of employment duration on folder permissions
Users do not touch most files to which they have permitted access
In assessing the effectiveness of the traditional permissions model, the research team compared the number of folders opened by the organization’s users in a specific month to the number of folders which they had permission to access. Figure 2 shows that 75% of the users accessed fewer than 36 folders per month; 50% opened fewer than 10 folders monthly. The number of folders opened has a very low correlation with the number of permitted folders. This reveals that typical user behavior is independent of the resource permissions they are granted.
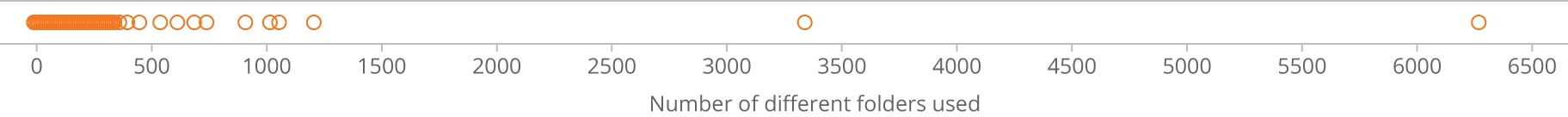
Figure 2: Number of folders used during one month per user
On average, users are permitted access to 370,000 folders, each containing seven files. All users in our case study used less than 1% of their granted permissions (see Figure 3).
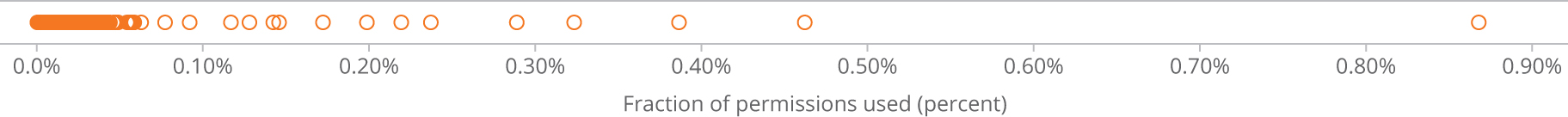
Figure 3: Percentage of permissions used
Enterprise-level file permissions have become increasingly complex
The complexity of managing enterprise-level file permissions on a daily basis makes it increasingly difficult at any given moment for security teams to keep track of who has access to what. Permission inheritance between folder structures further complicates effective oversight of unstructured data. This is one reason why so many data breaches happen as a result of insiders within an organization.
Folder use varies over time. It can be separated into two categories:
- Folders having a continual interest. They are repeatedly used by the user and permission should be granted.
- Folders having a temporary interest. These are used over a specific duration, e.g., those containing information regarding a specific project or financial quarter. More than 99% of all shared folders are in this category.
To reduce risk, static permissions should remain for folders continually in use. But without dynamic permissions management for folders having only temporary interest (where 99% of files are stored), it is unmanageable for IT teams to keep pace with constant permission changes.
Instead, the permissions model should be dynamic and based on user behavior. This serves to relieve IT staff of a near-impossible task while simultaneously protecting an organization’s data assets.
A new approach – Dynamic Peer Groups
Some resources in the file share should never be accessed by certain users. For example, developers do not need access to financial data. Traditional, static access controls can still be used to define resources to which a user or group should never have access. But all other files require a new security approach that is flexible, agile, dynamic and easier to maintain over time.
Backed by research, Imperva has developed an improved file security approach based on how users actually access files. Using highly granular input data collected from Imperva SecureSphere audit logs, coupled with advanced machine learning algorithms, Imperva is able to build dynamic peer groups and determine appropriate permissions based on how users actually access files within an organization. This also allows IT teams to dynamically remove permissions as changes in user interaction with enterprise files occurs over time.
Once virtual peer groups have been established for an organization, suspicious folder access by unauthorized users is identified and flagged, allowing security teams to immediately follow up on critical incidents pertaining to file access. This approach results in less work for IT teams, more appropriate access in today’s dynamic work environment, and a higher level of security.
Learn more about dynamic peer group functionality available in Imperva CounterBreach.
Read the full HII report: “Today’s File Security is So ’80s”.
Other posts in the series
Today’s File Security is So ’80s, Part 2: Detect Suspicious File Access with Dynamic Peer Groups
Today’s File Security is So ’80s, Part 3: Dynamic Peer Groups– 3 Examples from Customer Data
Try Imperva for Free
Protect your business for 30 days on Imperva.















