Protect applications and APIs anywhere
Block threats with confidence
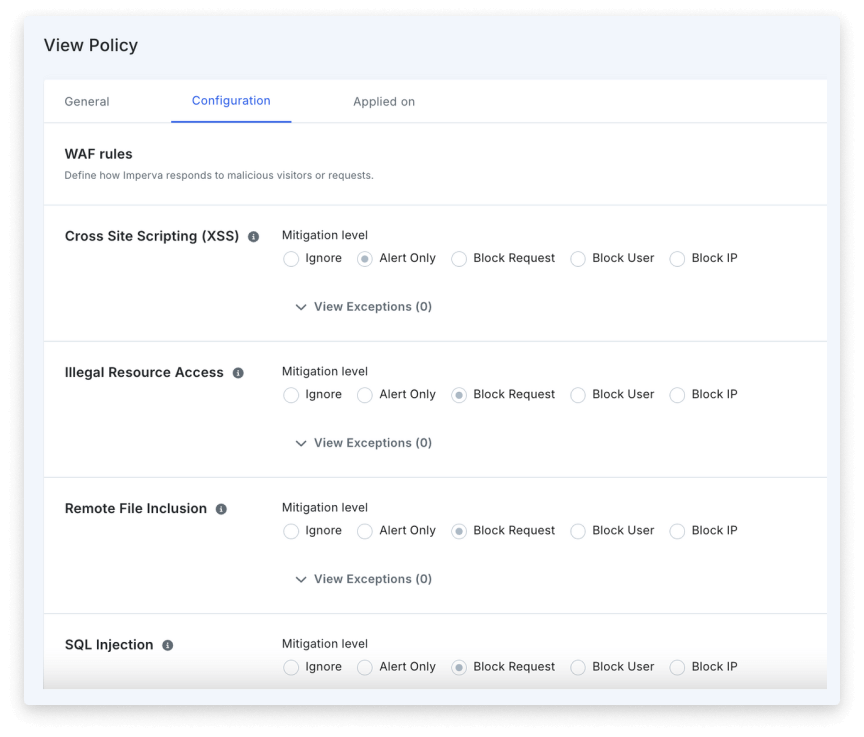
Near-zero false positives and managed rules that are written and tested by the Imperva Threat Research team prior to deployment allow more than 94% of Imperva customers to deploy the Imperva WAF in blocking mode.
Empower security analysts
Machine learning automatically identifies attack patterns and correlates security events into a single incident narrative, reducing alert fatigue and enabling security analysts to quickly identify and focus on critical security incidents.
Protect against data breaches
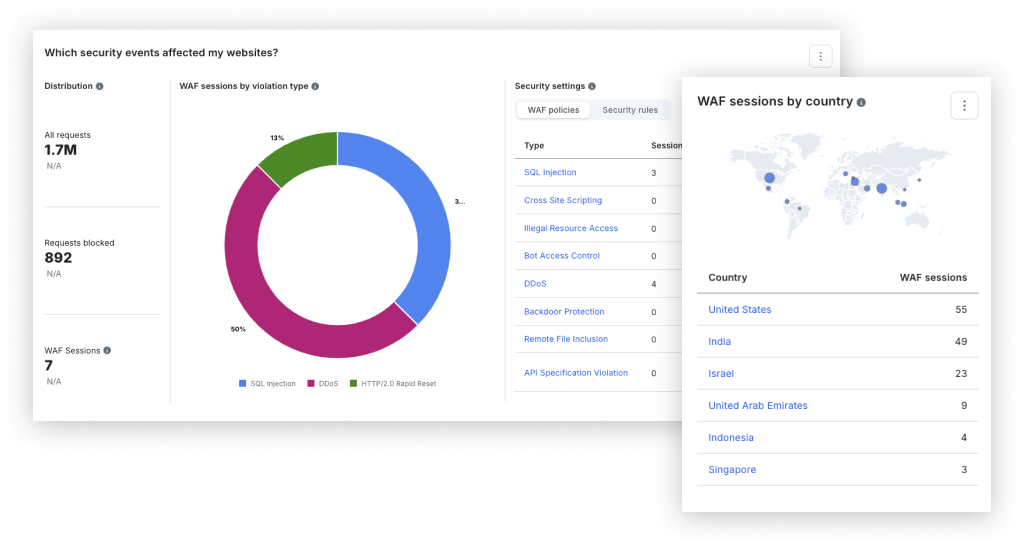
Imperva WAF delivers high security efficacy—effectively blocking threats such as SQL injection, XSS, and other OWASP Top 10 vulnerabilities—safeguarding web applications from potential data breaches and integrity compromises.
Comply with regulations
Organizations must meet strict regulatory standards (GDPR, PII, PCI DSS) to protect sensitive data. Compliance features such as logging, auditing, and access controls ensure adherence to these requirements.
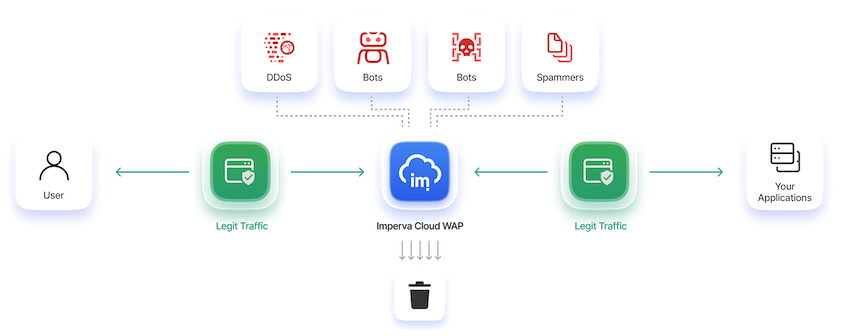
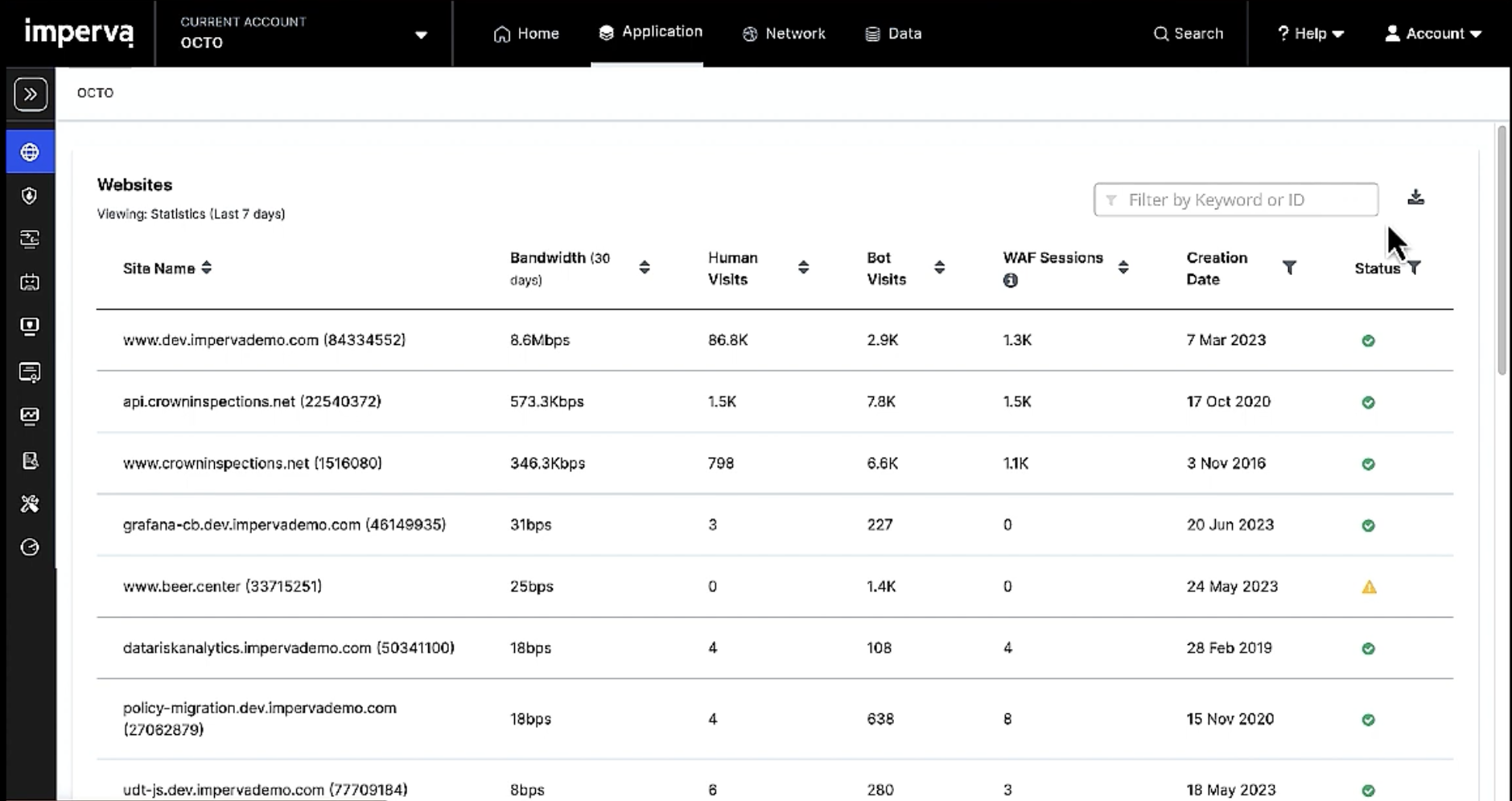
Protect applications anywhere
Flexible deployment options protect applications in public/private cloud, hybrid and on-premises environments.
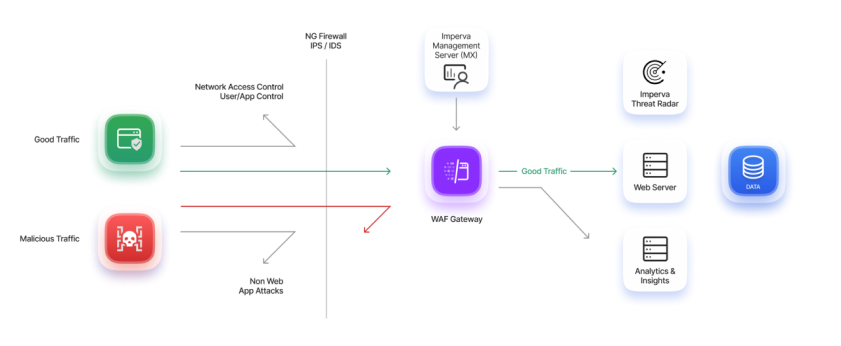
How Imperva WAF works

High security efficacy
False positives can trap organizations in a dilemma between blocking legitimate traffic or indefinitely monitoring threats. Imperva Research Labs delivers unparalleled precision, allowing customers to confidently block threats as the security landscape shifts. Over 90% of our clients use blocking mode, bolstered by automated policies and rapid rule updates. This empowers security teams to safely utilize third-party code while keeping pace with DevOps.

Proactive managed rules
Imperva Threat Research experts continuously identify new threats from common attack vectors like SQL injection and XSS, create and test new rules in production and proactively push them to you, so you don’t have to spend time creating your own custom rules. Regular daily updates and real-time updates for critical threats assure you have the most up-to-date protection, reducing the burden on security teams to research new threats and manually create rules.

Deploy in block mode, in minutes
With out-of-the-box rules that have been tested in production environments, Imperva can be deployed in blocking mode from the start. In fact, over 90% of customers deploy in blocking mode. As a SaaS solution it is easy to deploy and manage all your sites behind one solution and one dashboard. If your team is large or small, Cloud WAF can help protect your applications in public, private, or hybrid cloud infrastructures.

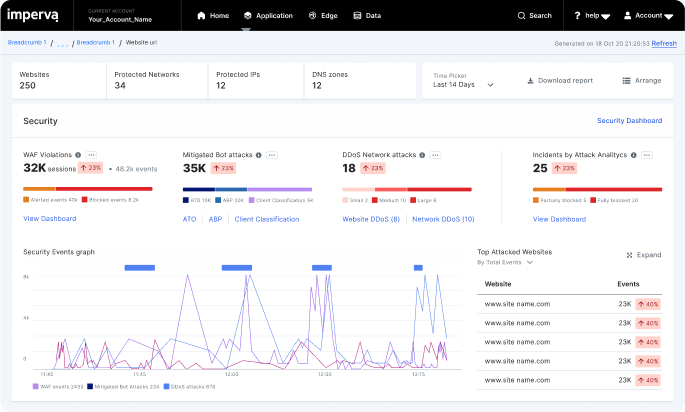
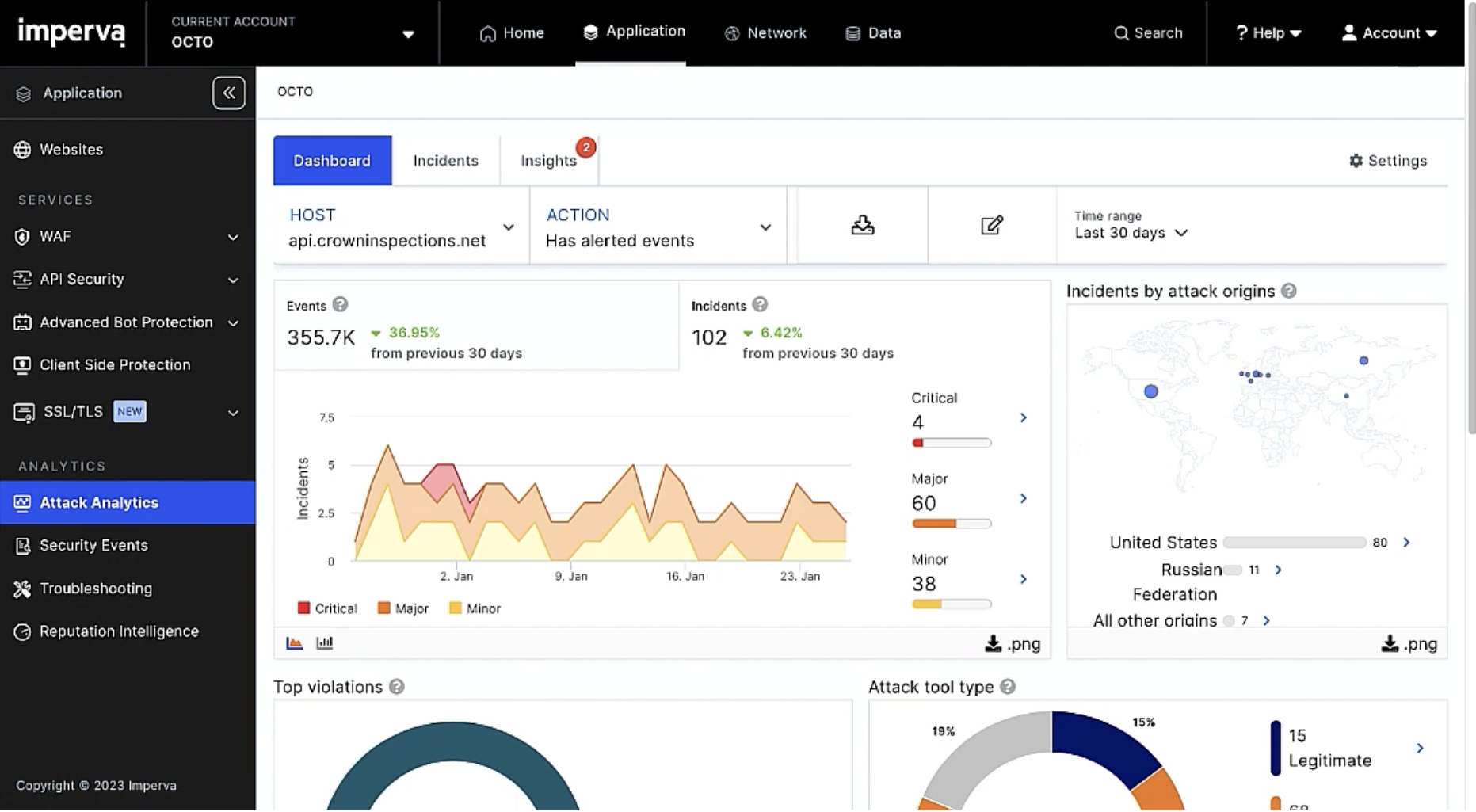
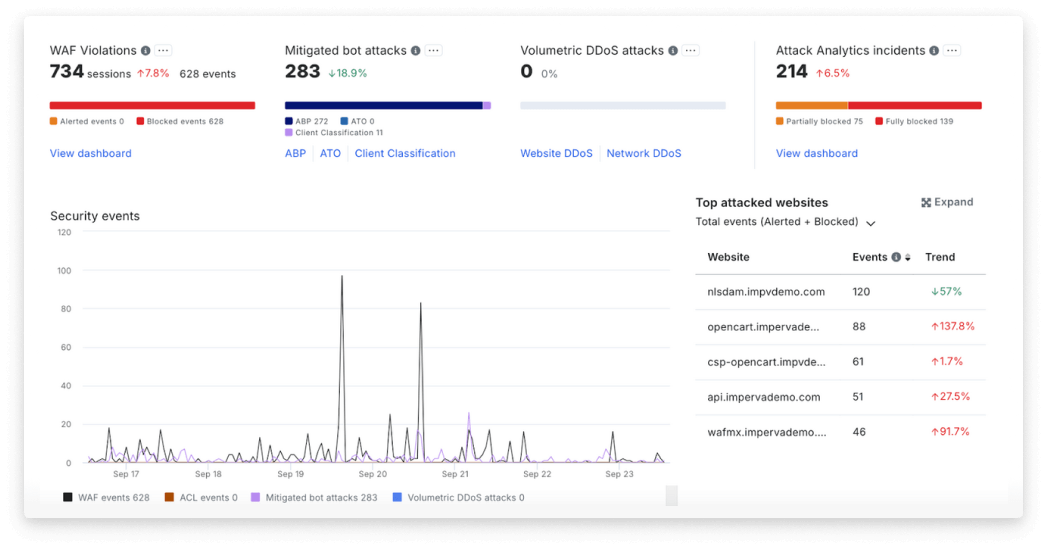
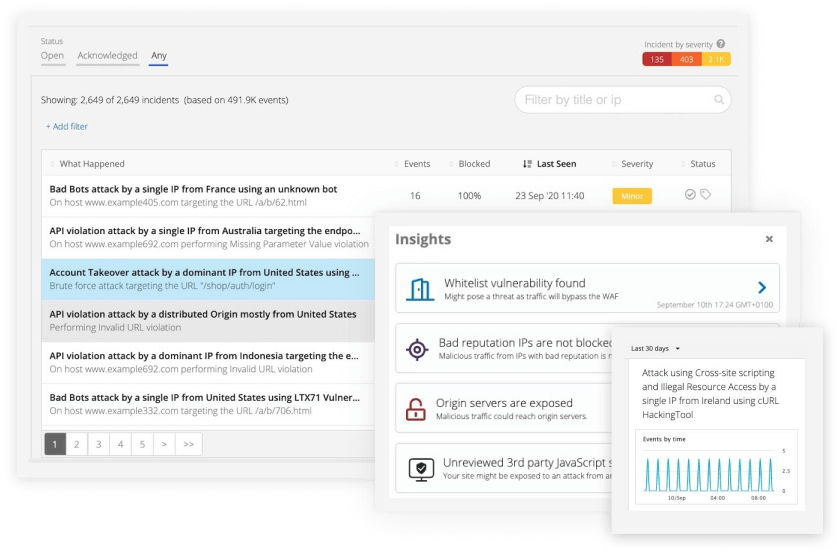
Security incidents with context
Imperva’s Attack Analytics automatically correlates thousands of security alerts into easily digestible narratives. By leveraging advanced machine learning, it provides unified visibility and contextual information about each incident, including attack origin, methods, and severity. This reduces alert fatigue and empowers security teams to respond quickly and accurately to the attacks that matter most.

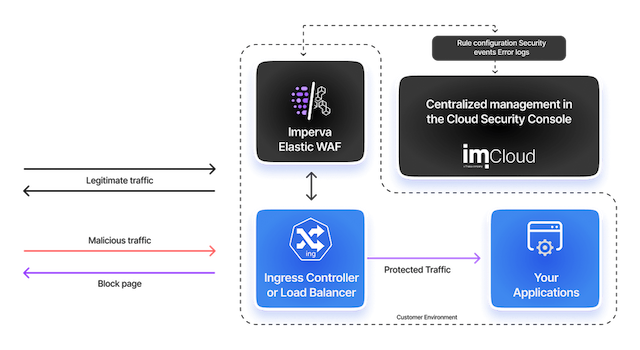
Automated deployment, configuration, and management
Imperva’s Terraform provider automates Cloud WAF deployments. Through a modular design, Imperva’s Terraform module simplifies complex configurations, enabling teams to manage resources across various environments with greater efficiency. This approach enhances security operations and accelerates deployment times by leveraging modern Infrastructure as Code (IaC) practices.

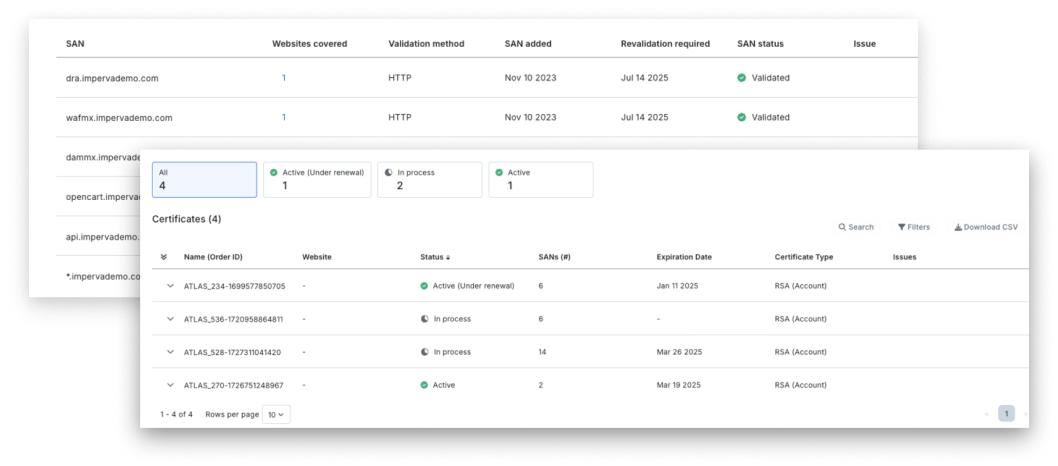
Enterprise SSL management
Full management of SSL connections provides business continuity, security governance, automated certificate renewal and domain validation, and centralized observability. With Imperva enterprise SSL management, you can easily scale your certificates, avoid outages, and enhance security while reducing total cost of ownership.

Protect against malicious file uploads
Upload Scan and Control introduces advanced file‑upload security designed to protect modern web applications from increasingly common malicious uploads. The feature enforces secure upload workflows by validating, scanning, and controlling files before they reach application backends, reducing the risk of malware, exploitation attempts, and data‑exfiltration attacks.
As file‑based threats grow in volume and sophistication, this capability ensures organizations can confidently support user‑generated content while maintaining a strong security posture and operational integrity.