As a web application firewall provider, part of our job at Imperva is to continually monitor for new security vulnerabilities. To do this, we use internal software that collects information from various data sources such as vulnerability databases, newsletters, forums, social media and more, integrating it into a single repository, and assessing each vulnerability’s priority. Having this kind of data puts us in a unique position to provide an analysis of all web applications and database vulnerabilities throughout the year, view trends, and notice significant changes in the security landscape. As we did last year, we took a look back at 2019 to understand the changes and trends in web application and database security over the past year.
This year we slightly changed the vulnerability classification algorithm. The goal was to increase classification accuracy as well as to fit the vulnerabilities to the categories defined by OWASP in the best way possible. Such changes directly affected our research, however, and made it hard to compare to the previous years’ published results. We, therefore, executed a new algorithm on the data from the previous years and conducted the research back to 2016. In this blog post, all the results from 2019 and previous years are aligned based on the new classification algorithm.
It may seem to our readers that, when divided into categories, the sum of the vulnerabilities is greater than the total number of vulnerabilities. The reason for this is the assignment of particular vulnerabilities to multiple categories. For example, we came across a SQL injection vulnerability that could allow an attacker to extract sensitive information from a database and execute arbitrary scripts. In such a case the vulnerability would be related to both ‘Injection’ and ‘Sensitive Data Exposure’ categories.
We often face a situation in which one vulnerability can be exploited in different ways and lead to different results. In such cases, we decided to assign this vulnerability to all the categories in which it may manifest. We believe that such an approach will present the overall picture in the most accurate way.
As in previous years, we continued to see an increase in the amount of vulnerabilities in 2019. The dominant category this year was, by far, injection. When drilling down into the data, a large percentage appeared to be related to Remote Code/Command Execution (RCE). The runner up category was Cross-site scripting (XSS), mainly consisting of Reflected XSS vulnerabilities. We also observed an increase in vulnerabilities in third-party components compared to the previous year, with most of the vulnerabilities related to WordPress plugins. We observed an unexpected decrease in the number of IoT vulnerabilities too, despite the increase in the number of devices in the market.
As expected, the number of vulnerabilities in API (Application Programming Interface), which is still a growing market, continues to grow, although not as fast as we would have expected based on the previous year. In the content management system category, WordPress was not only the most popular platform but also dominated the number of new vulnerabilities in 2019. In the server-side technologies category, PHP – the most prevalent server-side language – was associated with the highest number of vulnerabilities. MySQL appears to be ahead of all others popular databases, in terms of new vulnerabilities discovered in the last year, with 130 (59%) of the total vulnerabilities. The most common vulnerability in databases was Denial-of-Service (DoS). We drew an interesting conclusion from the social media analysis we conducted on twitter.com. The analysis revealed that the CVSS score, which most of the industry relies on in order to prioritize systems patching, doesn’t necessarily correlate with the vulnerability popularity (at least in social media).
2019 vulnerabilities statistics
The first phase in our yearly analysis was to check the number of vulnerabilities published in 2019 in comparison to previous years. Figure 1 shows the number of vulnerabilities on a monthly basis over the last four years. We can see that the overall number of new vulnerabilities in 2019 (20,362) increased by 17.6% compared to 2018 (17,308) and by 44.5% compared to 2017 (14,086). Dividing vulnerabilities according to the CVSS (Common Vulnerability Scoring System), 8% were ranked as Low or None severity, 61% were considered Medium, while 18% and 13% were of High and Critical severity respectively. According to our data, almost half of vulnerabilities (47%) have a public exploit available to hackers. In addition, more than a third (40.2%) of vulnerabilities don’t have an available solution, such as a software upgrade, workaround, or software patch.
Figure 1: Number of vulnerabilities
Vulnerabilities by OWASP category
In Figure 2, you can see vulnerabilities from 2019 split into OWASP top 10 2017 categories.
Figure 2: Vulnerabilities into OWASP categories
Most common vulnerability – injection
The dominant category this year was, by far, injection, with 5,730 (28.1%) of the total vulnerabilities seen in 2019 – a 21% increase on last year. When talking about injection vulnerabilities, the first thing that jumps to mind is SQL injection. When drilling down into the data, however, we saw remote command execution (RCE) emerge as the bigger issue, with 3,869 vulnerabilities (19%), compared to 1,610 vulnerabilities (8%) for SQLi. This was alongside 75 vulnerabilities related to local or remote file inclusion, and 607 vulnerabilities to unsanitized file upload.
Increase in the number of vulnerabilities in third-party components
We observed an increase of 80.6% in vulnerabilities in third-party components in 2019 compared to the previous year. These components contain plugins and packages for major products developed by third parties. Out of 2,081 vulnerabilities, 1,341 (64%) were in WordPress plugins, 354 (17%) in Jenkins plugins, while 88 new vulnerabilities were in NodeJS packages and the rest split among different products and frameworks.
DoS and CSRF
Two major vulnerability categories – Denial-of-Service (DoS) and Cross-Site-Request-Forgery (CSRF) – were out of the OWASP top 10, but still very common. In 2019 we observed 4,130 new DoS vulnerabilities, a decrease of 19.2% on 2018 with 5114 vulnerabilities. Conversely, the number of CSRF vulnerabilities increased by 23.8% from 639 in 2018 to 791 in 2019.
Figure 3: DoS and CSRF vulnerabilities
An unexpected decrease in IoT vulnerabilities
Despite the increase in the number of IoT (Internet of Things) devices and vendors, we observed a decrease of 9% in vulnerabilities on the previous year. Figure 4 shows the number of IoT vulnerabilities between 2016-2019.
Diving into categories we found that DoS was the most common vulnerability for IoT in 2019 with 418 vulnerabilities. The runner up was Remote Code/Command Execution with 398 vulnerabilities, and Broken Authentication (default credentials) was in third place with 157 new vulnerabilities in 2019. From here we can conclude that manufacturers had learned from old mistakes and paid more attention to IoT security.
Figure 4: IoT vulnerabilities
API vulnerabilities – growing, but slowing
API (Application Programming Interface) vulnerabilities are becoming more widespread as time goes by. In accordance with this, as presented in Figure 5, the number of new API vulnerabilities in 2019 (485) increased by 18.9% from 2018. Although API vulnerabilities continued to grow year-over-year, they appear to be slowing – from ~80% yearly growth between 2016 to 2018. One possible explanation is that, since APIs are more popular nowadays, they draw more attention from hackers and security researchers. In turn, organizations spend more time securing their APIs.
Figure 5: API vulnerabilities
Content management systems
The most popular content management system is WordPress which, according to market share statistics cited by BuiltWith, is used by over 33% of all websites, and by 68% of all websites using a known content management system, followed by Drupal and Joomla. Perhaps unsurprisingly, WordPress also registered the highest number of vulnerabilities (1,574) last year and also saw a major increase of 143% from 2018 (Figure 6). The second major increase in the number of vulnerabilities (77%) was in Magento, from 126 in 2018 to 223 in 2019.
Figure 6: Content Management Systems vulnerabilities
According to the WordPress official site, the current number of plugins is 55,173, a slight decrease from 55,271 in 2018. Despite this slower growth in new plugins, the number of WordPress vulnerabilities increased. The explanation for this could either be the code quality of the plugins, or the fact that WordPress is such a popular CMS, motivating more attackers to develop dedicated attack tools and try their luck searching for holes in the code.
Unsurprisingly, 97.2% of WordPress vulnerabilities were related to plugins (see Figure 7), which extend the functionality and features of a website or a blog. Anyone can create a plugin and publish it — WordPress is open-source, easy to manage, and there is no enforcement or proper process that mandates minimum security standards (e.g. code analysis). Hence, WordPress plugins are especially prone to vulnerabilities.
Figure 7: WordPress vulnerabilities
The number of vulnerabilities in WordPress plugins increased by 143% from 629 in 2018 to 1,530 in 2019. The remaining 44 vulnerabilities were related to WordPress core, which also increased by 159% compared to 2018 where there were only 17 vulnerabilities.
The most common WordPress vulnerability by far was XSS with 703 (44.6%) vulnerabilities, while the runner up was CSRF with 254 (16.1%) vulnerabilities this year. In 2018, this position was held by Remote Code Execution.
Figure 8: WordPress vulnerabilities into attack type
Server technologies
PHP is still the most prevalent server-side language used by 37% of the websites. Therefore it’s expected to be associated with the highest number of vulnerabilities. In 2019, 2,652 vulnerabilities in server technologies implemented in PHP were published (see Figure 9), an increase of 12.7% on the number of vulnerabilities in 2018 (2,353). Java language, on which many Apache services are written (HTTP-Server, Tomcat, Struts, etc.) had much less attention this year, with 229 new vulnerabilities compared to 256 in 2018. This year also had far fewer (62.5%) vulnerabilities in applications or packages written in JavaScript for NodeJS. These trends can be explained by a continuous increase of awareness of the developers to the application’s security.
Figure 9: Top Server-Side technology vulnerabilities
Databases
The three most popular databases, with only small gaps between them, were Oracle, MySQL, and Microsoft SQL Server. But, in terms of new vulnerabilities discovered in the last year, MySQL was ahead of all others, with 130 (59%) of the vulnerabilities – this represented an increase of 23.8% on 2018 and 68.8% on 2017. The runner up with regard to the number of new vulnerabilities was SQLite, with 17, followed by Oracle with 16. The popularity of SQLite is growing as it is a lightweight database that’s integrated into Android, iOS and Windows 10 as well as being used in many well-known applications like Chrome and Firefox. The most common vulnerability in Databases was Denial-of-Service (DoS) with 138 vulnerabilities, and the runner up was Broken Access Control with 45. This is due to the fact that, in the case of databases, the attacker’s desire is to get access to data. That said, vulnerabilities such as XXE, XSS or CSRF aren’t just applicable to databases.
Figure 10: Vulnerabilities in DataBases
Social media analysis
Analyzing tweets from twitter.com, we located the top viral vulnerabilities from 2019. The first place with a wide margin – ~4.5K posts and ~77.5K retweets – belonged to (CVE-2019-0708), a remote code execution vulnerability in Remote Desktop Services for Windows (a.k.a BlueKeep). That was disclosed on May 16 and had a public exploit from September 6. According to StatCounter Global Stats reports from December 2019, Windows is the most popular desktop computer operating system with more than 77% market share, which might explain the hype around this vulnerability.
The runner up, with 670 posts and 18.7K retweets, was (CVE-2019-14287) – a bypass of `runas` user restrictions in UNIX sudo shell command. By exploiting this vulnerability, users with low privileges can run processes as a root user. The third place, with 339 posts and ~15K retweets, belonged to (CVE-2019-11932), a remote code execution in WhatsApp Messenger for Android in which the android-gif-drawable library is used to parse a specially crafted GIF image. According to Statista, WhatsApp appears to be a market leader in its sector with 1.6 billion active users.
The most viral vulnerability in web application technologies, with 553 unique posts and ~8.5K retweets, was (CVE-2019-11043), a remote code execution vulnerability in PHP-FPM running on the Nginx server. It wasn’t surprising that the RCE vulnerability in the most popular server-side technology would be highlighted accordingly in social media. Between the exploit’s release on October 22 and the end of the year, we observed more than 730,000 attempted attacks on Imperva’s Cloud WAF customers.
| CVE ID | DESCRIPTION | CVSS SCORE | DATE PUBLISHED |
| CVE-2019-0708 | Microsoft Windows Remote Desktop Services RDP Connection Request Handling Remote Code Execution | 10 | 16/05/2019 |
| CVE-2019-14287 | Sudo Runas Specification ALL Keyword Local Command Execution | 8.8 | 14/10/2019 |
| CVE-2019-11932 | WhatsApp Messenger for Android GIF Image Handling Function Arbitrary Code Execution | 8.8 | 02/10/2019 |
| CVE-2019-1040 | Microsoft Windows MitM NTLM MIC Protection Bypass | 5.9 | 12/06/2019 |
| CVE-2019-11043 | Remote Code Execution Vulnerability In PHP-FPM (The Fastcgi Process Manager) Running On The Nginx Server | 9.8 | 28/10/2019 |
| CVE-2019-11931 | WhatsApp MP4 File Elementary Stream Metadata Handling Remote Stack Buffer Overflow | 7.8 | 14/11/2019 |
| CVE-2019-2215 | Linux Kernel Binder (The Main Inter-Process Communication System In Android) Use-after-free Local Privilege Escalation | 7.8 | 11/10/2019 |
| CVE-2019-8777 | Apple macOS FaceTime Lock Screen Handling Unspecified Local Contact Information Disclosure | 1.2 | 10/10/2019 |
| CVE-2019-11510 | Pulse Connect Secure Web Service HTML5 Access Feature Path Traversal Remote File Disclosure | 10 | 26/04/2019 |
| CVE-2019-2107 | Google Android Media Framework Unspecified File Handling Arbitrary Code Execution | 8.8 | 01/07/2019 |
The interesting conclusion we drew from the analysis of these tweets was that the CVSS score that most of the industry relies on to prioritize systems patching doesn’t necessarily correlate with the vulnerability popularity (at least in social media). While 95% of vulnerabilities are mentioned in fewer than 40 tweets, there are some “superstars” that feature in thousands of posts and reposts. In Figure 12 you can see the distribution of vulnerabilities by CVSS score and their virality in social media. While it’s not hard to notice a trend for more viral vulnerabilities among high CVSS scores, there are dozens of vulnerabilities in the Medium severity range that also reached high popularity in social media.
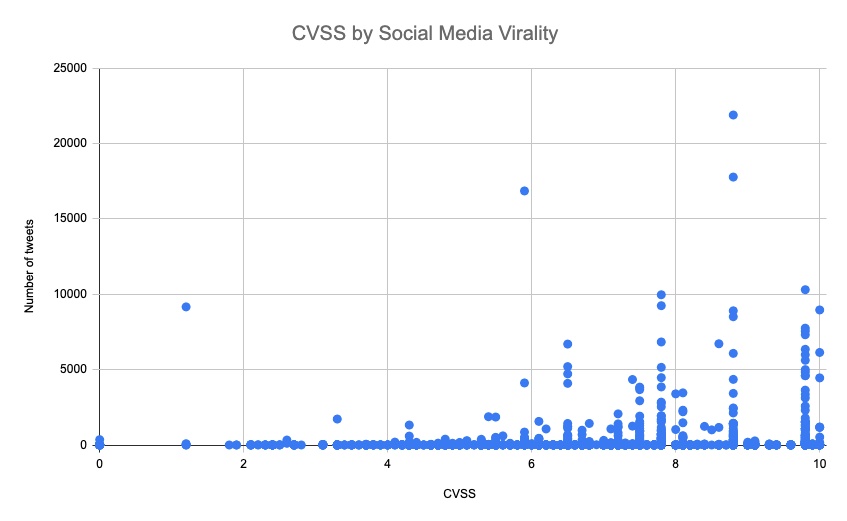
Figure 12: CVSS by Social Media Virality
Predictions for 2020
As a security vendor, we’re often asked for our thoughts on what the future might hold. Here, then, are our vulnerability predictions for 2020:
- Old faithful Injection and Cross-Site-Scripting vulnerabilities will remain at the top of the chart. Despite the awareness of these vulnerabilities and the number of tools that check code for their presence, their number won’t decrease in 2020. The reason for this is the direct impact of the exploitation of these vulnerabilities, as well as – in most cases – the lack of preconditions required to exploit them.
- The number of vulnerabilities in third-parties will continue to grow. Major platforms and frameworks rely on third-party plugins. WordPress has over 55K plugins, the NPM registry has almost 450K packages for NodeJS, and PyPI has over 210K packages for Python. In addition, there are also main package registries for Java and Ruby-based projects. As the community continues to grow, and without code standards or restrictions to publish a plugin or a package, they remain the weakest point in the application, making them the sweet spot for attackers.
- The release of the OWASP top 10 for API that standardizes the main threats in API will, on one hand, increase the awareness of security among developers. On the other hand, however, it will focus attackers and increase their attention on API vulnerabilities. Based on the previous year’s results, we expect to see constant growth, but at the same time a decrease in the growth rate.
- The security awareness among IoT vendors is still growing, so they will invest more in securing their devices. This will be reflected in the number of new vulnerabilities in IoT devices.
How to protect your apps and data
One of the best solutions for protecting against web application and database vulnerabilities is to deploy a Web Application Firewall (WAF) and Data Monitoring & Protection. The solutions may be either on-premise, in the cloud, or a combination of both depending on your needs, infrastructure, and more. As organizations move more of their apps and data to the cloud, it’s important to think through your security requirements. A solution supported by a dedicated security team is one to add to your selection criteria. Security teams can push timely security updates in order to properly defend your assets.
Try Imperva for Free
Protect your business for 30 days on Imperva.
















